What Additional Settings Are Required If the Proxy Is Enabled?
If the proxy is enabled for edge nodes, proxy settings must be configured on edge nodes, Docker and containerized applications.
Currently, only HTTP proxy is supported.
Settings on Edge Nodes
- If an edge node is registered and managed using a certificate, and the edge node uses a network proxy, add the HTTP_PROXY and HTTPS_PROXY parameters to the environment variables and configure the /opt/IEF/Cert/user_config file.
- Add the HTTP_PROXY and HTTPS_PROXY parameters to the environment variables. You can set he network proxy through temporary and permanent environment variables.
- Method 1: Set the environment variables that take effect temporarily. The temporary environment variables take effect only in the current shell.
- Run the following commands to add the two parameters. Replace http://192.168.0.70:8888 in the following example with the actual network proxy address.
export http_proxy="http://192.168.0.70:8888" export https_proxy="http://192.168.0.70:8888"
If the network proxy requires username and password authentication, prefix the username and password to the proxy address. For example, change http://192.168.0.70:8888 to the following format:
export http_proxy="http://username:paasword@192.168.0.70:8888" export https_proxy="http://username:paasword@192.168.0.70:8888"
- After the configuration file is modified, run the installation commands on the edge node.
- Run the following commands to add the two parameters. Replace http://192.168.0.70:8888 in the following example with the actual network proxy address.
- Method 2: Set environment variables that take effect permanently.
- Run the vi /etc/profile commands to add the two parameters. Replace http://192.168.0.70:8888 in the following example with the actual network proxy address.
export http_proxy="http://192.168.0.70:8888" export https_proxy="http://192.168.0.70:8888"
If the network proxy requires username and password authentication, prefix the username and password to the proxy address. For example, change http://192.168.0.70:8888 to the following format:
export http_proxy="http://username:paasword@192.168.0.70:8888" export https_proxy="http://username:paasword@192.168.0.70:8888"
- Run the source /etc/profile command to make the modified environment variables take effect.
- After the configuration file is modified, run the installation commands on the edge node.
- Run the vi /etc/profile commands to add the two parameters. Replace http://192.168.0.70:8888 in the following example with the actual network proxy address.
- Method 1: Set the environment variables that take effect temporarily. The temporary environment variables take effect only in the current shell.
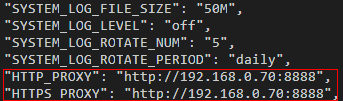
- Run the following command to open the /opt/IEF/Cert/user_config file, and add the two parameter settings. Note that http://192.168.0.70:8888 in the following example must be replaced with the actual network proxy address.
Before adding the parameters, upload the downloaded edge node installation tool and configuration file to the specified directory on the edge node and decompress the package. For details, see Node Management > Managing an Edge Node in the User Guide.
vi /opt/IEF/Cert/user_config
If the network proxy requires username and password authentication, prefix the username and password to the proxy address. For example, change http://192.168.0.70:8888 to the following format:
http://username:password@192.168.0.70:8888
- After the configuration file is modified, run the installation commands on the edge node.
- Add the HTTP_PROXY and HTTPS_PROXY parameters to the environment variables. You can set he network proxy through temporary and permanent environment variables.
Settings on Docker Daemon
In certain lab environments, servers do not have permissions to directly connect to external networks. Therefore, network proxies are required. Generally, network proxies are configured in configuration files such as /etc/environment and /etc/profile, which is applicable to most operations. However, Docker commands cannot use these proxies. For example, if the docker pull operation needs to pull an image from the external network, the following error message is displayed:
$ docker pull hello-world Unable to find image 'hello-world:latest' locally Pulling repository docker.io/library/hello-world docker: Network timed out while trying to connect to https://index.docker.io/v1/repositories/library/hello-world/images. You may want to check your internet connection or if you are behind a proxy..
- Solution 1: Stop the Docker service, and manually start the Docker daemon by using port 2375 to listen to all network interfaces.
systemctl stop docker.service
nohup docker daemon -H tcp://0.0.0.0:2375 -H unix:///var/run/docker.sock &
- Solution 2: Edit the configuration file (/etc/default/docker in Ubuntu, or /etc/sysconfig/docker in CentOS). However, it is not recommended to configure the daemon process by modifying these configuration files.
HTTP_PROXY="http://[proxy-addr]:[proxy-port]/" HTTPS_PROXY="https://[proxy-addr]:[proxy-port]/" export HTTP_PROXY HTTPS_PROXY
- Solution 3: Modifications made with this solution are persistent and always take effect. This solution also modifies the default docker.service file.
- Create an embedded systemd directory for the Docker service.
mkdir -p /etc/systemd/system/docker.service.d
- Create the /etc/systemd/system/docker.service.d/http-proxy.conf file and add the HTTP_PROXY environment variable to the file. In the following command, replace [proxy-addr] and [proxy-port] with the actual proxy address and port number, respectively.
[Service] Environment="HTTP_PROXY=http://[proxy-addr]:[proxy-port]/" "HTTPS_PROXY=https://[proxy-addr]:[proxy-port]/"
If there are internal Docker registries that can be accessed without using a proxy, set the NO_PROXY environment variable as follows:
[Service] Environment="HTTP_PROXY=http://[proxy-addr]:[proxy-port]/" "HTTPS_PROXY=https://[proxy-addr]:[proxy-port]/" "NO_PROXY=localhost,127.0.0.1,docker-registry.somecorporation.com"
- Run the following command to update the configurations:
- Run the following command to restart the Docker service:
- Create an embedded systemd directory for the Docker service.
Settings on Containerized Applications
If the proxy is enabled for an edge node, the containerized application deployed on the node must be configured with proxy addresses before it accesses the external network. You can configure proxy-related environment variables when creating a containerized application.
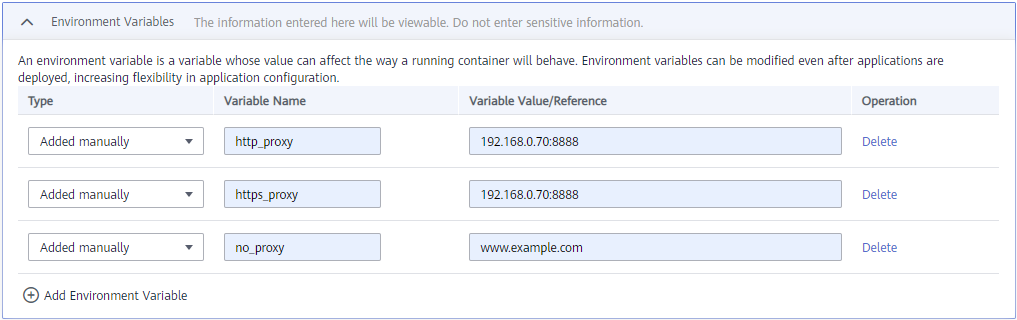
In the preceding figure, http_proxy and https_proxy are the network proxy addresses used by the edge node. Replace them with the actual network proxy addresses.
The no_proxy variable specifies the website or IP address that needs to ignore the proxy. To be specific, such an address does not use a proxy.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





