Marking Vulnerabilities as Ignored
This section shows how to mark vulnerabilities as Ignored. Before the marking, make sure that the vulnerabilities are free of security risks.
After you mark a vulnerability as Ignored, you cannot change its status again and the system will no longer consider this vulnerability risky. You can click Unignore to bring back the vulnerability.
Prerequisites
- An account and its password have been obtained for logging in to the management console.
- At least one vulnerability has been detected.
Procedure
- Log in to the management console.
- Choose Security > Vulnerability Scan Service > Dashboard.
- On the right of the Vulnerability List area, click View to go to the Vulnerability List page.
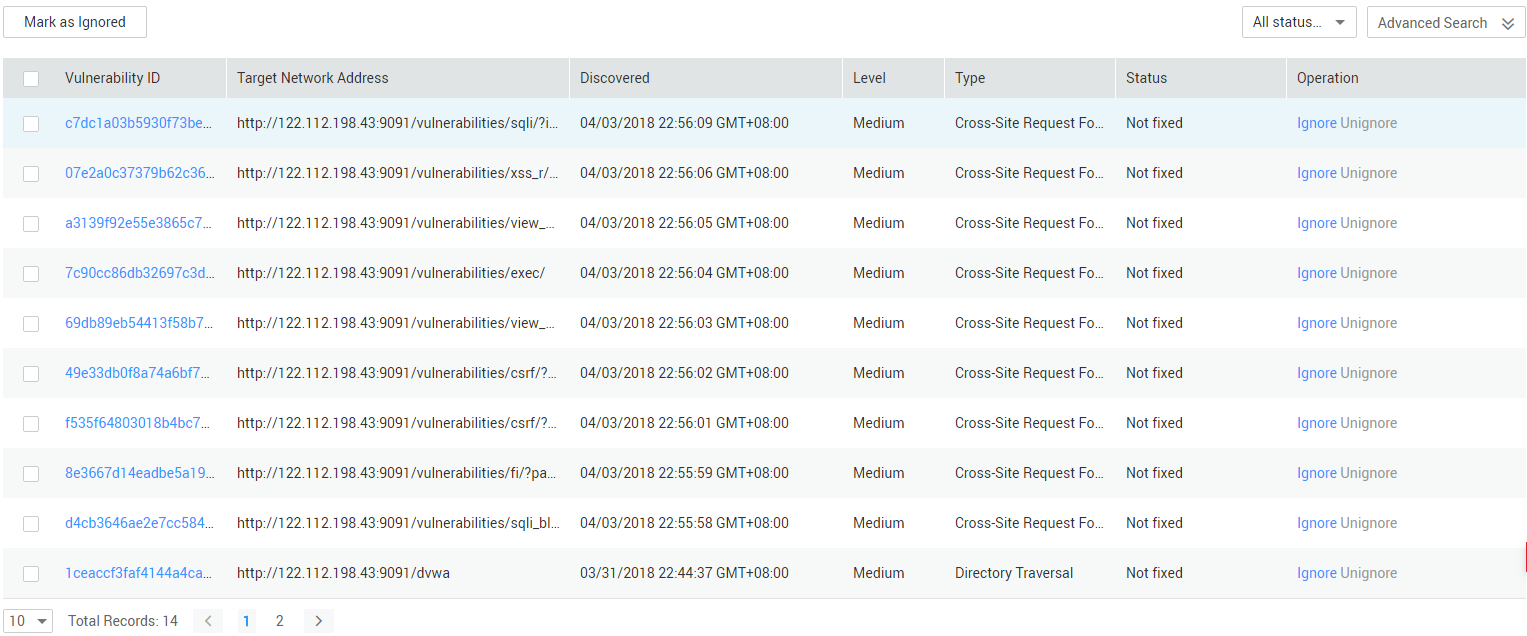
- Select the vulnerabilities to be ignored and click Mark as Ignored.
Figure 1 Marking vulnerabilities as ignored
 NOTE:
NOTE:
- Alternatively, in the row containing the desired vulnerability, click Ignore in the Operation column to mark a vulnerability separately.
- You can also click Ignore on the page displaying the details of the vulnerability to mark a vulnerability.
- In the displayed Ignore Vulnerability dialog box, specify the mandatory fields, and then click OK.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





