Enabling Disk Encryption for MRS Cluster Nodes
When creating an MRS cluster, you can choose whether to encrypt the system and data disks attached to the MRS cluster nodes. Keys used for encrypting system disks are provided by Key Management Service (KMS) in Data Encryption Workshop (DEW). You do not need to build and maintain the key management infrastructure.
When an encrypted disk is attached, EVS accesses KMS, and KMS sends the data key (DK) to the host memory for storage. EVS uses the plaintext DK to encrypt and decrypt disk I/Os. The plaintext DK is only stored in the memory of the host running the ECS and is not stored persistently on the storage media. If the custom key is deleted or disabled in KMS, the disk encrypted using the key can still use the plaintext DK stored in the host memory. However, if the disk is detached, the plaintext DK will be deleted from the memory, and the disk cannot be read or written. Before you re-attach this encrypted disk, ensure that the custom key is enabled.
For more information about DEW, see What Is DEW?
For more information about disk encryption, see Managing Encrypted EVS Disks.
Notes and Constraints
- To enable disk encryption during MRS cluster creation, you must have the Security Administrator and KMS Administrator permissions.
- System disk encryption is supported only in MRS 3.3.0-LTS or later.
- Disk encryption can be enabled only during cluster creation. This function cannot be enabled after the MRS cluster is created.
Configuring Disk Encryption for MRS Cluster Nodes
- Prepare the key used for disk data encryption.
Log in to the DEW console and create a key for user disk encryption on KMS. For details, see Creating a Custom Key.
You can create a key or use the default EVS encryption key evs/default that is automatically generated by the system.
- When creating an MRS cluster in custom config mode, enable advanced settings.
- Determine whether to enable system and data disk encryption based on your service requirements.
Figure 1 Configuring disk encryption
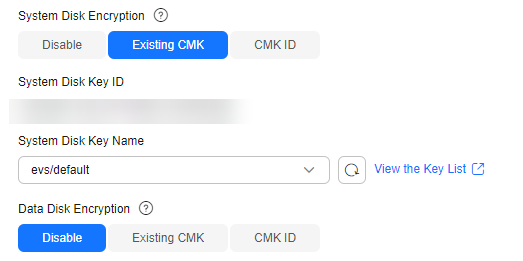
After system or data disk encryption is enabled, select an encryption key from KMS keys. Click View the Key List to enter the KMS page where you can create and manage keys.

If cloud disks are encrypted using a master key and the key is then disabled or scheduled for deletion, the disks can no longer be read from or written to, and data on these disks can never be recovered. Exercise caution when performing relevant operations.
- Configure other MRS cluster parameters to complete the cluster creation.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





