Configuring the Application
Before initiating transactions, the inviting party must download the administrator certificates of the orderer and organization democraticBank, and the certificates in which the private keys are hidden by invitees A and B.
Encrypt the private keys in the downloaded certificates for storage.
Prerequisites
An ECS has been created. For more information on how to create ECSs, see Elastic Cloud Server User Guide.
Downloading SDK Configurations and Certificates
- On the Instance Management page, click Download Client Configuration on the card containing the bank-union-demo instance of the inviting party.
- Select SDK Configuration File and set the parameters as described in Table 1.

To ensure that the demo runs properly, set the parameters as described in the following table.
Table 1 SDK file parameters Parameter
Setting
Chaincode Name
Enter fabbank.
Certificate Root Path
Enter /opt/bank/src/bank/conf/crypto.
NOTE:/opt/bank/src/bank/conf/crypto is the internal path of the container and is mounted to the /root/bankuniondemo path of the ECS.
Channel
Retain the automatically selected testchannel.
Member
Retain the default settings. Do not select all organizations and peers.
- Select Orderer Certificate and Peer Certificates. Under Peer Certificates, retain the default selection for Peer Organization and select Administrator certificate. Click Download.
- Decompress the downloaded file. Duplicate the sdk-config.yaml file with another two copies, and name the three files democraticBank.yaml, civilizationBank.yaml, and harmoniousBank.yaml. Then, save the files to the /root/bankuniondemo directory on the ECS.
- Create the bankuniondemo directory in the /root directory of the ECS.
- According to Installing and Instantiating a Chaincode, the chaincode installed by all parties (inviting party democraticBank, invitee A civilizationBank, and invitee B harmoniousBank) must be the same one. Therefore, you only need to download the inviting party's SDK configuration file sdk-config.yaml to obtain the chaincode and certificate path information. Then, duplicate the file with two copies, and rename the three files.
- On the card containing the instance of invitee A, click Download Client Configuration, and select Peer Certificates and Administrator certificate to download the administrator certificate of the civilizationBank organization.
- Invitee A deletes the private key files (server.key file in the tls directory and files in the keystore folder in the msp directory) from the administrator certificate of organization civilizationBank.
Figure 1 Deleting the server.key file from the tls directory
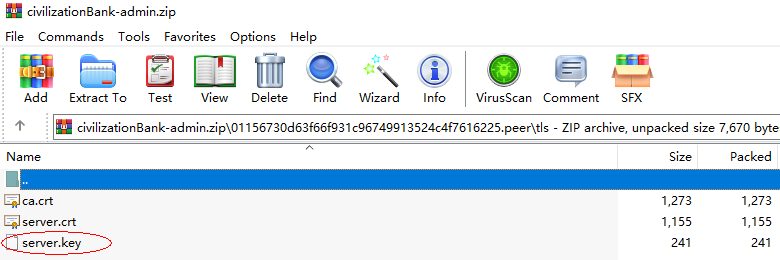 Figure 2 Deleting the keystore file from the msp directory
Figure 2 Deleting the keystore file from the msp directory
- Invitee B repeats 5 to 6 to download the administrator certificate of organization harmoniousBank and delete the private key files.
- The inviting party stores the downloaded bank-union-demo-orderer administrator certificate, the administrator certificate of organization democraticBank, and certificates of organizations civilizationBank and harmoniousBank (in which the private key files have been deleted by the invitees) to the /root/bankuniondemo directory of the prepared ECS.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





