Why Can't TLS v1.0 or v1.1 Be Used for the NGINX Ingress Controller Add-on?
Symptom
If the TLS version of the client is earlier than v1.2, an error is reported during negotiation between the client and Nginx Ingress.
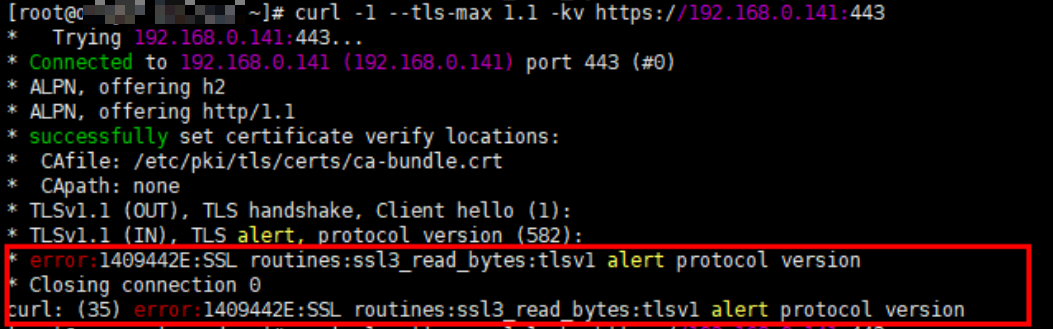
Solution
By default, NGINX Ingress Controller for CCE Autopilot clusters supports only TLS v1.2 and v1.3. If additional TLS versions are needed, you can add the @SECLEVEL=0 field to the ssl-ciphers parameter for NGINX Ingress Controller. For details, see TLS/HTTPS.
For the purpose of secure data transmission, you should not use TLS v1.0 or v1.1. These outdated protocols pose security risks that could lead to data leak or be exploited by attackers. You are advised to upgrade TLS to v1.2 or later for enhanced communication security.
- Log in to the CCE console and click the cluster name to access the cluster console. In the navigation pane, choose Add-ons. Then locate the NGINX Ingress Controller add-on and click Manage.
- In the right corner of the installed add-on list, click Edit.
- Add the following configuration to the Nginx Parameters:
{ "ssl-ciphers": "@SECLEVEL=0 ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA256:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA", "ssl-protocols": "TLSv1 TLSv1.1 TLSv1.2 TLSv1.3" } - Click OK.
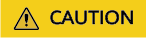
- Use TLS v1.1 for access again and verify that the response is normal.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





