How Do I Handle Open-Source Software Vulnerabilities?
CodeArts Governance decompresses and scans your software packages and firmware. It performs static analysis based on the software BOM to identify vulnerabilities and license risks. After the scan is complete, you can perform the following operations to handle the vulnerabilities.
- Check the Open Source Vulnerability Analysis tab page.
Locate the files according to the file path displayed on the report details page or in the report. If the detected software does not exist or the software version number is incorrect, no further analysis is required.
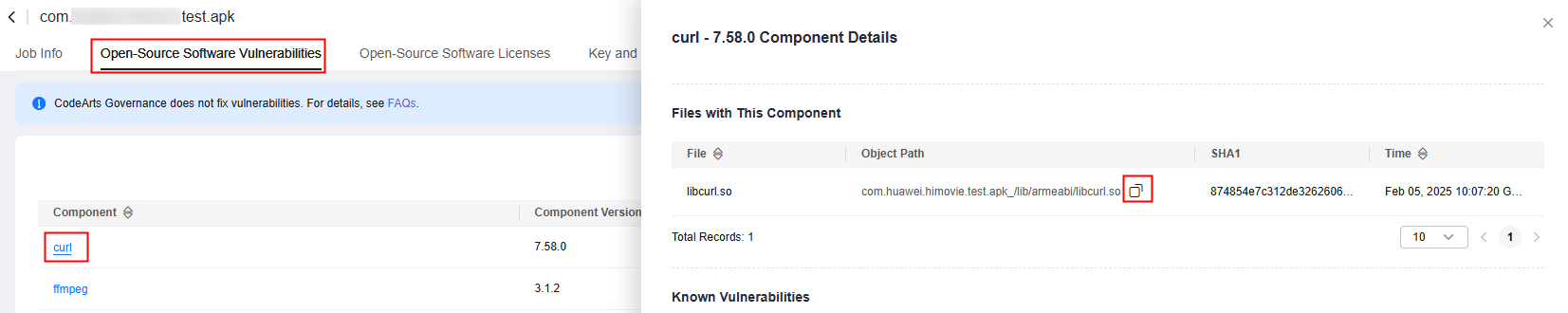
- Check the Known vulnerabilities area.
Search for the CVE number in National Vulnerability Database (NVD), Common Vulnerabilities and Exposures (CVE), and China National Vulnerability Database (CNVD) to check the vulnerability details.
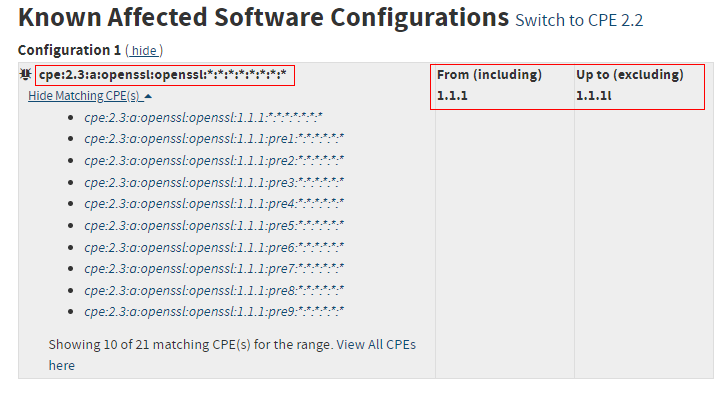
- General analysis: Confirm the scope of each vulnerability. For example, CVE-2021-3711 is listed in the Known Affected Software Configurations area by NVD, as the following figure shows. You can check whether the vulnerability affects the software version that you are using.
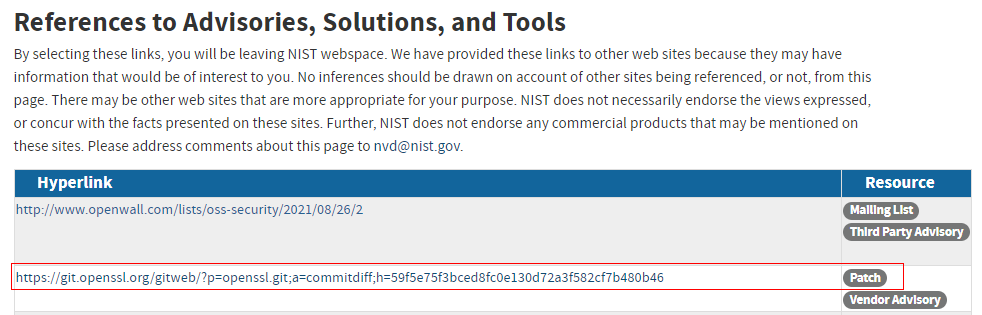
- Refined analysis: Since some vulnerabilities exist in functions, you can refer to the patches listed in the communities mentioned above to learn the vulnerability details, affected functions, and fixing methods, as shown in the following figure, and confirm whether the vulnerability affects the software that you are using.
- General analysis: Confirm the scope of each vulnerability. For example, CVE-2021-3711 is listed in the Known Affected Software Configurations area by NVD, as the following figure shows. You can check whether the vulnerability affects the software version that you are using.
- Check the license compliance. Identify the risky licenses and confirm whether they can meet your service requirements.
- Handle the vulnerabilities according to the following instructions.
- Known vulnerabilities: Upgrade the software to the version recommended by the communities mentioned above. Alternatively, install patches to fix the vulnerabilities temporarily.
- Risky licenses: Replace the risky licenses with compliant ones that function the same.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





