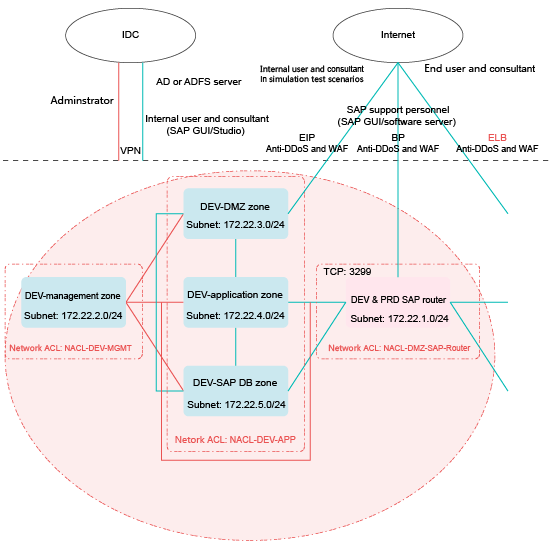
O&M Border
The management zone does not need to communicate with the public network. Therefore, you only need to configure access control policies between the management zone and IDCs.
Security Policies
As shown in Figure 1, network ACL NACL-DEV-MGMT is associated with the subnet for the management zone in the development and test environment. You can configure inbound rules of network ACL NACL-DEV-MGMT (for administrators) to allow access from IDCs to management ports (such as ports 22 and 3389) of hosts in the management zone.

IP addresses and ports in this section are only used as examples. You can also configure access control policies associated with end users for the administrator so that the administrator can access service ports in the development and test environment.
|
Rule |
Source IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
For the administrator |
A subnet (subnet a) in an IDC |
TCP |
22 |
Allow |
Allows the administrator of a subnet (subnet a) in an IDC to access VMs in the management zone in the development and test environment. |
|
For the administrator |
A subnet (subnet a) in an IDC |
TCP |
3389 |
Allow |
Allows the administrator of a subnet (subnet a) in an IDC to access VMs in the management zone in the development and test environment. |
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all inbound traffic that is not processed based on preset rules. |
|
Rule |
Destination IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
1 |
0.0.0.0/0 |
Any |
Any |
Allow |
Allows all outbound traffic from the management zone. |
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all outbound traffic that is not processed based on preset rules. |
For security group rule configuration, see the related content in Network Isolation and Access Control.
Security Services
With enterprise security practices considered, bastion hosts are used to free O&M and operations personnel from using system usernames and passwords (usernames and passwords for all system components are stored in the bastion host system). The rights of O&M operations performed through bastion hosts are controlled. The rights of high-risk operations are limited. The whole process of O&M operations is recorded and audited so that each event is monitorable and traceable. Bastion hosts are deployed in the form of ECSs in the subnet for the management zone.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot