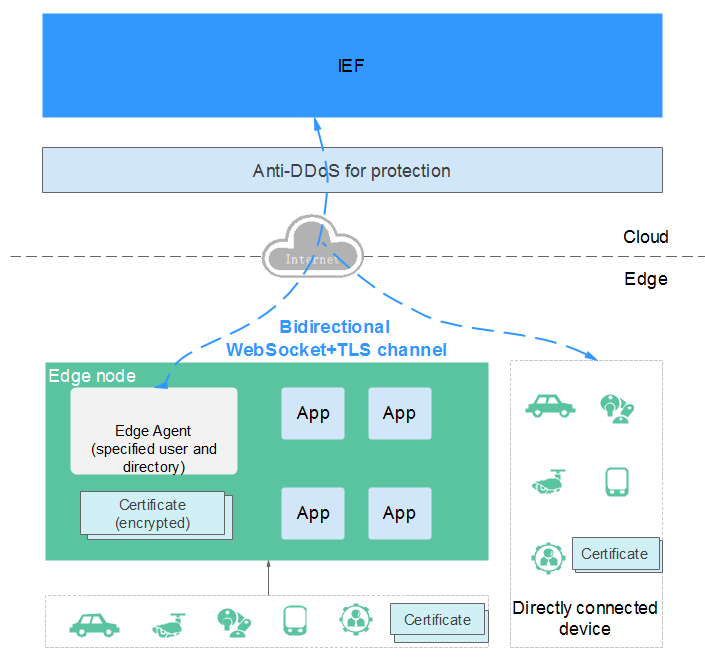
How Is Edge Environment Security Protected?
IEF provides a security solution under edge-cloud synergy.
- IAM authentication
Agencies can be created in Identity and Access Management (IAM) to allow edge nodes to access resources such as Application Operations Management (AOM), Data Ingestion Service (DIS), and SoftWare Repository for Container (SWR).
- Edge node security
Edge Agent creates dedicated service users whose accessible directories and permissions are limited. Users can upload logs and monitoring information to the cloud based on their requirements.
- Edge-cloud synergy communication security
Edge Agent initiates a request to IEF for establishing a bidirectional encrypted channel. Messages exchanged between devices and IEF are authenticated and encrypted by certificates.
- Cloud security
The frontend anti-DDoS protects the cloud against malicious attacks.
A unique access certificate is issued for each edge node. Bidirectional communication is authenticated and encrypted by certificates.
- Device security
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





