Introduction
This section describes fine-grained permissions management for your enhanced Hyperledger Fabric blockchains. If your Huawei Cloud account does not need individual IAM users, you may skip over this section.
A policy is a set of permissions defined in JSON format. By default, new IAM users do not have any permissions assigned. You need to add a user to one or more groups, and assign permissions policies to these groups. The user then inherits permissions from the groups it is a member of. This process is called authorization. After authorization, the user can perform specified operations on BCS based on the permissions.
You can grant users permissions by using roles and policies. Roles are a type of coarse-grained authorization mechanism that defines permissions related to user responsibilities. Policies define API-based permissions for operations on specific resources under certain conditions, allowing for more fine-grained, secure access control of cloud resources.
For details about policies of enhanced Hyperledger Fabric blockchains, see Permissions Management.
Supported Actions
Actions supported by policies are specific to APIs. Common concepts related to policies include:
- Permissions: Statements in a policy that allow or deny certain operations.
- APIs: APIs that will be called for performing certain operations.
- Actions: Specific operations that are allowed or denied.
- Related actions: Actions on which a specific action depends to take effect. When assigning permissions for the action to a user, you also need to assign permissions for the related actions.
- Supported: IAM projects and enterprise projects
Type of projects in which policies can be used to grant permissions. A policy can be applied to IAM projects, enterprise projects, or both. Policies that contain actions for both IAM and enterprise projects can be used and take effect for both IAM and Enterprise Management. Policies that only contain actions for IAM projects can be used and applied to IAM only. For details, see What Are the Differences Between IAM and Enterprise Management?.
Policy-based authorization is useful if you want to allow or deny the access to an API. Notes:
- Currently, only BCS instances created based on existing clusters support fine-grained authorization. To achieve this, grant namespace permissions to these clusters on the CCE console using an account with CCE Administrator or higher permissions. For example, grant the view namespace permission to the user group with the BCS Fabric ReadOnlyAccess permission and grant the cluster admin namespace permission to the user group with the BCS Fabric FullAccess permission. For details, see Namespace Permissions (Kubernetes RBAC-based).
- If a user wants to query the agency status, they must be granted the IAM ReadOnlyAccess permission. To authorize an agency, contact an account with the Security Administrator role.
- To create a yearly/monthly BCS instance, grant the BSS Operator role. Do not use the BCS Fabric ReadOnlyAccess and BSS roles together to avoid unexpected unsubscription.
- Do not use the Tenant Guest role together with the BCS Fabric FullAccess policy, or some function pages will be hidden.
- Some APIs of dependent services do not support enterprise project-based permission management. You need to grant project permissions to IAM user groups during enterprise project authorization. For example, to create an instance, you need to grant the VPC ReadOnlyAccess project permission. To view monitoring information, you need to grant the AOM ReadOnlyAccess project permission. To view contract instances, you need to grant the CloudIDE ReadOnlyAccess project permission. To add an organization, you need to grant the SFS Turbo ReadOnlyAccess project permission.
Configure specific policies as required. The following figures show examples. For details, see Creating a User Group and Assigning Permissions.
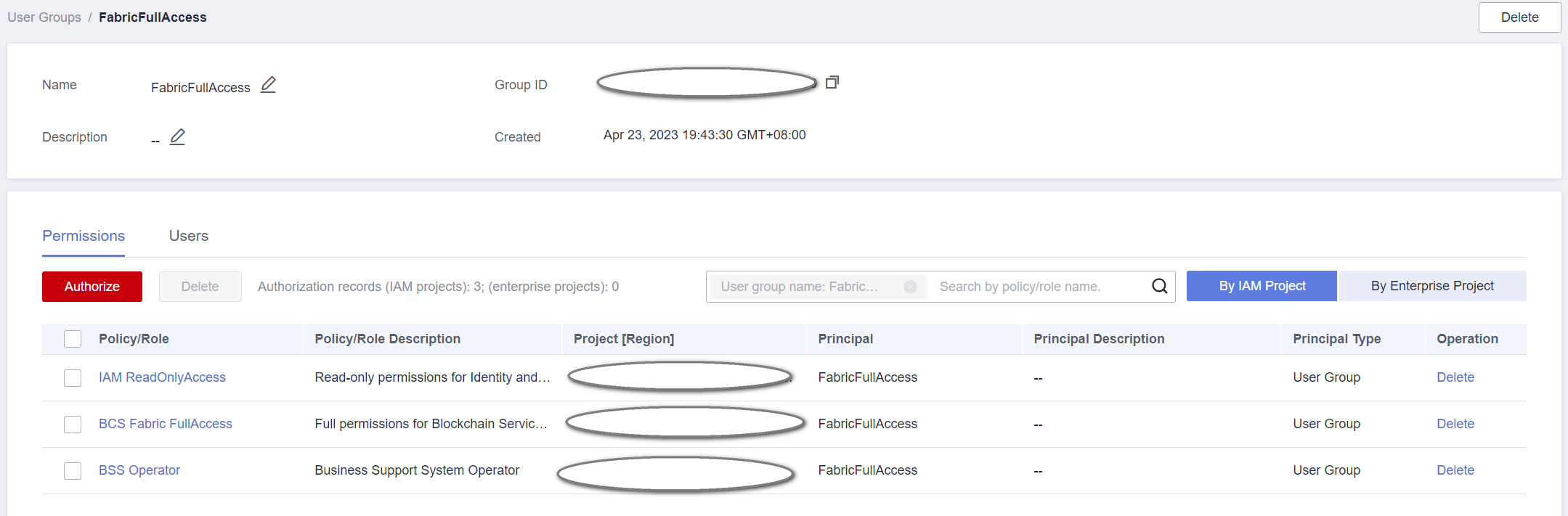
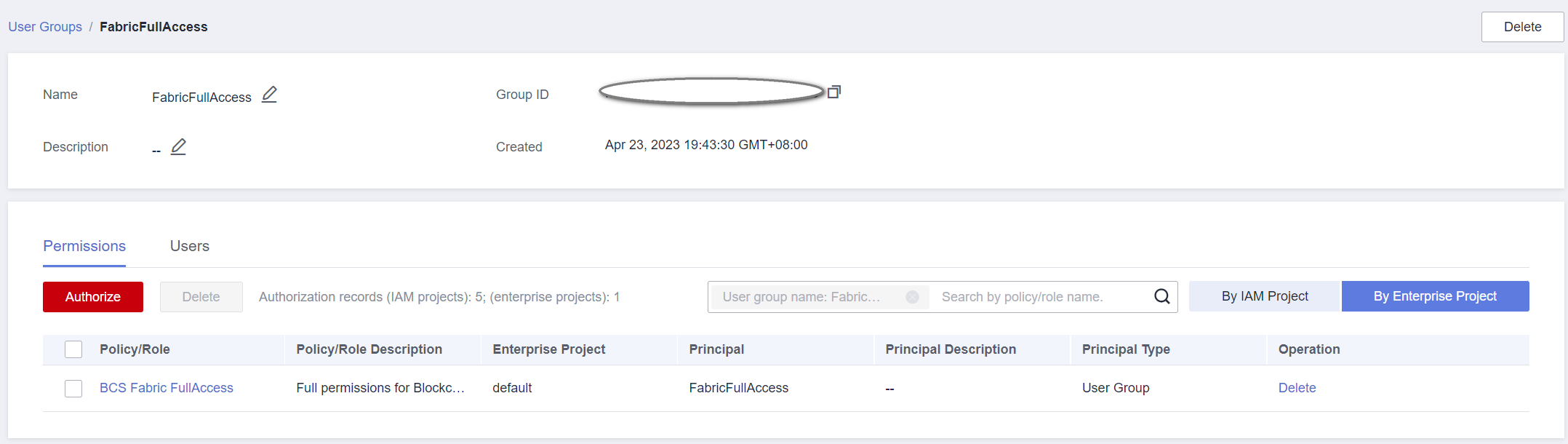
- After BCS Fabric FullAccess is granted to a project and the user group is configured.
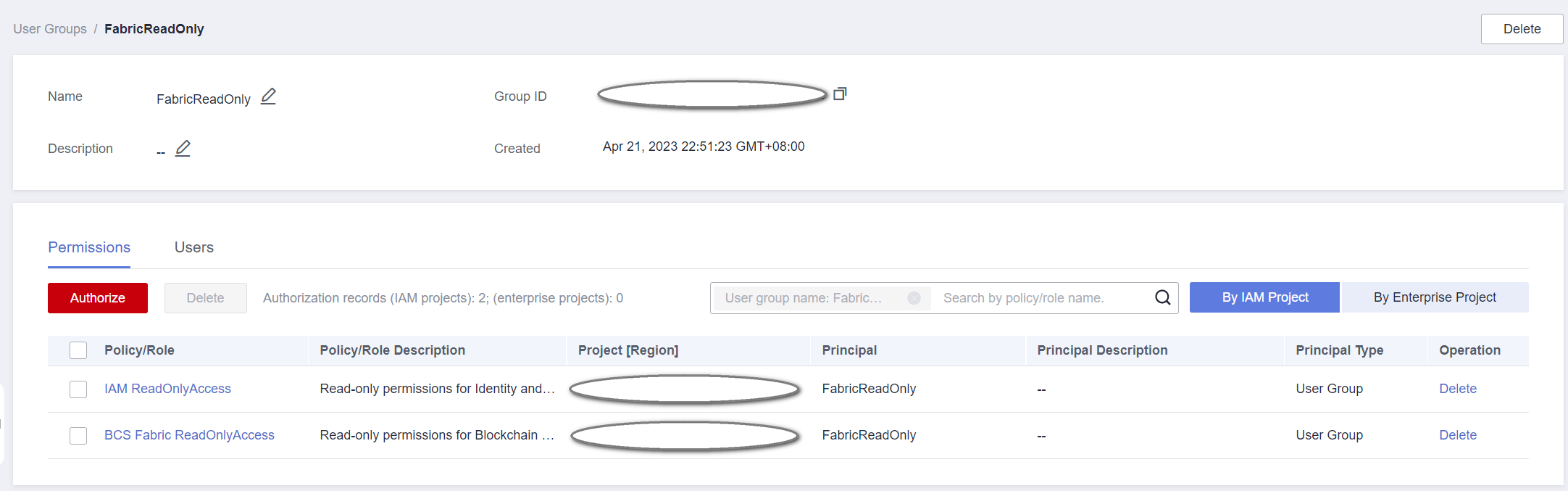
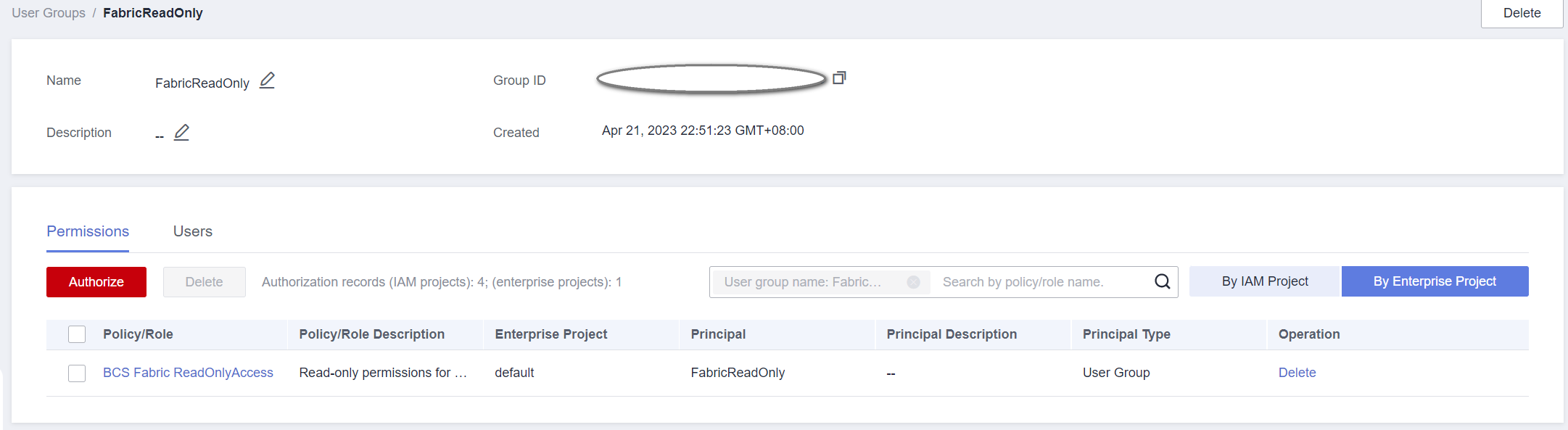
- After BCS Fabric ReadOnlyAccess is granted to a project and the user group is configured.
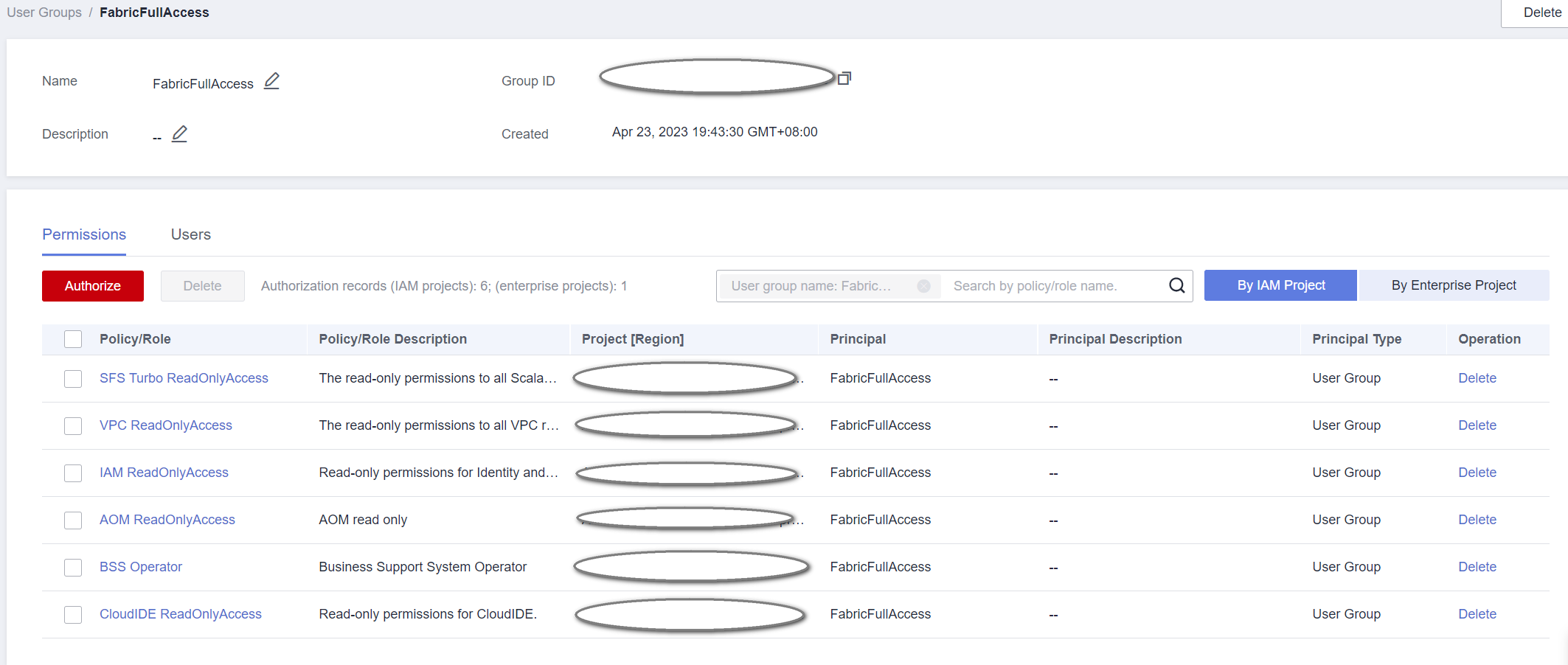
- After BCS Fabric FullAccess is granted to an enterprise project and the user group is configured.
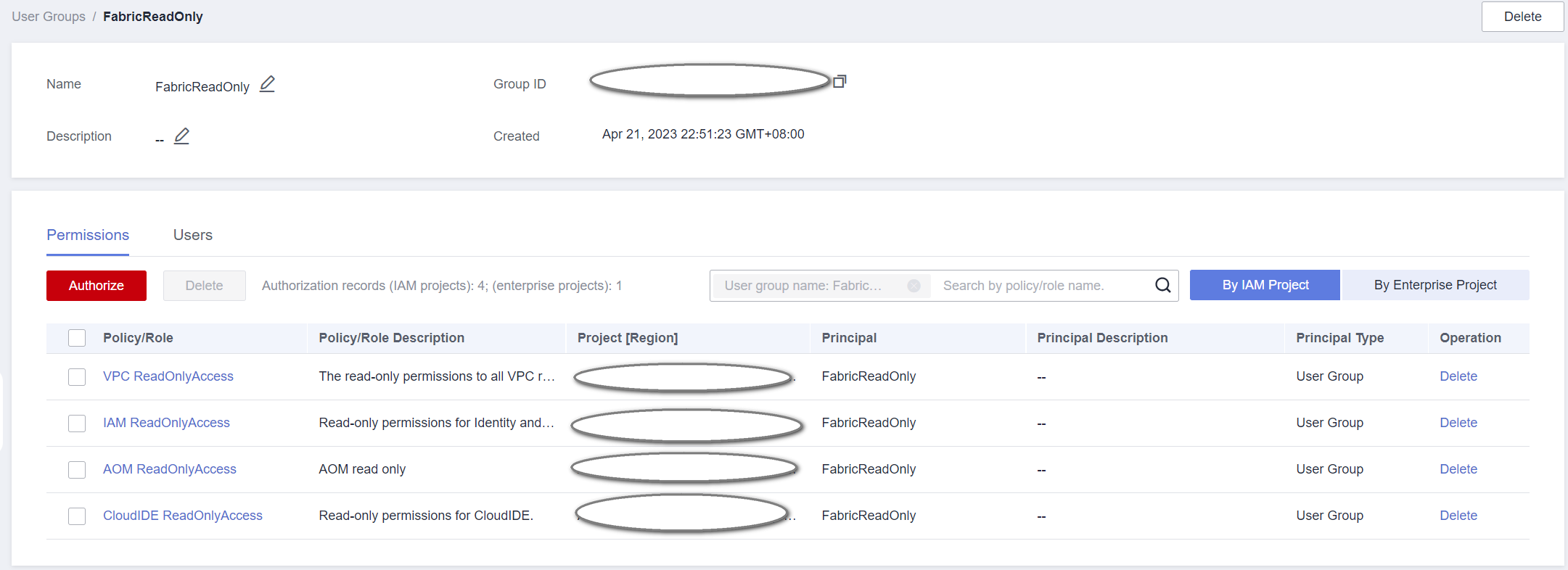
- After BCS Fabric ReadOnlyAccess is granted to an enterprise project and the user group is configured.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot