Managing SaaS Assets
KooGallery provides a unified asset management center for you to add, modify, delete, and perform other operations on assets.
SaaS assets you added will be used for subsequent commercial SaaS release. Before releasing SaaS assets, ensure that you have developed and debugged related interfaces and that your SaaS websites (including the service frontend and management backend portal) do not have high-risk vulnerabilities such as XSS, SQL injection, CSRF, XXE injection, OS injection, cross-directory access, file upload vulnerabilities, sensitive information leakage, URL redirection leakage, TLS configuration defects, and web page Trojan horses.
Adding a SaaS Asset
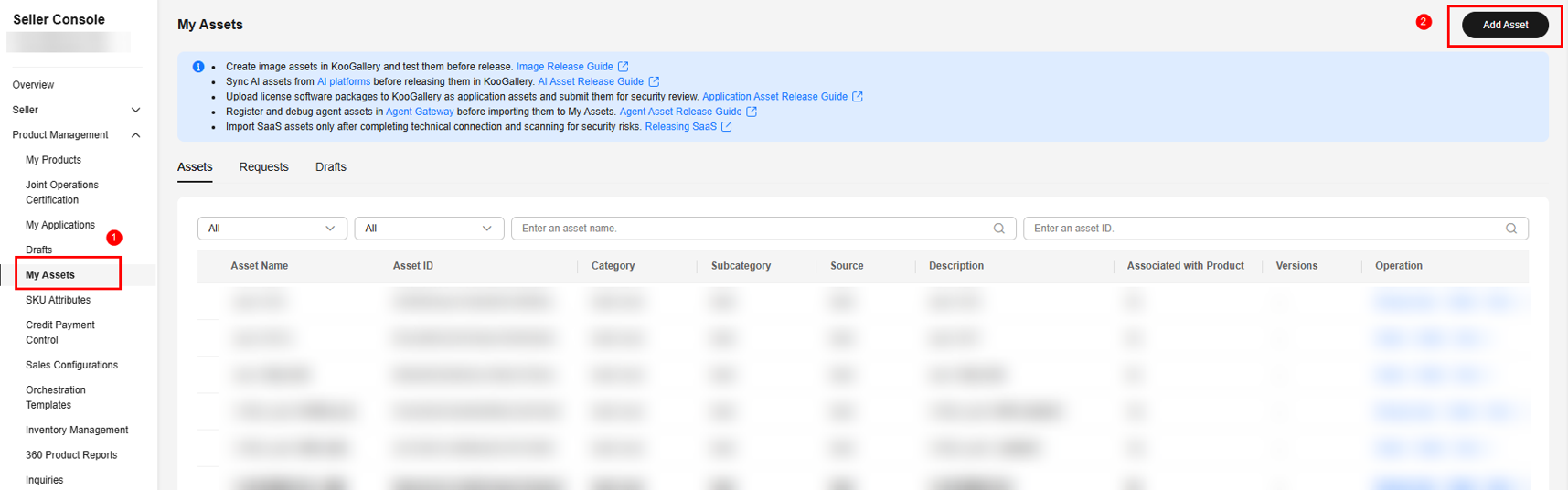
- Go to the Seller Console.
- In the navigation pane, choose Product Management > My Assets. On the displayed page, click Add Asset in the upper right corner.
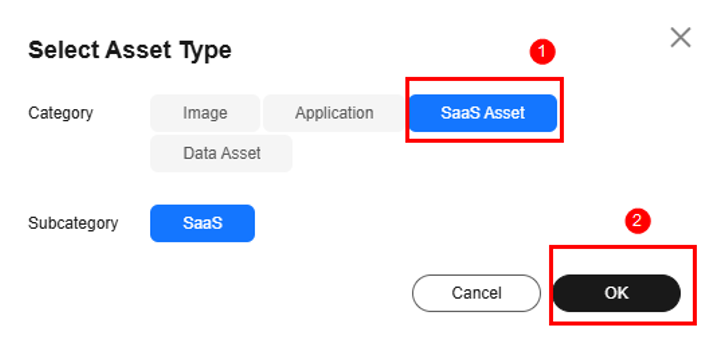
- In the Select Asset Type dialog box, set Category to SaaS Asset and click OK.
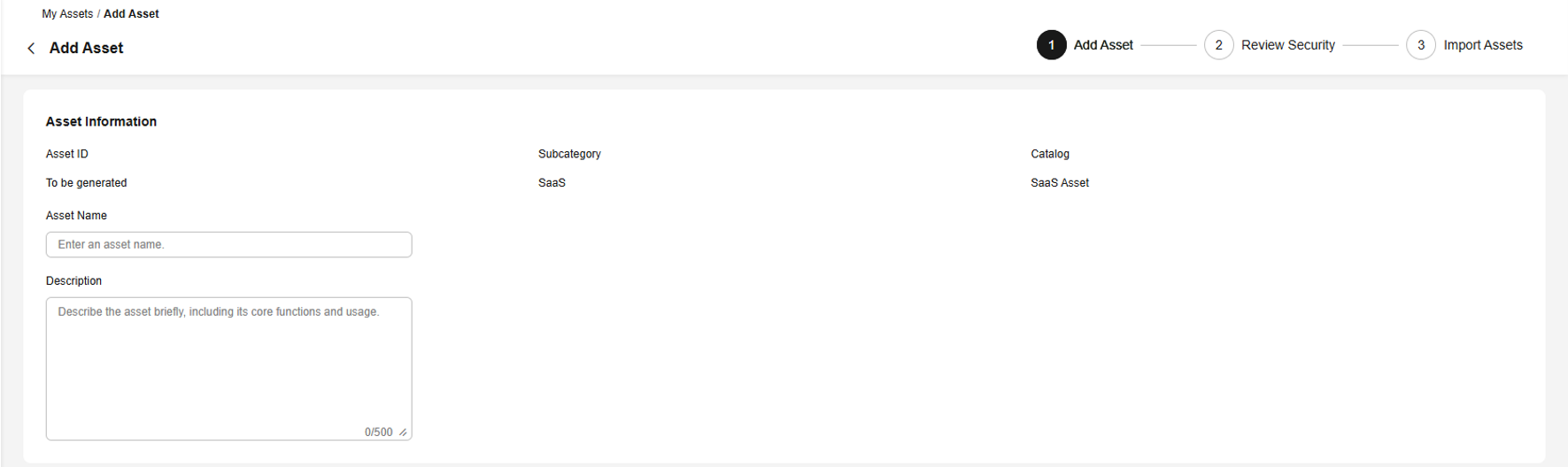
- Enter the asset information. It is recommended that the asset name be the same as the software name.
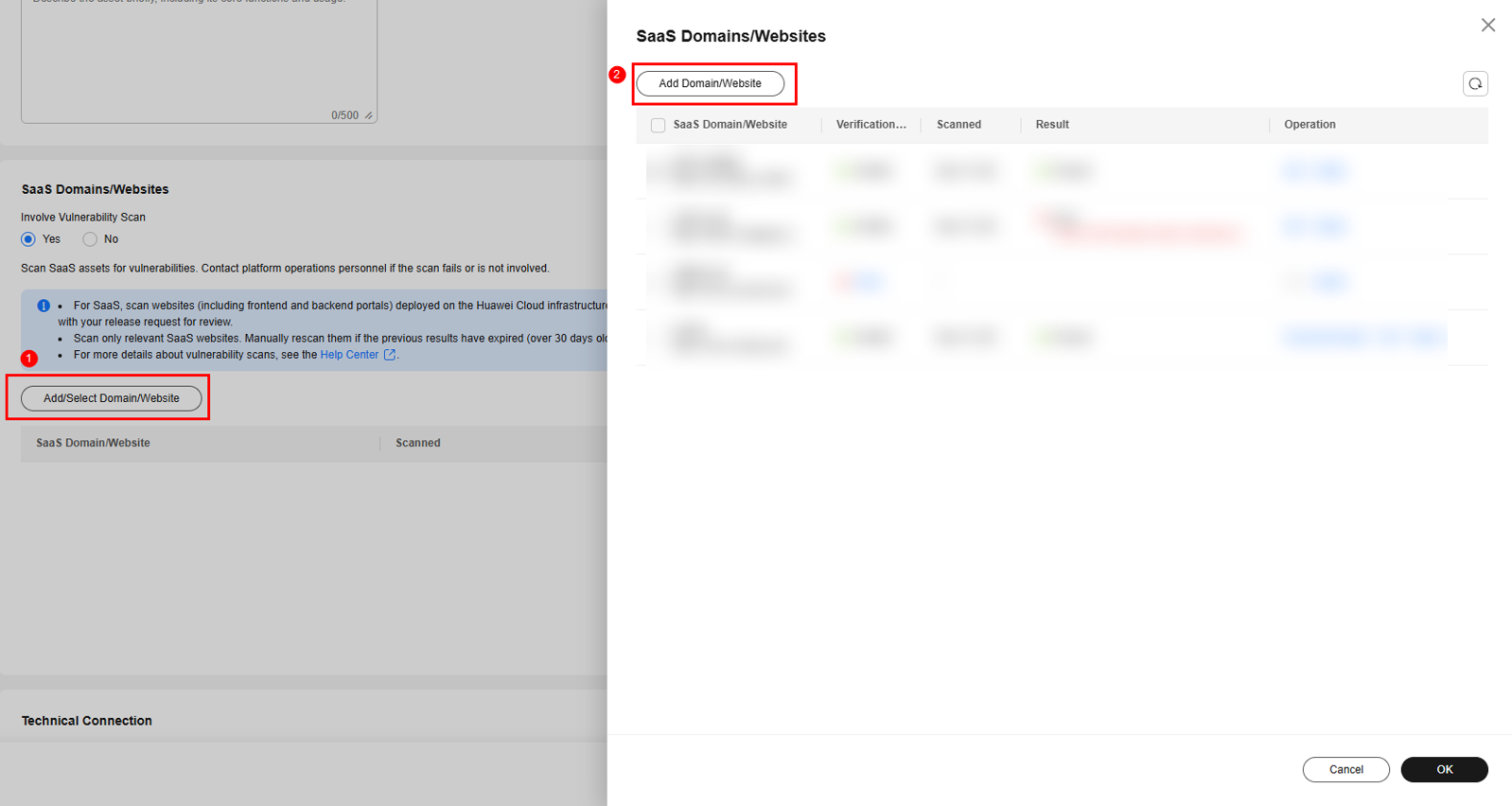
- Add a SaaS domain name or website.
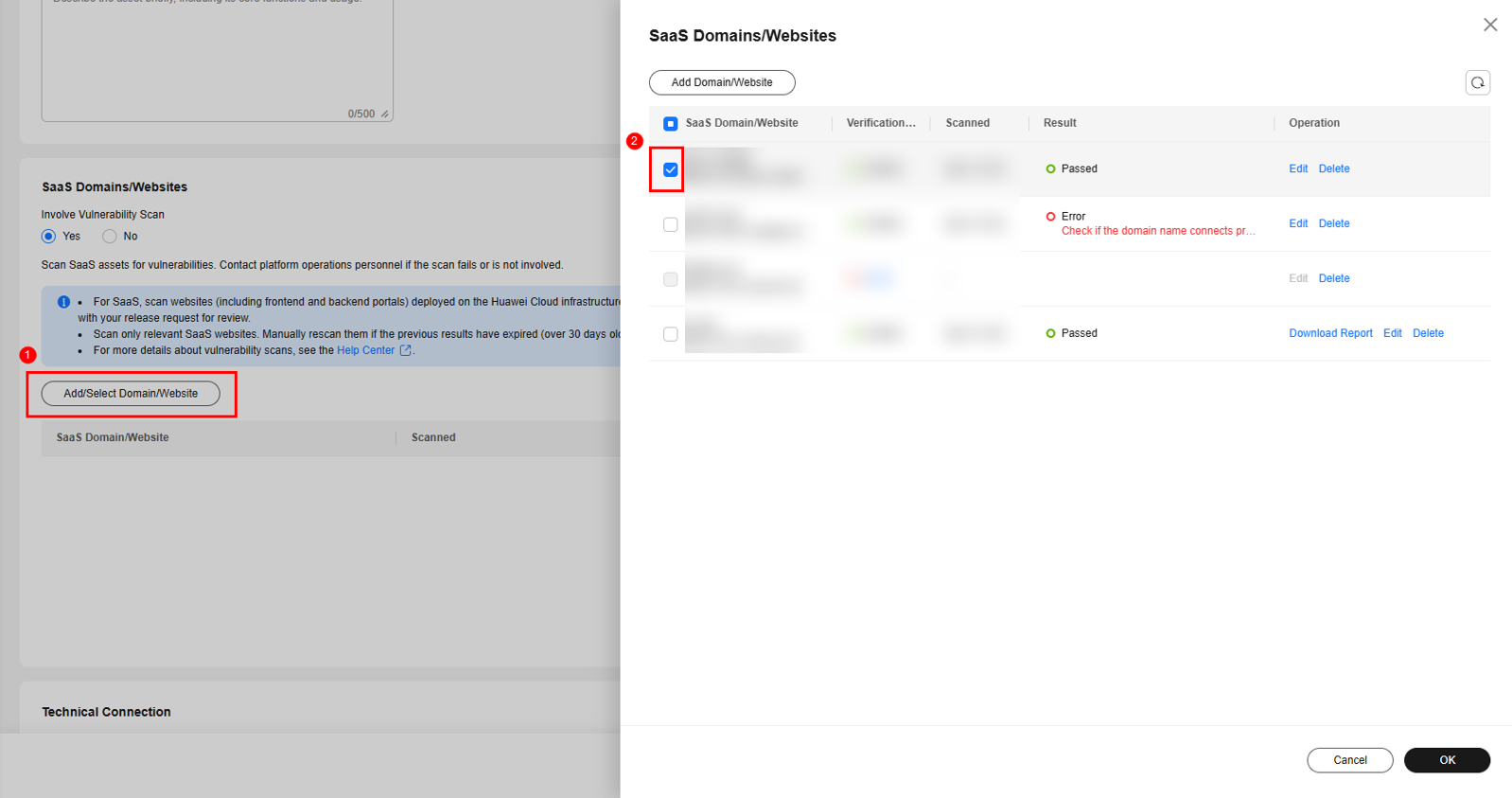
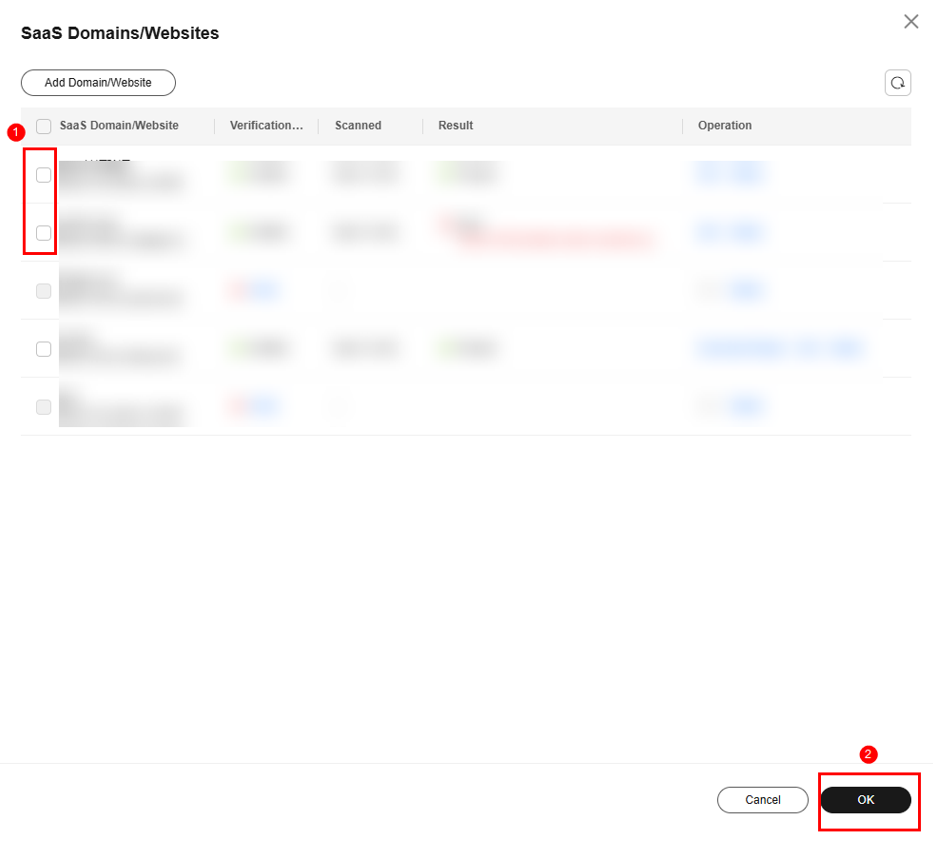
- Select the SaaS domain name that has passed the security scan.
- If a domain name of SaaS to release has passed the security scan, perform the following steps:
- Click Add Domain/Website.
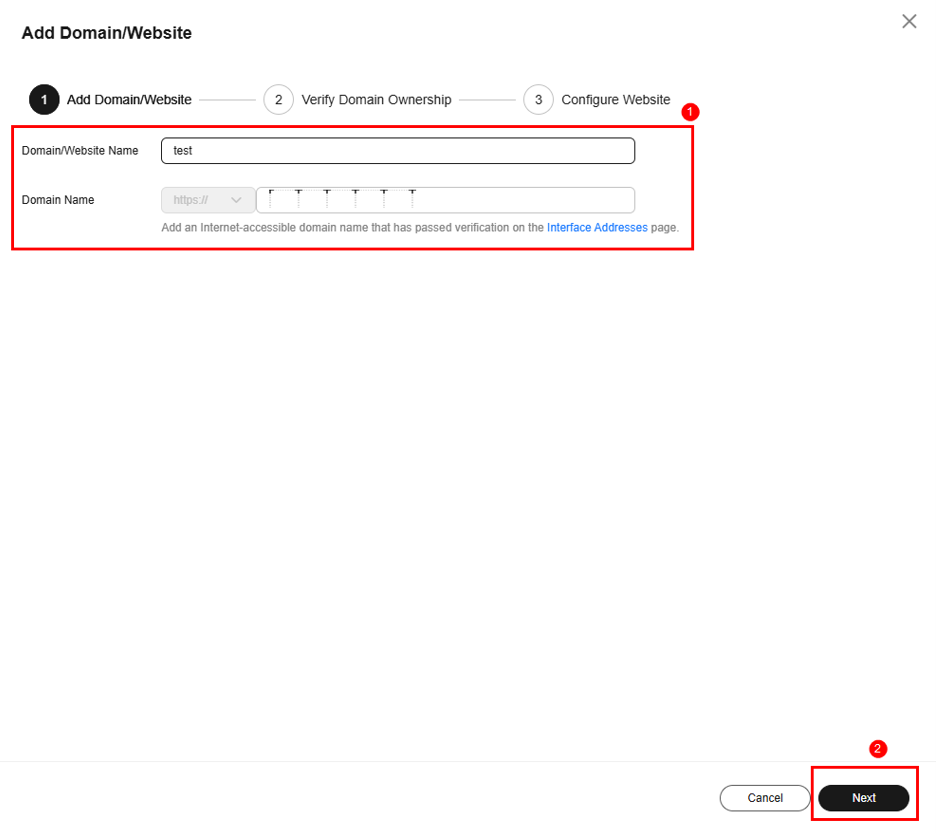
- Enter basic details and click Next.
- Verify the domain name ownership, select I have read and agree to the HUAWEI CLOUD Vulnerability Scan Service Agreement, and click Verify.
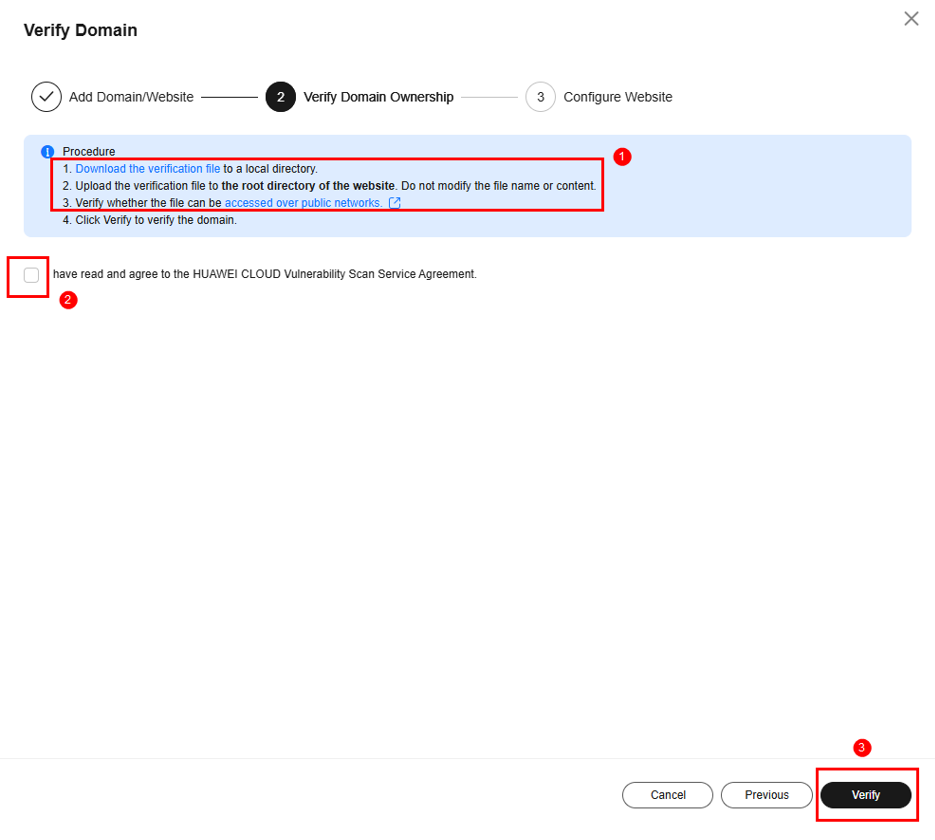
- The scanned SaaS domain name should match the one requested by customers.
- Do not modify the content of the downloaded verification file. Save the file to the root directory of the domain name or website.
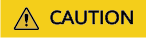
- Enter the website settings, select a login mode (username/password or cookies), and click Confirm.
- After the SaaS domain name is added, select it.
- Perform self-check and click Complete.
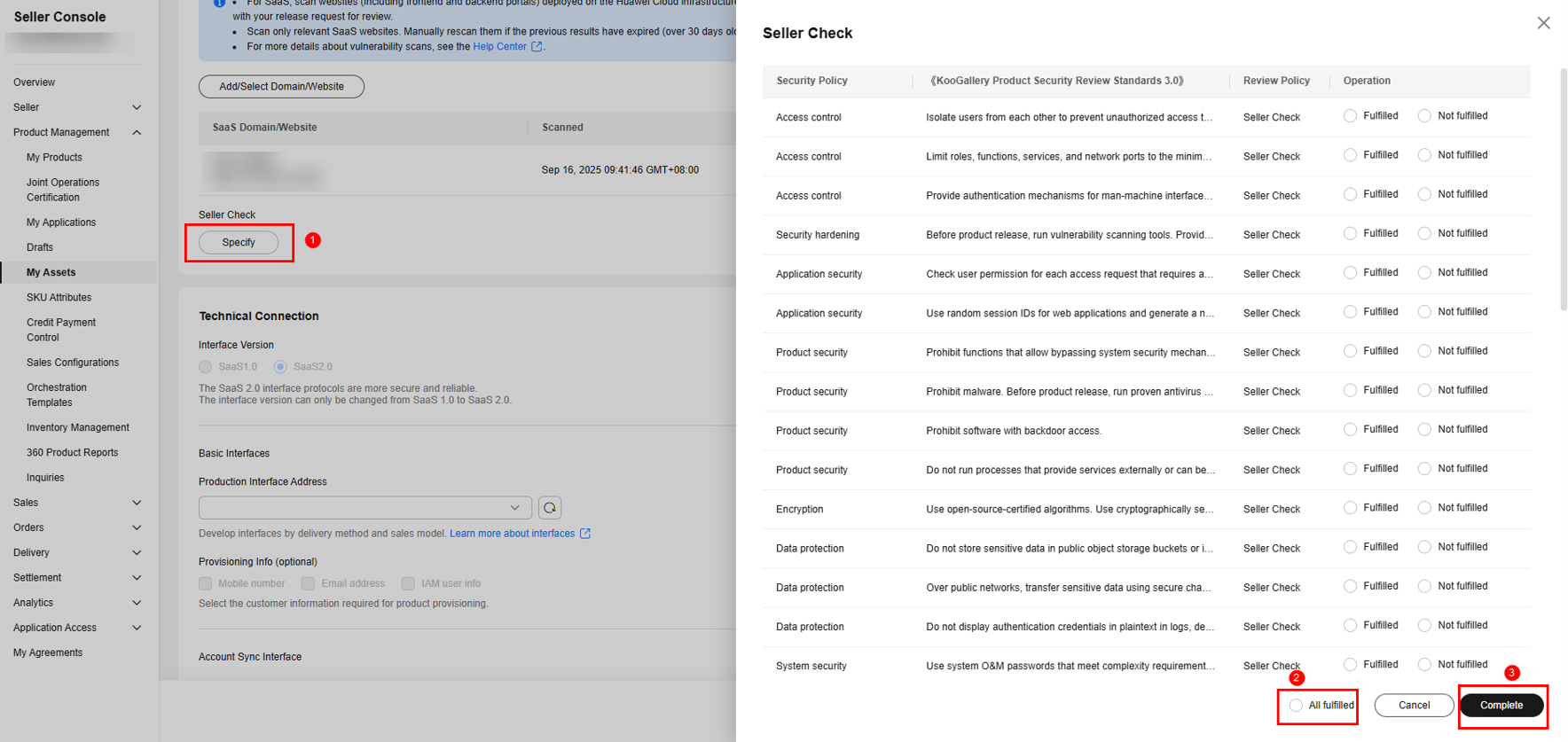
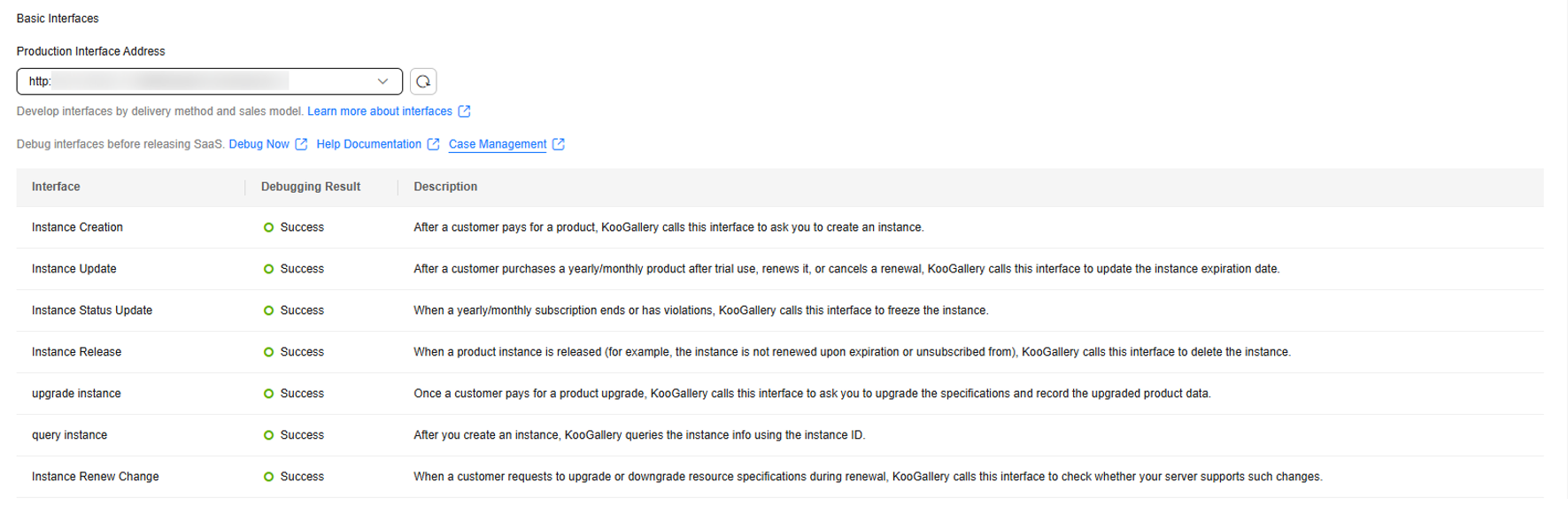
- Add technical connection information. If no interface address is available, develop interfaces by referring to SaaS Access Guide V2.0 (New Products).
- Basic interfaces: required for both common and joint operations products.
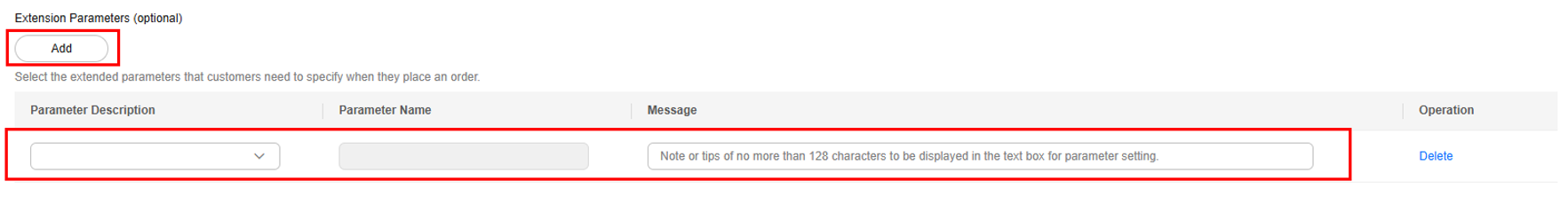
- Extension Parameters (optional): Customers need to specify them when placing an order. Select parameters as required.
- Provisioning Info (optional): Select the sensitive customer information (mobile number, email address, or Huawei Cloud IAM user name) required for SaaS interfaces to enable the product.


From October 25, 2025, new SaaS assets no longer support the transfer of Huawei Cloud IAM user information through APIs. The existing SaaS assets are not affected.
- Click Submit for Review. After the asset is submitted, you can check the asset review status.
Checking the Asset Review Status
- Approved: You can release the asset as a SaaS product.
- Scanning: Wait for the system to check whether it complies with KooGallery Product Security Review Standards 3.0. If you have any questions, submit a service ticket to contact the customer service.
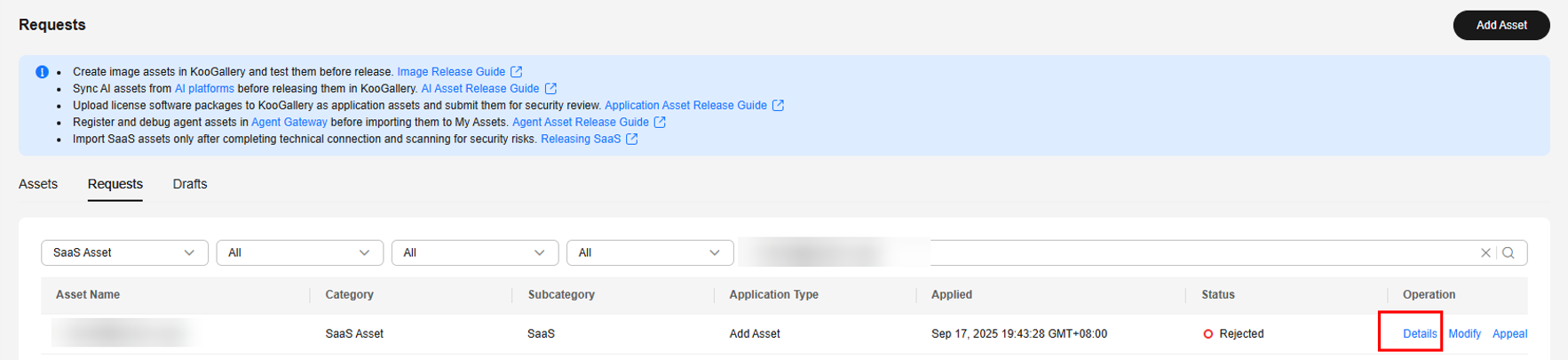
- Rejected: Click Details. On the asset details page, scroll down to SaaS Domains/Websites and click the security scan report to download and view it.
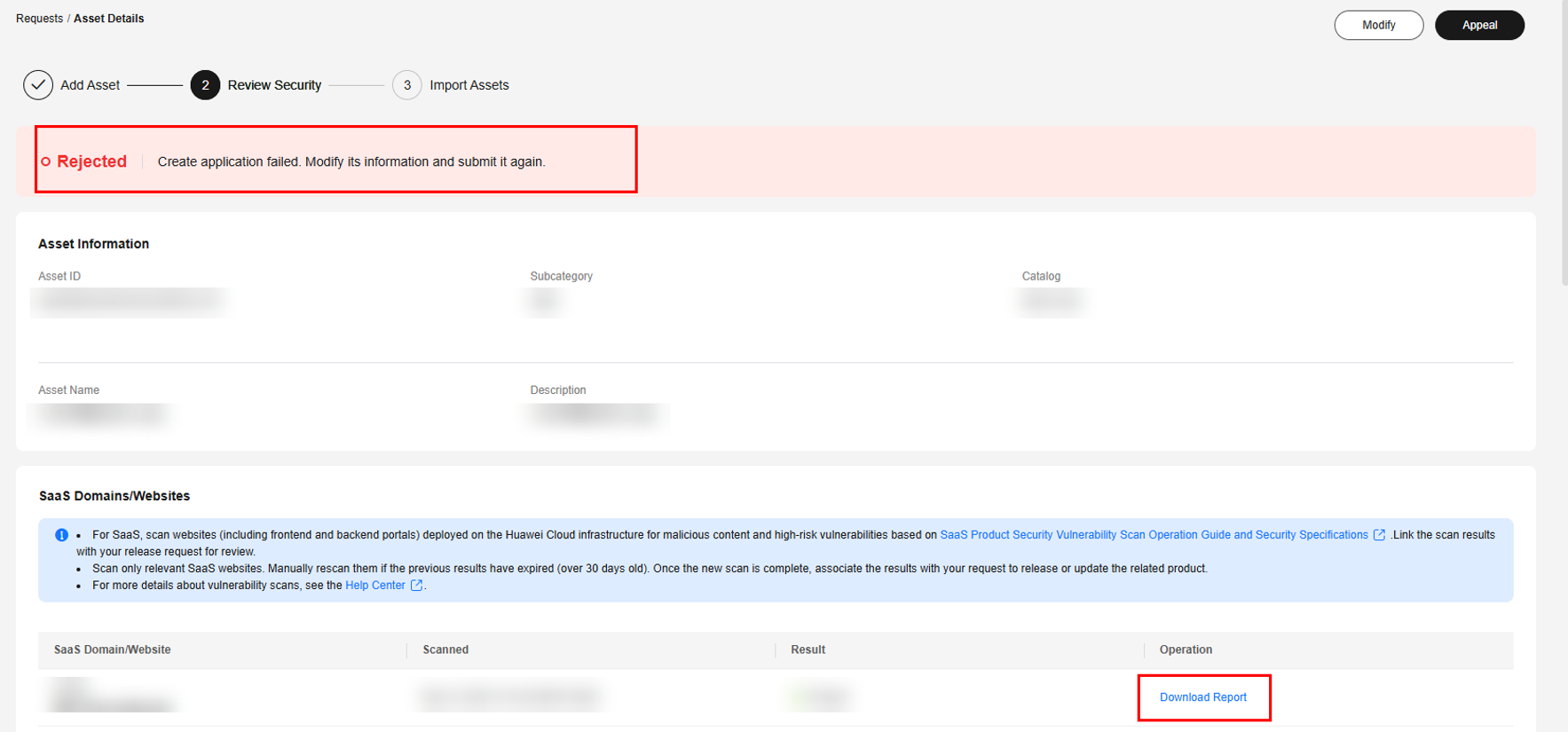
- If the security issues have been rectified, click Modify, and submit the modified asset for review again.
- If there are false positives, click Appeal to file an appeal.
- Enter the false positive conclusion in columns F, G, and H in the downloaded Security Scanning Report and save it.
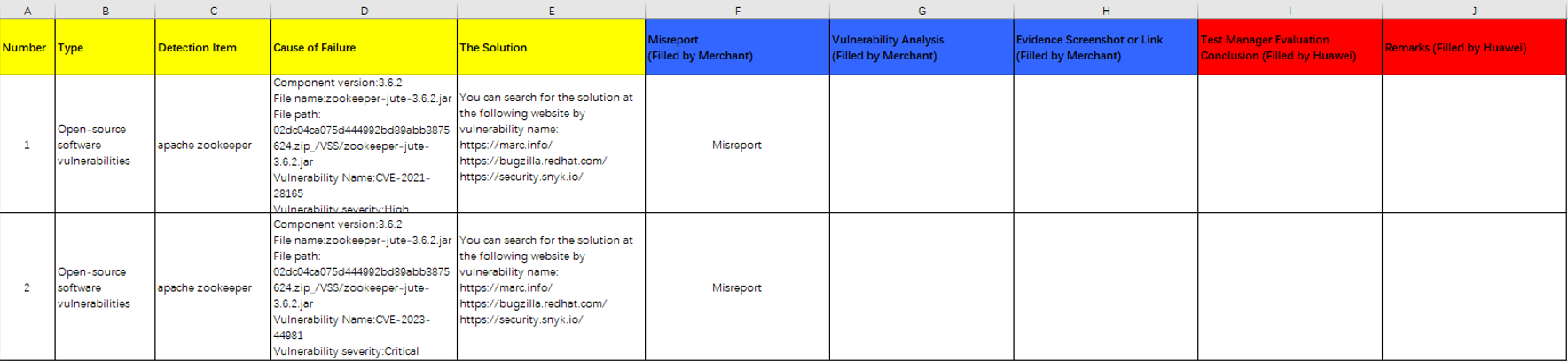
- Click Upload Proof, upload the saved file, and click Submit in the lower right corner. The asset status changes to Reviewing. KooGallery will review the asset within three working days.

- Enter the false positive conclusion in columns F, G, and H in the downloaded Security Scanning Report and save it.
Modifying an Asset
- On the Assets > My Assets tab, search for the target asset and choose More > Modify in the Operation column.
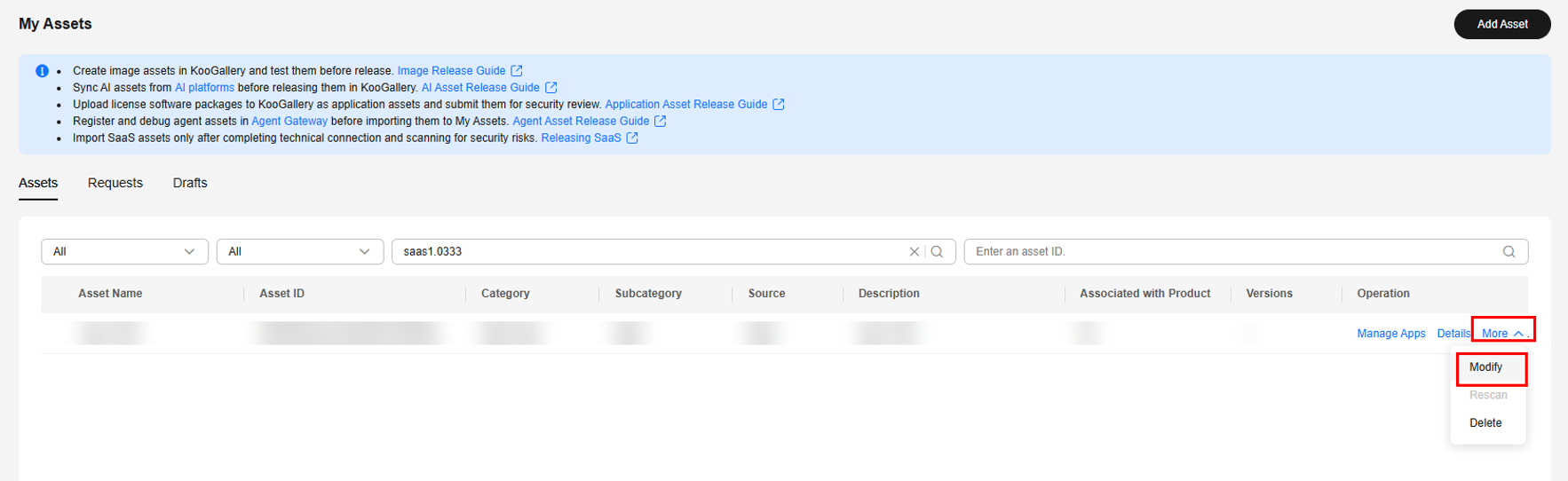
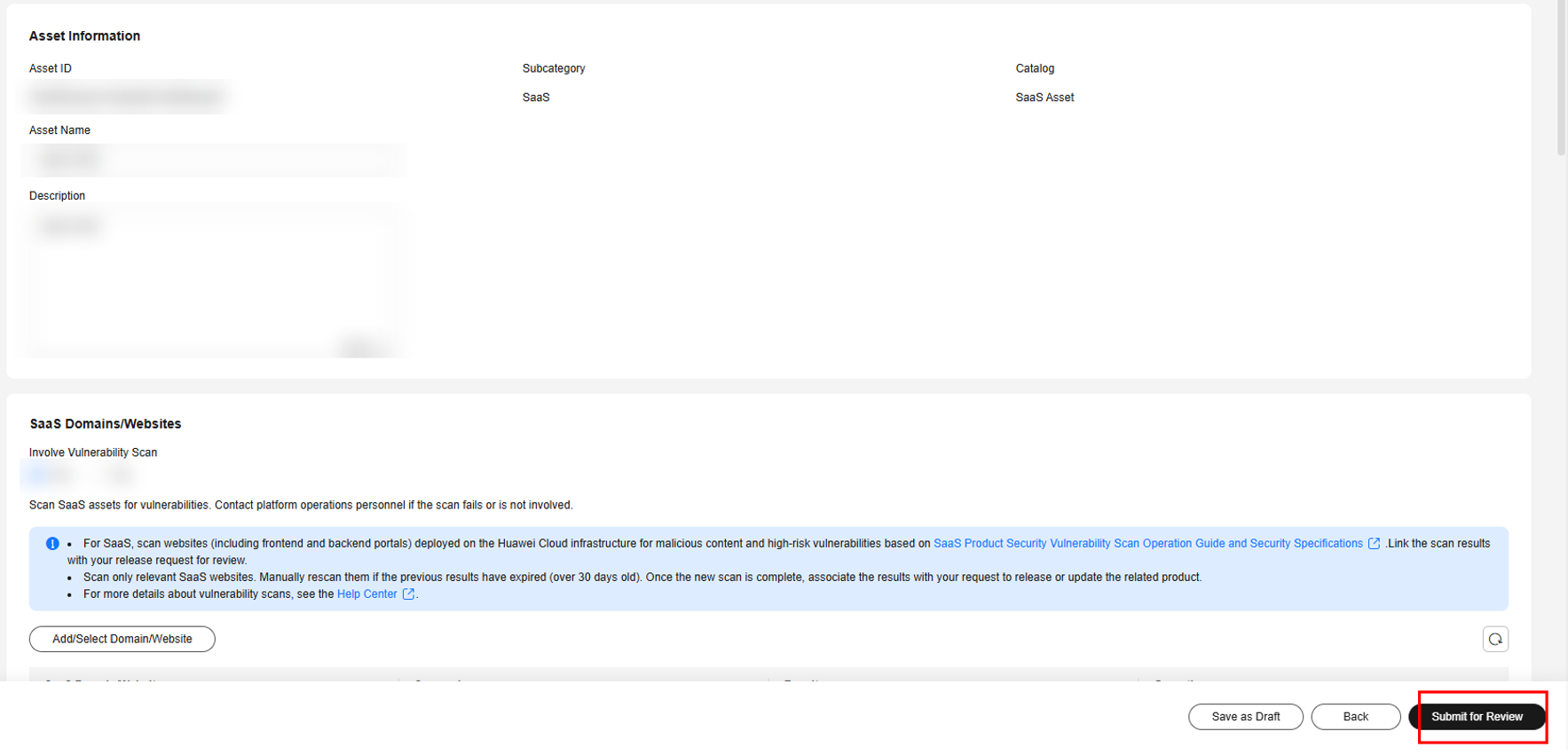
- On the Modify Asset page, select the information to be changed and click Submit for Review.

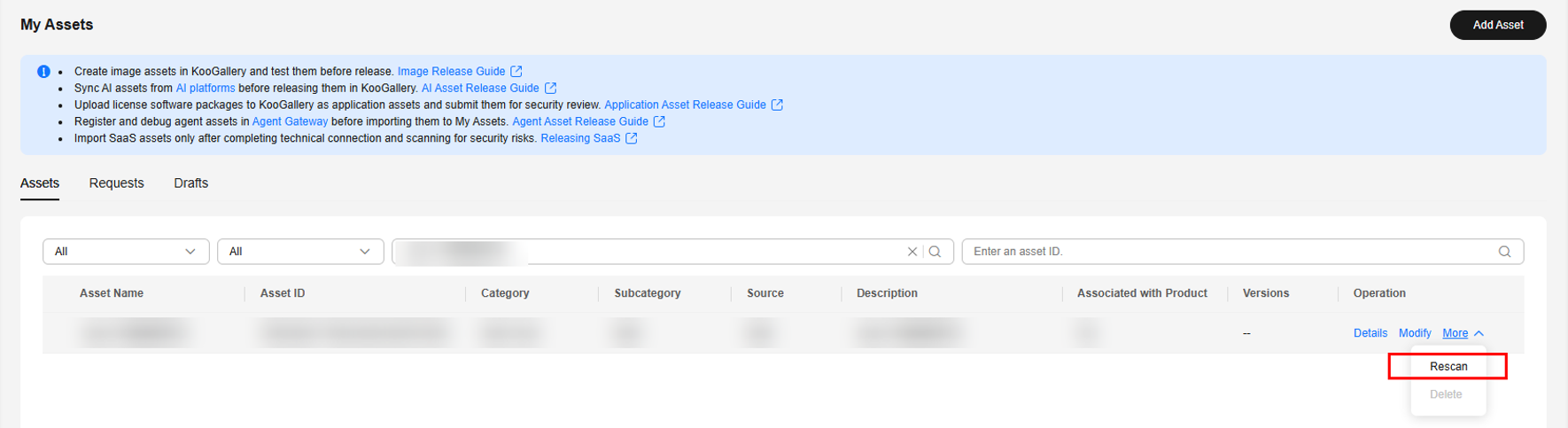
The scan results of a SaaS asset are valid only for 30 days. If they expire, you need to rescan the asset.
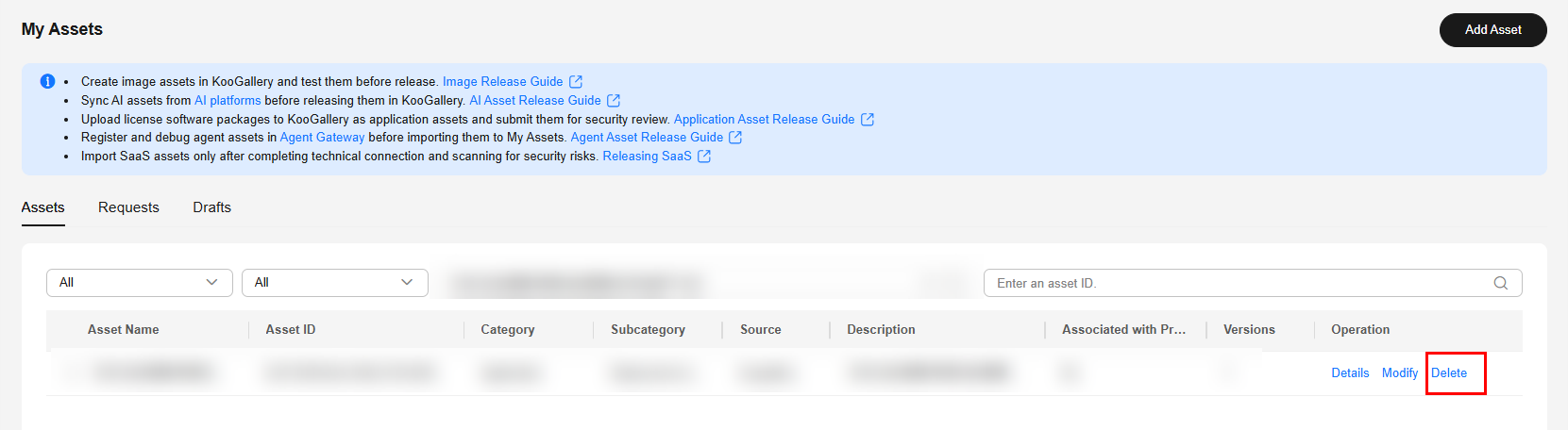
Deleting an Asset
You can delete assets that are not associated with products and those in the draft box.
On the Assets page, click Delete in the Operation column of the asset to be deleted and confirm the deletion.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot