Help Center/
Edge Data Center Management/
User Guide/
System/
System Management/
Security Configuration/
Overview of Security Configuration/
Principles
Updated on 2022-04-02 GMT+08:00
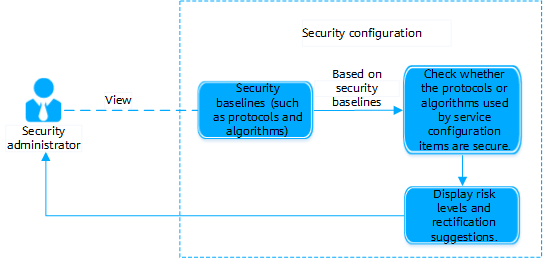
Principles
Figure 1 shows the principles of the security configuration function.
Parent topic: Overview of Security Configuration
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
The system is busy. Please try again later.
For any further questions, feel free to contact us through the chatbot.
Chatbot