Configuring an Access Control Policy
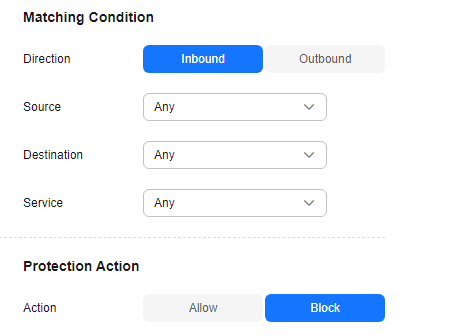
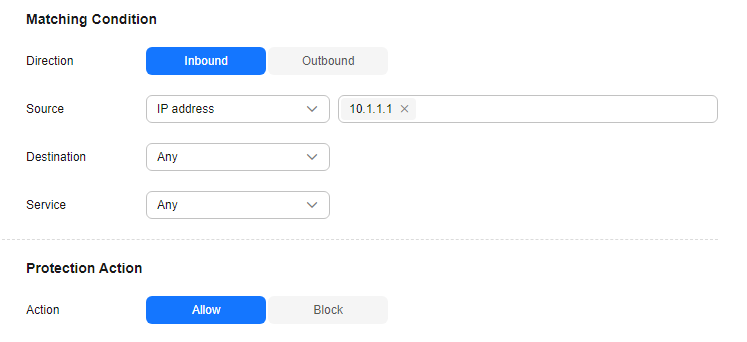
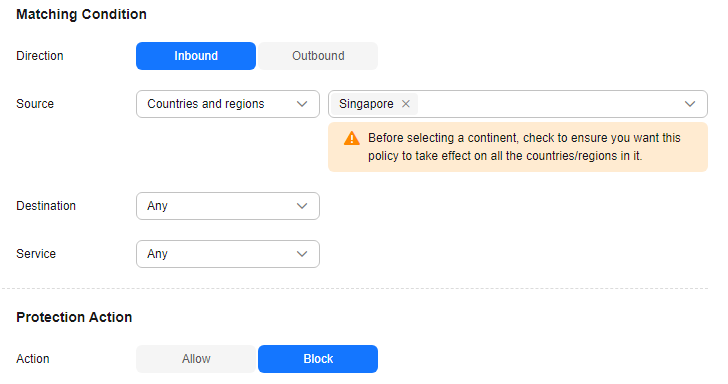
The default status of an access control policy is Allow. Configure a proper access control policy for fine-grained management and control, preventing the spread of internal threats and enhancing security. For details about how to configure an access control policy, see Adding an Internet Boundary Protection Rule. For details about how to block all access and allow only certain traffic, see Configuration Example - Allowing the Inbound Traffic from a Specified IP Address. For details about how to block the access traffic of a region, see Configuration Example - Blocking Access from a Region.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot