Step 4: Create a Non-administrator IAM User
This topic walks you through how to create a non-administrator IAM user.
IAM authentication is used for tenant log collection. So you need to create an IAM user (machine-machine account) with the minimum permission to access SecMaster APIs. MFA must be disabled for the IAM user. This user is used to log in to the log collector on the tenant side and access SecMaster.
Creating a Non-administrator IAM User
- Log in to the console as the IAM administrator.
- Click
 in the upper left corner of the page and choose Management & Governance > Identity and Access Management.
in the upper left corner of the page and choose Management & Governance > Identity and Access Management. - Create a user group.
- In the navigation pane on the left, choose User Groups. On the displayed page, click Create User Group in the upper right corner.
- On the Create User Group page, specify user group name and description.
- Name: Set this parameter to Tenant collection.
- Description: Enter a description.
- Click OK.
- Assign permissions to the user group.
- In the navigation pane on the left, choose Permissions > Policies/Roles. In the upper right corner of the displayed page, click Create Custom Policy.
- Configure a policy.
- Policy Name: Set this parameter to Least permission policy for tenant collection.
- Policy View: Select JSON.
- Policy Content: Copy the following content and paste it in the text box.
{ "Version": "1.1", "Statement": [ { "Effect": "Allow", "Action": [ "secmaster:workspace:get", "secmaster:node:create", "secmaster:node:monitor", "secmaster:node:taskQueueDetail" , "secmaster:node:updateTaskNodeStatus" ] } ] }
- Click OK.
- Assign permissions to the created user group.
- In the navigation pane on the left, choose User Groups. On the displayed page, click Tenant collection created in 3.
- On the Permissions tab, click Authorize.
- On the Select Policy/Role page, search for and select the Least permission policy for tenant collection added in 4, and click Next.
- Set the minimum authorization scope. Select All resources for Scope. After the setting is complete, click OK.
- Create a user.
- In the navigation pane on the left on the IAM console, choose Users. Then, click Create User in the upper right corner.
- Set basic user information.
Table 1 Basic user information Parameter
Description
User Details
Custom configuration.
Record the IAM Username you configure. The username is required later.
Access Type
Programmatic access
Select this parameter.
Management console access
Deselect this parameter.
Credential Type
Access key
Select this parameter.
Password
Select this parameter.
After selecting the Password parameter, select Set by user, and set a password. Record the IAM user password you set. This password is required later.
- Click Next.
- Search for and select the Tenant collection user group created in 3, and click Create in the lower right corner.
- Verify that no virtual MFA devices are associated to the user.
- In the navigation pane on the left on the IAM console, choose Users. Then, click the user created in 6.
- Click the Security Settings tab and ensure that the status of Virtual MFA Device is Unbound.
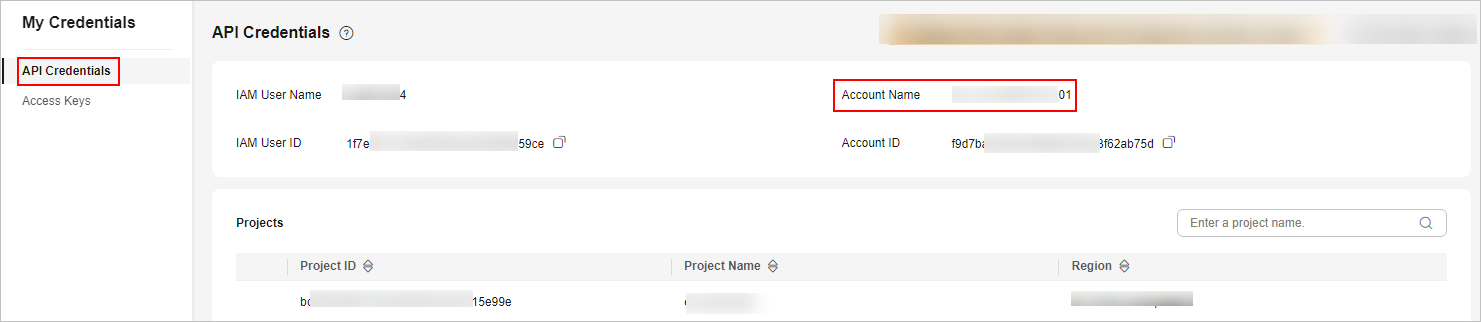
- View the domain account information of the IAM user.
- Hover over the username in the upper right corner and select My Credentials from the drop-down list.
- On the API Credentials page, view and record the account name, which is the domain account for installing the isap-agent.
Figure 1 Account Name
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





