Overview
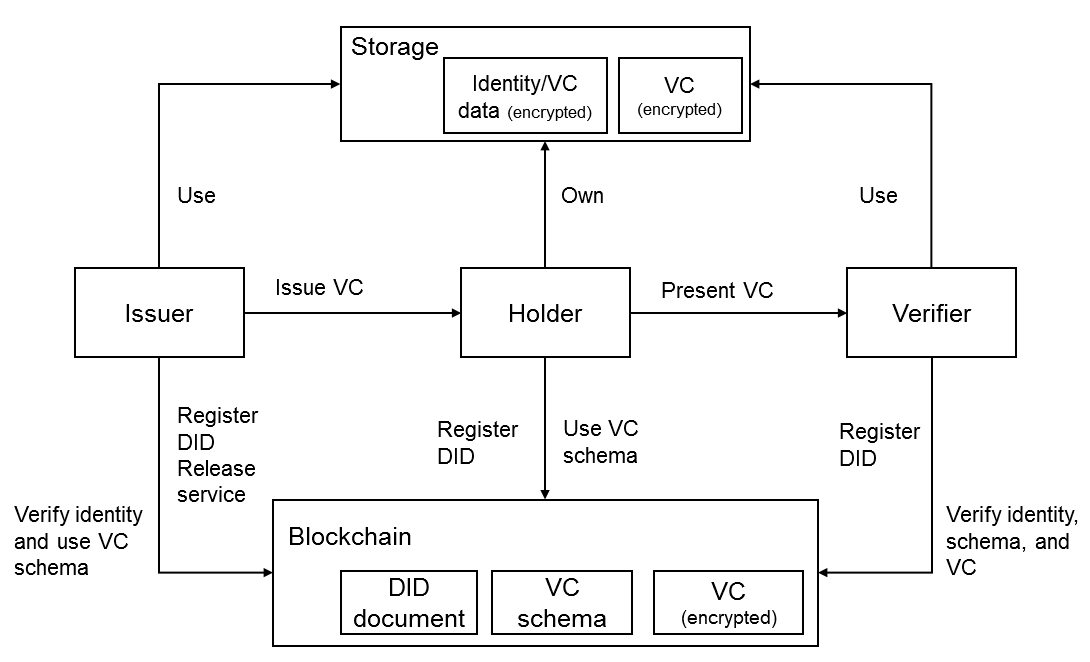
Distributed identity (DID) is a blockchain-based identity management technology. It allows you to create user identities, and register, issue, and verify verifiable credentials (VCs). BCS's DID is implemented based on the W3C DID and VC specifications. It provides unified, self-explainable, and portable distributed identifiers for individual and enterprise users to address privacy issues and identity authentication across departments, enterprises, and regions.
Implementation
- Each role can call the Enterprise Identity Registration (with Service) and Registering a DID APIs to generate their own DID which they fully control, and then publish the DID document to the blockchain to complete identity registration. The DID of an enterprise includes information about the services the enterprise can provide in various application scenarios.
There are three roles: issuer, holder, and verifier. Each role can be a device, an application, an individual, or an organization.
- VCs are used to authenticate identities. Relevant entities register and continuously maintain credential schemas on the blockchain. Holders initiate authentication requests to issuers, obtain credentials, and provide the credentials to verifiers to complete verification.
- Verifiers verify VCs presented by holders by using an API to ensure that holders are qualified and permitted to proceed with relevant services.
Usage
You can download the private key and certificate on the BCS console or generate them using OpenSSL. For details, see How Can I Obtain Private Keys and Certificates of Fabric Users?
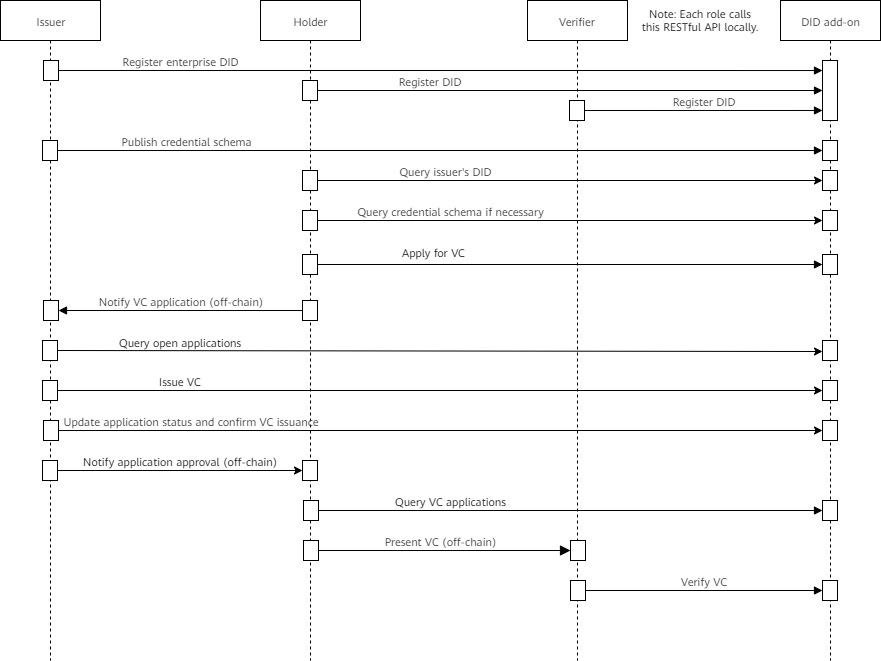
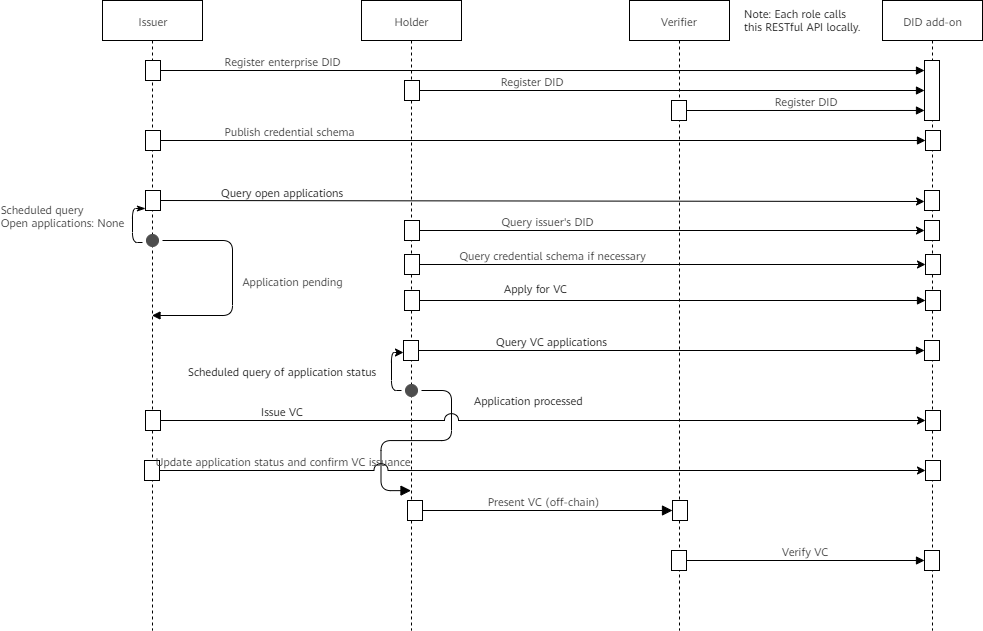
Holders can apply for VCs on or off the blockchain.
- Off-chain application: The holder sends the identity or VC data for applying for a VC to the issuer.
- On-chain application: The holder encrypts and stores the identity or VC data for applying for a VC on the blockchain.
On-chain application can be online or offline, depending on whether communication channels are required between the holder and the issuer.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot