Application Scenarios
Internet Egress of SMEs
Typically, small and medium-sized enterprises (SMEs) have very small or no security budgets. They often have no dedicated network security owners, and cannot afford on-site services. Even if basic security devices are purchased, results are poor as there is a lack of professional security O&M personnel. For these reasons, SMEs tend to have almost no security protection. Even a common virus may compromise the entire information system of an SME. With network attacks increasingly prevalent, routine service operations are often severely affected. This has made network security construction vital for SMEs.
Main security construction requirements of SMEs:
- There is no workforce for security O&M. This deters SMEs from purchasing multiple types of security devices.
- The security budget is very limited, and on-site services are unaffordable. SMEs prefer to outsource the network security construction to obtain basic security capabilities. In this way, the internal network can communicate with the external network without affecting routine service operations.
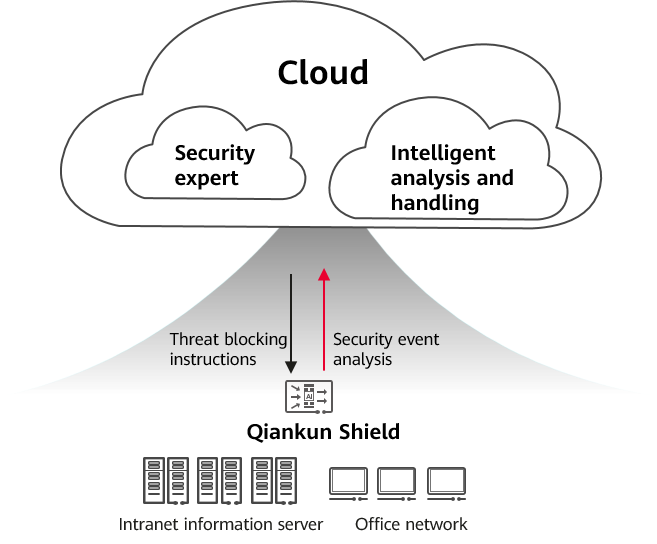
Functions implemented by the Border Protection and Response Service:
- Only one Qiankun Shield device needs to be deployed at the egress of the enterprise network. Huawei Qiankun automatically delivers intrusion prevention and antivirus capabilities to the Qiankun Shield devices to effectively block external network threats and prevent virus-infected files from spreading. In addition, the internal and external networks can communicate with each other without affecting routine service operations.
- With only minimal investment, SMEs can purchase cloud service security capabilities, obtain security expert services and intelligent threat handling capabilities, and outsource network security construction to Huawei Qiankun, greatly reducing local O&M workload.
Multi-branch Interconnection of Large Enterprises
Large enterprises usually provide services across a country, with branches distributed in multiple regions. These branches frequently communicate with each other. Typically, such enterprises have small-scale network security departments at the headquarters. These security departments mainly depend on security vendors or integrators for security construction, and purchase on-site services from vendors or service providers. Due to limited capabilities of on-site service personnel, lack of dedicated security O&M personnel in branches, and frequent transmission of Internet data between branches, the overall security posture of such enterprises is poor and they are vulnerable to all kinds of attacks; even those launched by common hackers.
Main security construction requirements of large enterprises:
- Simplified local O&M: Due to limited budgets for security O&M, security O&M personnel cannot be dispatched to each branch and on-site services cannot be purchased for each branch. Even if on-site services are purchased, robust security cannot be achieved due to limited capabilities of on-site service personnel.
- Unified protection: The solution covers all branch networks and analyzes security events of the entire enterprise. It also responds to threats in a unified manner and blocks threats in time. In addition, the headquarters can be informed of the security posture of each branch in a timely manner.
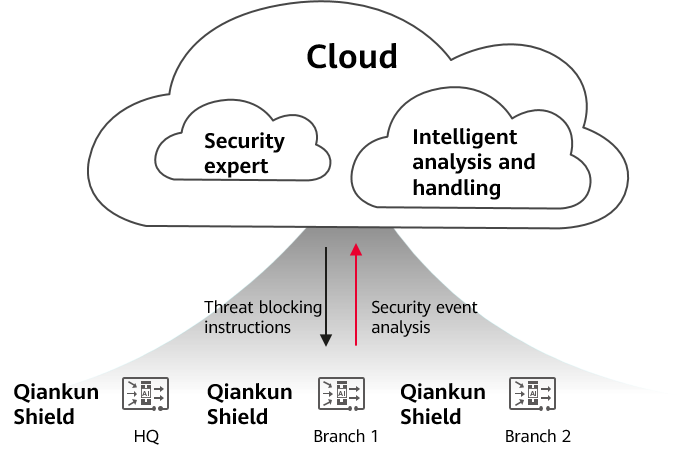
Functions implemented by the Border Protection and Response Service:
- The intelligent analysis and handling capabilities of Huawei Qiankun improve automatic O&M efficiency and automatically block threats. Security experts of Huawei Qiankun provide 24/7 online services to resolve complex network security issues and simplify local O&M.
- One Qiankun Shield device is deployed at the Internet border of each branch to act as the security protection node. The device works with security services of Huawei Qiankun to implement unified protection for all branch networks.
- Based on the overall analysis of security events through Huawei Qiankun, the system automatically responds to and blocks threats in a timely manner, and sends security alarms to the security administrators at the headquarters by email. The security administrators can then respond to emergencies and deal with serious host compromise events. The security administrators at the headquarters use the weekly and monthly reports provided by the global security service to get an understanding of the overall network security posture and the network security status of the entire enterprise.
Security Construction and Management for Some Industries
In industries such as government, healthcare, and education, upper-level administrative departments place stringent network security requirements on subordinates. However, subordinates are unable to implement comprehensive network security construction due to tight security budgets and sub-par technical capabilities. What is worse, the upper-level departments cannot effectively manage whether the network security requirements are met. They also lack a means of urging subordinates to swiftly rectify the items that fail to meet the requirements.
Main security construction requirements of such departments:
- Subordinates meet the network security requirements of upper-level departments, in spite of limited budgets.
- The upper-level departments can effectively manage the subordinates and urge them to swiftly rectify items that do not meet the requirements.
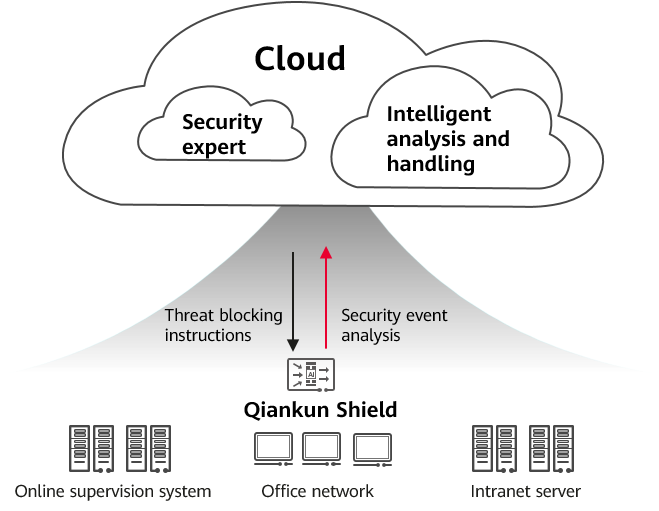
Functions implemented by the Border Protection and Response Service:
- With only minimal investment, customers can purchase cloud service security capabilities and obtain security expert services and intelligent handling capabilities.
- Huawei Qiankun is used to analyze and respond to threat events in a unified manner, and block them in time. On top of this, security experts of Huawei Qiankun help solve difficult problems, making up for insufficient technical capabilities of subordinates.
- When sending security alarms and email reports to subordinates, Huawei Qiankun also sends global security detection reports to upper-level departments to comprehensively display the security posture of subordinates and whether security events are handled in a timely manner, implementing effective and timely management of subordinates.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





