Viewing Incidents
Scenarios
An incident is a broad concept. It can include but is not limited to alerts. It can be a part of normal system operations, exceptions, or errors. In the O&M and security fields, an incident usually refers to a problem or fault that has occurred and needs to be focused on, investigated, and handled. An incident may be triggered by one or more alerts or other factors, such as user operations and system logs.
An incident is usually used to record and report historical activities in a system for analysis and audits. Currently, incidents are generated in the following ways:
- Adding an Incident: You can add incidents on the Incidents page. If you identify an attack or an issue that needs to be handled, you can add an incident on the Incidents page for tracking. Incidents need to be added one by one. If you need to add incidents in batches, import them.
- Importing Incidents: You can import incidents on the Incidents page. You can use lists to add incidents.
- Converting an Alert into an Incident or Associating an Alert with an Incident: You can convert alerts into incidents or associate alerts with incidents. This operation will generate new incidents. SecMaster analyzes alerts it aggregates from other services. During the analysis, if SecMaster detects attacks or serious threats, it converts such alerts into incidents or associates such alerts with certain incidents.
On the Incidents page in SecMaster, you can check the incident list for the last 360 days. The list contains the incident name, type, severity, and occurrence time of each incident. By customizing filtering conditions, such as the incident name, risk severity, and time, you can quickly query information about the specific incident.
This topic describes how to view incident information.
Relationships Between Alerts and Incidents
This section describes the meanings and differences between alerts and incidents.
- Meanings and differences between alerts and incidents
Viewing Incidents
- Log in to the SecMaster console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - In the navigation pane on the left, choose Workspaces > Management. In the workspace list, click the name of the target workspace.
Figure 1 Workspace management page

- In the navigation pane on the left, choose .
Figure 2 Accessing the Incidents page
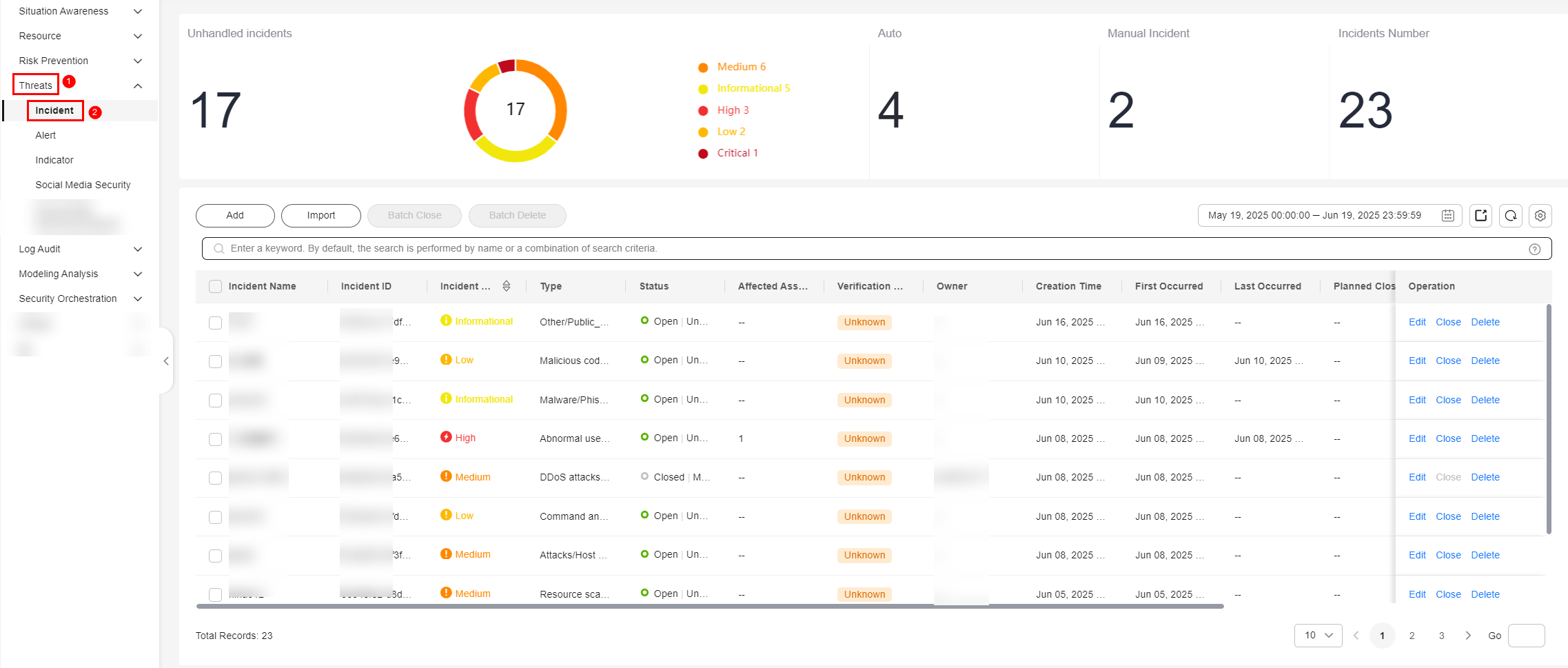
- On the Incidents page, view incident details.
Figure 3 Viewing an Incident

Table 2 Viewing an incident Parameter
Description
Unhandled Incidents
This area displays how many incidents are not handled within the time range you select in the current workspace. The unhandled incidents are displayed by severity.
Auto
This area displays how many incidents are automatically handled by playbooks within the time range you select in the current workspace.
Manual Incident
This area displays how many incidents are manually handled within the time range you select in the current workspace.
Incidents Number
This area displays how many incidents are reported within the time range you select in the current workspace.
Incident list
The list displays more details about each incident.
You can view the total number of incidents below the incident list. You can view a maximum of 10,000 incident records page by page. To view more than 10,000 records, optimize the filter criteria.
In the incident list, you can view the incident name, severity, source, and status.
To obtain overview of an incident, click the incident name. The Incident Overview panel is displayed on the right.
- On the incident overview panel, you can view the incident severity, status, and owner. You can change the incident severity and status from the Incident Severity and Status drop-down lists.
- On the Incident Overview panel, you can view incident handling suggestions, basic information, and associated information (including associated threat indicators, alerts, incidents, and attack information).
- To view incident details, click Incident Details in the lower right corner of the incident overview panel. The incident details page is displayed.
On the details page, you can view the incident timeline and attack information in addition to the information on the overview page. For example, you can view the first occurrence time of an incident, detection time, and attack process ID.
- On the incident overview or details page, you can associate or disassociate alerts, incidents, and indicators and view information about affected resources.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





