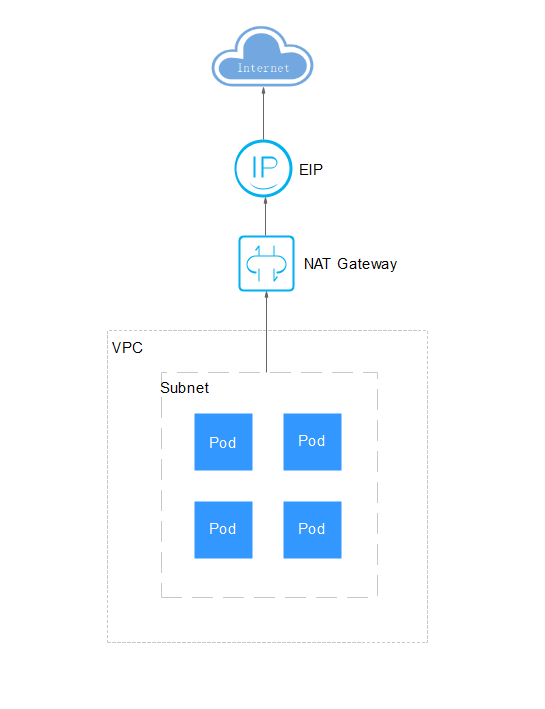
Accessing the Internet from a Container
Containers can access the Internet in either of the following ways:
- Bind an EIP to the node where the container is located.
- Configure SNAT rules through NAT Gateway.
You can use NAT Gateway to enable container pods in a VPC to access the Internet. NAT Gateway provides source network address translation (SNAT), which translates private IP addresses to a public IP address by binding an elastic IP address (EIP) to the gateway, providing secure and efficient access to the Internet. Figure 1 shows the SNAT architecture. The SNAT function allows the container pods in a VPC to access the Internet without being bound to an EIP. SNAT supports a large number of concurrent connections, which makes it suitable for applications involving a large number of requests and connections.
To enable a container to access the Internet, perform the following steps:
- Obtain an EIP.
- Log in to the management console.
- Click
 in the upper left corner of the management console and select a region and a project.
in the upper left corner of the management console and select a region and a project. - Click
 in the upper left corner and choose Networking > Elastic IP in the expanded list.
in the upper left corner and choose Networking > Elastic IP in the expanded list. - On the EIPs page, click Assign EIP.
- Configure parameters as required.

Set Region to the region where container pods are located.
- Create a NAT gateway.
- Click
 in the upper left corner and choose Networking > NAT Gateway in the expanded list.
in the upper left corner and choose Networking > NAT Gateway in the expanded list. - On the Public Network Gateways page, click Create Public NAT Gateway in the upper right corner.
- Configure parameters as required.

Select the same VPC.
- Click
- Configure an SNAT rule and bind the EIP to the subnet.
- On the page displayed, click the name of the NAT gateway for which you want to add the SNAT rule.
- On the SNAT Rules tab page, click Add SNAT Rule.
- Configure parameters as required.

SNAT rules take effect by CIDR block. As different container network models use different communication modes, the subnet needs to be selected according to the following rules:
- Tunnel network and VPC network: Select the subnet where the node is located, that is, the subnet selected during node creation.
- Cloud Native Network 2.0: Select the subnet where the container is located, that is, the container subnet selected during cluster creation.
If there are multiple CIDR blocks, you can create multiple SNAT rules or customize a CIDR block as long as the CIDR block contains the container subnet (Cloud Native Network 2.0) or the node subnet.
After the SNAT rule is configured, workloads can access the Internet from the container. The Internet can be pinged from the container.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot