Creating a Custom CCE Node Image
Custom CCE node images are created using the open source tool HashiCorp Packer of v1.7.2 or later and the open source plug-in. The cce-image-builder template is provided to help you quickly build images.
Packer is used to create custom container images. It offers builders, provisioners, and post-processors that can be flexibly combined to automatically create image files concurrently through JSON or HCL template files.
Packer has the following advantages:
- Automatic build process: You can use Packer configuration files to specify and automate the build process.
- High compatibility with cloud platforms: Packer can interconnect with most cloud platforms and various third-party plug-ins.
- Easy-to-use configuration files: Packer configuration files are simple and intuitive to write and read. Parameter definitions are easy to understand.
- Diverse image build functions: Common functional modules are supported. For example, the provisioner supports the shell module in remote script execution, the file module in remote file transfer, and the breakpoint module for process pauses.
Constraints
- Suggestions on using CCE node images:
- You are advised to use the default node images maintained by CCE. These images have passed strict tests and updated in a timely manner, providing better compatibility, stability, and security.
- Use the base images provided by CCE to create custom images.
- The component package on which nodes depend for running is preset in the base image. The package version varies with the cluster version. For custom images, CCE does not push component package updates.
- When customizing an image, exercise caution when modifying kernel parameters. Any improper kernel parameter modification will deteriorate the system running efficiency.
Modifying the following kernel parameters will affect the system performance: tcp_keepalive_time, tcp_max_tw_buckets, somaxconn, max_user_instances, max_user_watches, netdev_max_backlog, net.core.wmem_max, and net.core.rmem_max.
To modify node kernel parameters, fully verify the modification in a test environment before applying the modification to the production environment.
Precautions
- Before you create an image, prepare:
- An ECS executor: An ECS x86 server is used as the Linux executor. You are advised to select CentOS7 and bind an EIP to it so that it can access the public network and be used to install Packer.
- Authentication credentials: Obtain the AK/SK of the tenant or user with required permissions.
- Security group: Packer creates a temporary ECS and uses a key pair to log in to the ECS using SSH. Ensure that TCP:22 is enabled in the security group.
- When you create a custom node image, make sure:
- You follow the instructions in this section to prevent unexpected problems.
- You have the sudo root or root permissions required to log in to VMs created from base images.
- When the creation is complete:
- The image creation process uses certain charging resources, including ECSs, EVS disks, EIPs, bandwidth, and IMS images. These resources are automatically released when the image is successfully created or fails to be created. Release the resources in time to ensure no charges are incurred unexpectedly.
Creating a Node Image
- Download cce-image-builder.
Log in to the ECS executor, download and decompress cce-image-builder.
tar zvxf cce-image-builder.tgz cd cce-image-builder/

The cce-image-builder contains:
- turbo-node.pkr.hcl # Packer configuration template used for creating the image. For details about how to modify the template, see 3.
- scripts/* # CCE image creation preset in the template. Do not modify it. Otherwise, the image might become unavailable.
- user-scripts/* # Custom package script directory preset in the template. Take example.sh as an example. When you create a custom image, the image is automatically uploaded to the temporary server and executed.
- user-packages/* # Custom package directory preset in the template. Take example.package as an example. When you create a custom image, the image is automatically uploaded to /tmp/example.package in the temporary server.
- Install Packer.
Download and install the HashiCorp Packer. For details, see Install Packer.

The Packer version needs to be 1.10.0.
Take the CentOS 7 executor as an example. Run the following command to automatically install Packer (This example is for reference only. For detailed operations, see the official guide):# Configure the yum repository and install Packer. sudo yum install -y yum-utils sudo yum-config-manager --add-repo https://rpm.releases.hashicorp.com/RHEL/hashicorp.repo sudo yum -y install packer-1.10.0 # Configure an alias to avoid duplicate Packer binary in the OS and check the Packer version. rpm -q packer alias packer=$(rpm -ql packer) packer -v
- Define Packer template parameters.
The cce-image-builder/turbo-node.pkr.hcl file defines the process of building an image using Packer. For details, see Packer Documentation.

- Parameters of variables or variable
turbo-node.pkr.hcl defines the parameters required in the process of building an image. You can configure the parameters based on the live environment. For details, see Table 1.
- Parameter of packer
required_plugins defines the add-on dependency of Packer, including the add-on source and version range. When you run packer init, the add-on is automatically downloaded and initialized.
packer { required_plugins { huaweicloud = { version = ">= 1.0.4" source = "github.com/huaweicloud/huaweicloud" } } } - Parameter of source
The preceding defined variables are referred to automatically configure the parameters required for creating an ECS.
- Parameter of build
The scripts are executed from top to bottom. Common modules such as the file upload module and script execution shell module are supported. The corresponding scripts and files are stored in the user-scripts and user-packages directories, respectively, in cce-image-builder.
Example:build { sources = ["source.huaweicloud-ecs.builder"] # Example: provisioner "file" { source = "<source file path>" destination = "<destination file path>" } provisioner "shell" { scripts = [ "<source script file: step1.sh>", "<source script file: step2.sh>" ] } provisioner "shell" { inline = ["echo foo"] } }
- Parameters of variables or variable
- Configure environment variables.
Configure the following environment variables on the executor:
export REGION_NAME=xxx export IAM_ACCESS_KEY=xxx export IAM_SECRET_KEY=xxx export ECS_VPC_ID=xxx export ECS_NETWORK_ID=xxx export ECS_SECGRP_ID=xxx export CCE_SOURCE_IMAGE_ID=xxx export PKR_VAR_ecs_flavor=xxx
Table 1 Variables configuration Parameter
Description
Remarks
REGION_NAME
Region to which the project belongs
To obtain the region information, go to My Credentials.
IAM_ACCESS_KEY
Access key for user authentication
Apply for a temporary AK and delete it when the image is built successfully.
IAM_SECRET_KEY
Secret key for user authentication
Apply for a temporary SK and delete it when the image is built successfully.
ECS_VPC_ID
VPC ID
Used by the temporary ECS server, which must be the same as that of the executor
ECS_NETWORK_ID
Network ID of the subnet
Used by the temporary ECS server. It is recommended that the value be the same as that of the executor. It is not the subnet ID.
ECS_SECGRP_ID
Security group ID
Used by the temporary ECS. The public IP address of the executor must be allowed to pass through port 22 in the inbound direction of the security group to ensure that the executor can log in to the temporary ECS using SSH.
CCE_SOURCE_IMAGE_ID
Latest CCE node image ID
Submit a service ticket to obtain the image ID.
PKR_VAR_ecs_flavor
Specifications of a temporary ECS
Enter a node flavor supported by CCE. The recommended flavor is 2 vCPUs and 4 GiB memory or higher.
Note: Retain the default values of other parameters. To change the values, refer to the description in the variable definition in turbo-node.pkr.hcl and configure the value using environment variables.
Use the ECS flavor variable ecs_az as an example. If no AZ is specified, select a random AZ. If you want to specify an AZ, configure an environment variable. The same applies to other parameters.
# export PKR_VAR_<variable name>=<variable value> export PKR_VAR_ecs_az=xxx
- Customize scripts and files.
Compile scripts and files by referring to the file and shell modules defined by the build field in the pkr.hcl file, and store the scripts and files in the user-scripts and user-packages directories in cce-image-builder.

When customizing an image, exercise caution when modifying kernel parameters. Any improper kernel parameter modification will deteriorate the system running efficiency.
Modifying the following kernel parameters will affect the system performance: tcp_keepalive_time, tcp_max_tw_buckets, somaxconn, max_user_instances, max_user_watches, netdev_max_backlog, net.core.wmem_max, and net.core.rmem_max.
To modify node kernel parameters, fully verify the modification in a test environment before applying the modification to the production environment.
- Create a custom image.
After custom parameter settings, create an image. The creation will take 3 to 5 minutes.
make image

In the encapsulation script packer.sh:
- Automatic access of hashicorp.com by Packer is disabled by default for privacy protection and security purposes.
export CHECKPOINT_DISABLE=false
- The debugging detailed logs option is enabled by default for better visibility and traceability. The local Packer build logs packer_{timestamp}.log is specified so that the logs can be packed to the /var/log/ directory during build. If sensitive information is involved, remove the related logic.
export PACKER_LOG=1 export PACKER_BUILD_TIMESTAMP=$(date +%Y%m%d%H%M%S) export PACKER_LOG_PATH="packer_$PACKER_BUILD_TIMESTAMP.log"
For details about Packer configuration, see Configuring Packer.
After the image is created, information similar to the following will display.
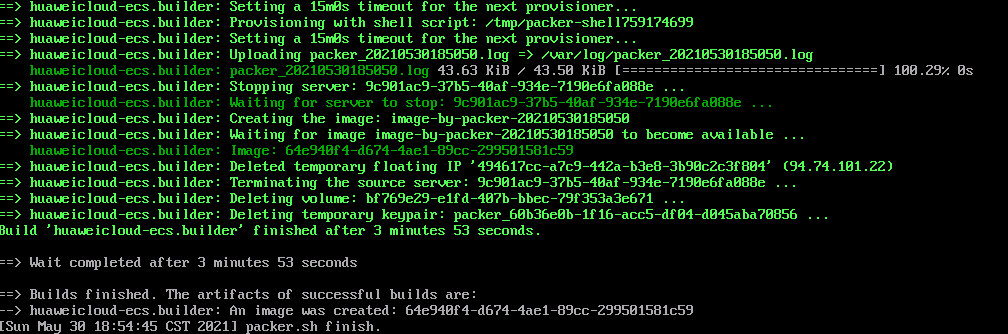
- Automatic access of hashicorp.com by Packer is disabled by default for privacy protection and security purposes.
- Clean up build files.
Clear the build files on the executor, mainly the authentication credentials in turbo-node.pkr.hcl.
- If the authentication credentials are temporary, directly release the executor.
- If they are built automatically, add post-processor in the configuration file to execute related operations.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





