Managing Integrations
SA integrates a variety of security products to aggregate their detection data and manage all findings in one place.
If you want to aggregate events from other products, click My Recommendations in the upper right corner of the Integrations page and provide details about the product.
This topic walks you through how to manage security product integrations, including enabling and disabling a product integration.
Enabling an Integration
- Log in to the management console.
- Click
 in the upper left corner of the page and choose .
Figure 1 Integrations
in the upper left corner of the page and choose .
Figure 1 Integrations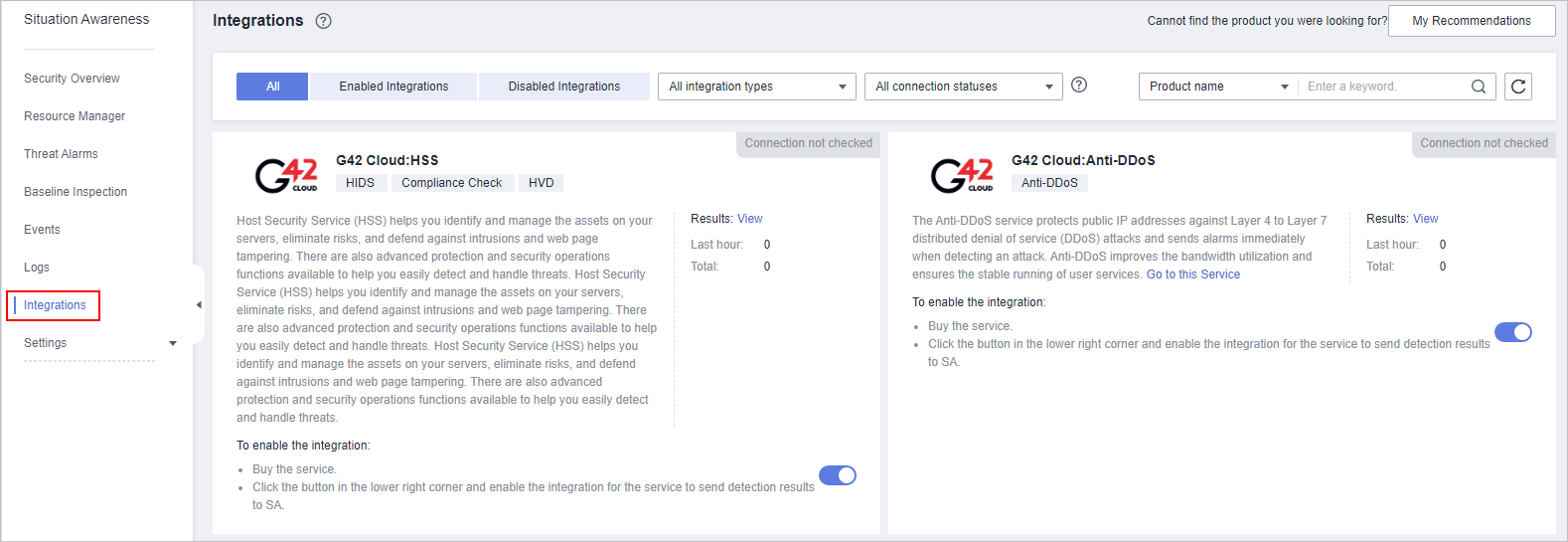
- Query the security products you want to aggregate in SA.
Select the Disabled Integrations tab and search for security products you want to enable. For more query methods, see Viewing Integrations.
- Start to receive events.
Locate the product whose detection data you want to receive in SA and enable the integration.
About 5 minutes after you enable an integration, you will receive the detection data reported by the product.
To let SA receive the product events properly, ensure that the corresponding protection of the product has been enabled.
Disabling an Integration
- Query the security products that have been aggregated in SA.
Select the Enabled Integrations tab and search for security products you want. For more query methods, see Viewing the Integration List.
- Stop to receive results.
Locate the product whose detection data you no longer want to receive in SA and disable the integration.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





