Checking the Security Protection Dashboard
Context
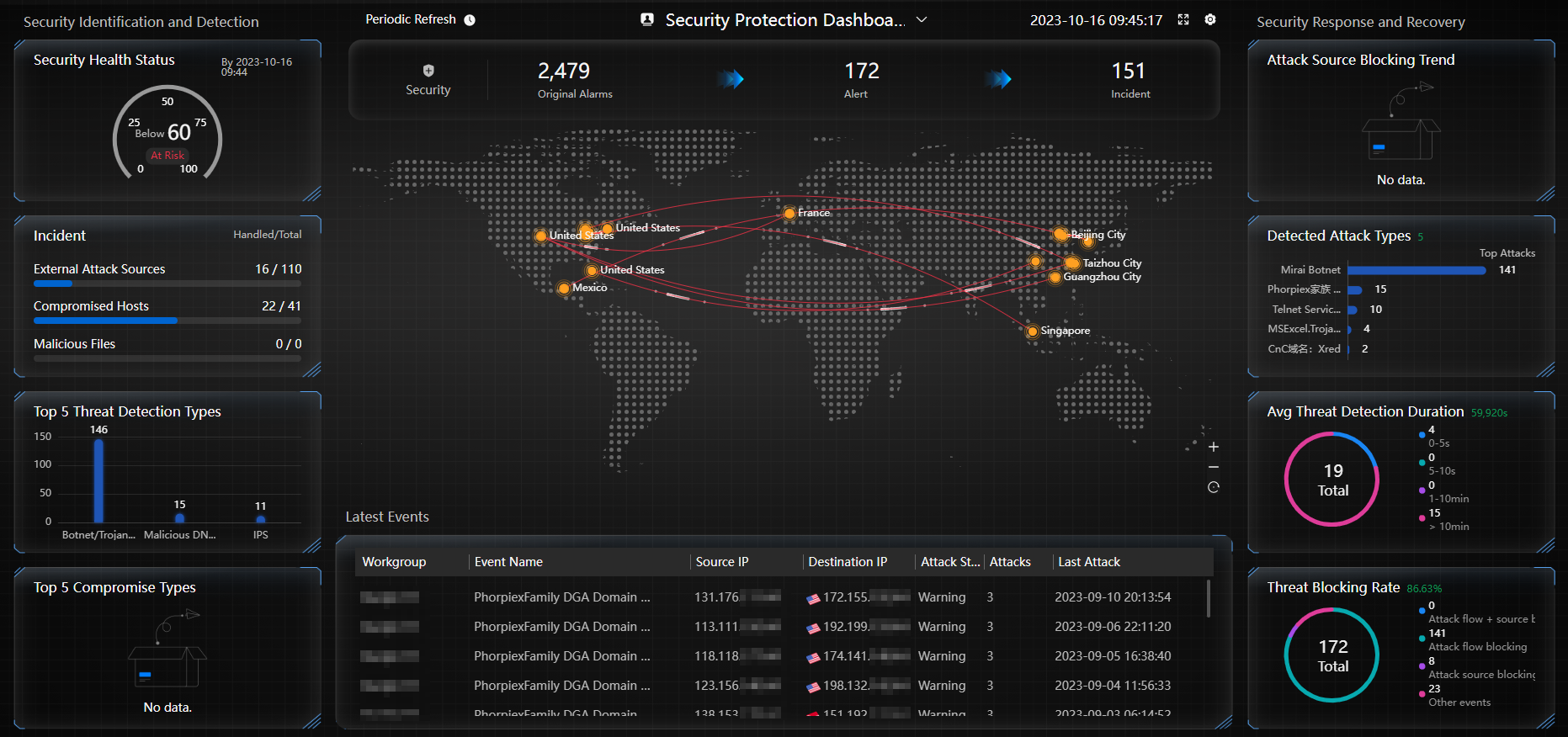
The security protection dashboard displays three parts: security identification and detection, security response and recovery, and latest events. The three parts include top 5 compromise types, top 5 threat types, threat events, system health status, average threat detection duration, threat blocking rate, detected attack types, threat IP blocking trend, and latest events.
The security protection dashboard provides differentiated functional modules based on the Border Protection and Response Service package type. The basic function module is applicable to users who have activated any package. The function module marked with the professional edition tag is applicable only to users who have activated the professional edition package. For details about the function modules and corresponding packages, see Table 1.
Procedure
- Log in to the Huawei Qiankun console, and choose .
If only security-related services of Huawei Qiankun are purchased and activated, the security protection screen is displayed by default.
- (Optional) Configure the security protection screen.
- Click
 to set the refresh interval. After the function of refreshing the dashboard periodically is enabled, the account on the page stays in the logged-in state and will not be automatically logged out even upon session timeout.
to set the refresh interval. After the function of refreshing the dashboard periodically is enabled, the account on the page stays in the logged-in state and will not be automatically logged out even upon session timeout. - Click
 to view the dashboard in full screen.
to view the dashboard in full screen. - Click the
 button to customize the dashboard name and select the modules to be displayed.
button to customize the dashboard name and select the modules to be displayed.
Table 1 Description of modules on the security protection dashboard Applicable Package
Module
Description
Standard, Standard + automatic blocking, and Professional
Security Health Status
Displays the security health score, which is calculated based on the security issues detected by security services in real time and certain scoring rules.
Incident
Displays the numbers of handled and total external attack sources, compromised hosts, and malicious files.
Top 5 Threat Detection Types
Displays top 5 threat event types by quantity.
Top 5 Compromise Types
Displays top 5 causes leading to compromised hosts by quantity.
Security Events
Displays the number of security events of each type.
- Original Alarms: Huawei Qiankun identifies original events based on threat logs provided by Qiankun Shield devices.
- Alert: Huawei Qiankun aggregates original events into alarm events after automatic model-based analysis and manual handling by security operations experts.
- Incident: After further intelligent analysis, Huawei Qiankun classifies alarm events into three types: external attack sources, compromised hosts, and malicious files.
Attack Map
Dynamically displays the source-to-destination attack direction and region distribution of the latest threat events.
Latest Events
Displays threat event information in reverse chronological order.
Threat IP Blocking Trend
Displays the trend of the number of blocked attack source IP addresses in the last 30 days.
Detected Attack Types
Displays top 5 detected attack types by quantity.
Avg Threat Detection Duration
Displays the average time taken by Huawei Qiankun to detect threat events based on the logs reported by Qiankun Shield devices.
Threat Blocking Rate
Displays information about threat event blocking.
- Attack flow + source blocking: displays the number of threat events detected and blocked by Qiankun Shield devices based on security protection policies and blacklisted by Huawei Qiankun.
- Attack flow blocking: displays the number of threat events detected and blocked by Qiankun Shield devices based on security protection policies.
- Attack source blocking: displays the number of threat events to which Huawei Qiankun has delivered blacklists.
- Other events: displays the number of threat events that have not been handled.
Professional
Top 5 File Attack Types
Displays top 5 malicious file types by file type (such as .exe and .zip).
Top 5 Hosts by Number of Malicious Files
Displays top 5 host IP addresses with the largest number of malicious files.
Top 5 Attack Source Geo-locations
Displays top 5 countries or regions by the number of attack sources.
Threat Event Severity Distribution
Displays the distribution of threat events of different severity levels in a pie chart.
Threat Type Trend
Displays the quantity trend of external attack sources, compromised hosts, and malicious files in the last 30 days.
Threat Type Handling Status
Displays the handling status of external attack sources, compromised hosts, and malicious files (unhandled, blocked, ignored, or manually handled).
- Click
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





