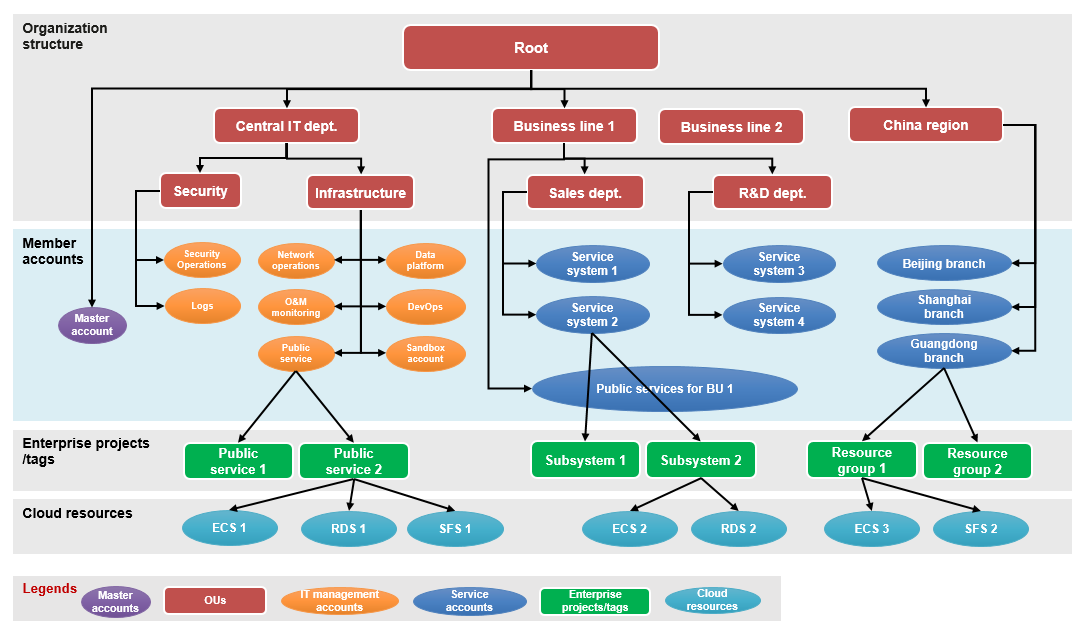
Organization and Account Design
The Landing Zone solution aims to build a secure, compliant, and scalable multi-account operating environment on the cloud. The first step is to plan the organization and account architecture. According to Conway's law, the account structure on Huawei Cloud should be consistent with the overall organization and business architecture of the company, but not necessarily identical. The mapping should only cover the OUs (such as subsidiaries, branches, and departments) that develop and maintain service systems or IT management systems, and the users of the IT resources.
For example, there is no need to create an OU that maps to the HR department if they do not manage, view, or operate any IT resources on the cloud. Also, there is no need to create a user with financial management permissions for financial personnel who are not responsible for cost accounting, analysis, and budget management of IT systems.
Huawei Cloud provides the following OUs and accounts in the architecture for your reference. You need to design the hierarchical structure of OUs and account groups on Huawei Cloud based on the business architecture, geographical area structure, and IT functions.
Service Account Planning
You can create OUs at different levels based on the business architecture. Each service OU can contain multiple service accounts, and each service account can be used for one or more service systems.
In principle, service accounts must be consistent with the business units defined by the organization. Business units can be subsidiaries, divisions, product lines, departments, project teams, or service systems. Finer granularity of business units matches higher-level lean governance requirements. Thanks to Huawei Cloud's experience in designing and implementing the Landing Zone solution for a large number of enterprise and government customers, we provided the following typical service account plans for your reference.
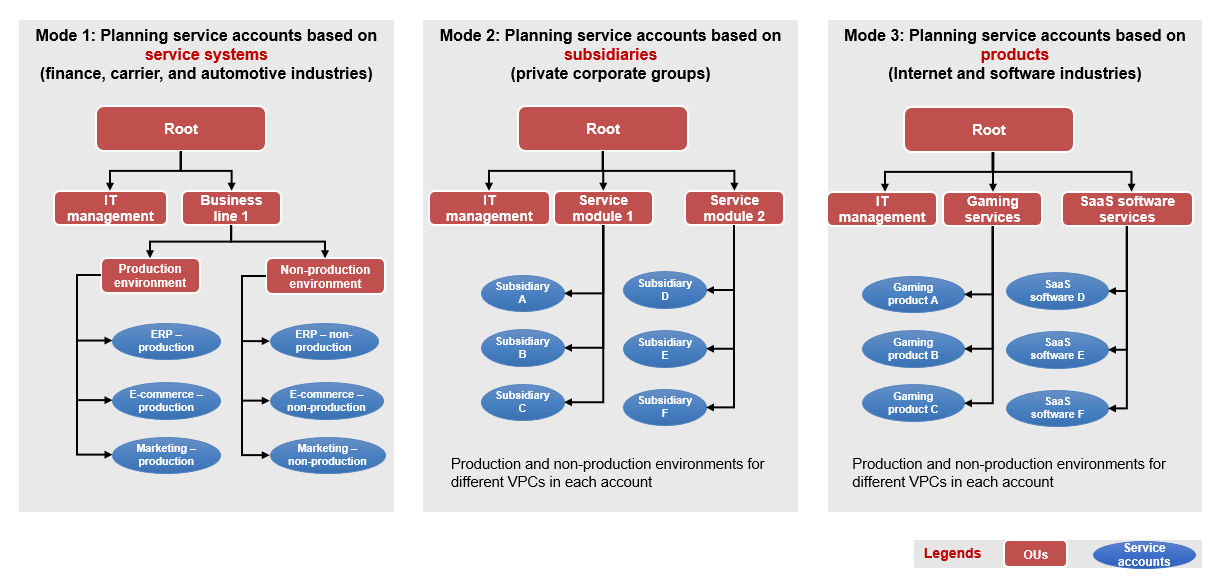
- In mode 1, service accounts are planned based on the service systems of each business unit. Service systems are isolated by member accounts. Member accounts are also used for isolating production and non-production environments. This mode is suitable for companies demanding strict control, such as financial institutions, carriers, and automakers.
- In mode 2, service accounts are planned based on subsidiaries. Each is an isolated service unit. Service systems of each subsidiary are deployed in the member accounts created for it. Within a member account, you can plan VPCs for production and non-production environments of each service system. This mode is suitable for private enterprise groups. They usually have dozens or even hundreds of subsidiaries. From the perspective of corporate governance, strict business isolation is required between subsidiaries, but service systems do not need to be isolated.
- In mode 3, service accounts are planned based on product planning. It breaks down business units into products. Products here refer to software systems that provide services for customers, such as live streaming systems, online games, and SaaS offerings. Different products are deployed and isolated in different member accounts. Within a member account, you can plan VPCs for production and non-production environments of each product. This mode is especially suitable for Internet and SaaS enterprises.
IT Management Account Planning
An OU is required for the central IT department of a company, and two lower-level OUs are required for security management and infrastructure management, respectively. IT management accounts are used to centrally manage all member accounts of the company.
In principle, the planning of IT management accounts must be consistent with the responsibilities and scale of the IT departments to maintain the benefits of each IT group. Thanks to Huawei Cloud's experience in designing and implementing the Landing Zone solution for a large number of enterprise and government customers, we provided the following typical IT management account plans for your reference.
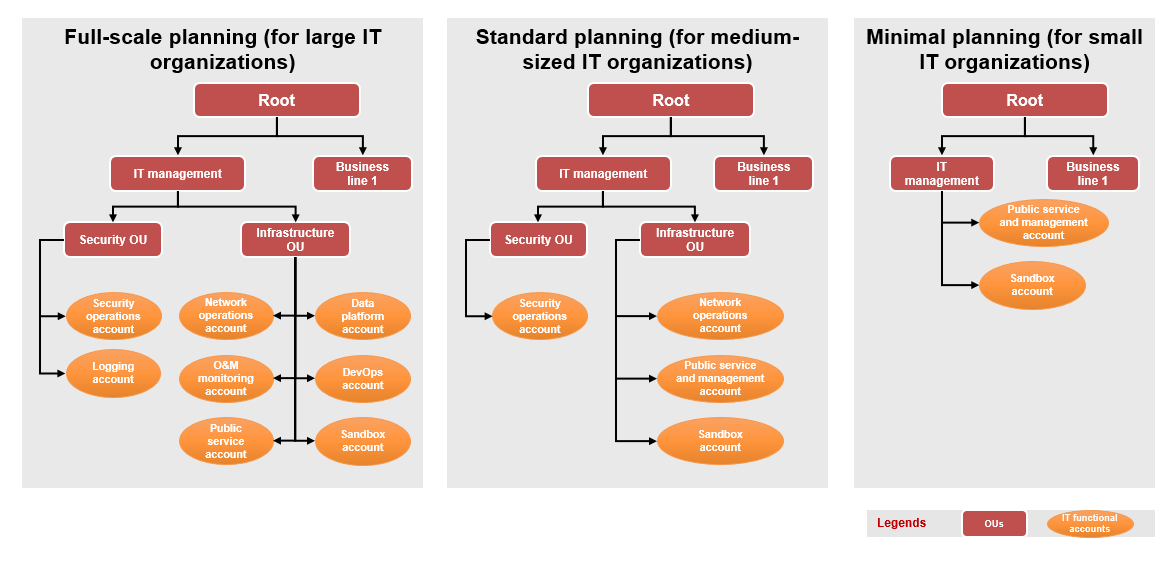
- The full-scale planning mode is suitable for large IT organizations. These IT organizations usually have dozens or hundreds of IT managers. Independent IT functional teams have been divided based on responsibilities such as security operations, log audit, network operations, O&M monitoring, public services, data platforms, and DevOps. To ensure separation of duties (SOD) within the IT department, map these IT functional teams to independent accounts. These accounts are used to fulfill independent IT responsibilities, so they are called IT management accounts (or functional accounts), as shown in the following table.
Table 1 IT management accounts Account
IT Function
Responsible Team
Recommended Cloud Service
Master account or management account
Centrally manage organizations and accounts, finances, governance policies, and identities and permissions.
CIO or IT director
Organizations, Resource Governance Center (RGC), Cost Center, and IAM Identity Center
Network operations account
Centrally deploy and manage enterprise network resources (including resources used for protecting network boundaries), and ensure VPC connectivity in a multi-account environment. In particular, manage ingress and egress in a unified manner for Internet and on-premises IDCs.
Network management team
Enterprise Router, Domain Name Service (DNS), NAT Gateway, Elastic IP (EIP), Virtual Private Cloud (VPC), Direct Connect, Cloud Connect, Virtual Private Network (VPN), Cloud Firewall (CFW), Web Application Firewall (WAF), and Anti-DDoS Service (AAD)
Public service account
Centrally deploy and manage the enterprise public resources, services, and application systems, and share them with other member accounts of the enterprise.
Public service management team
Image Management Service (IMS), SoftWare Repository for Container (SWR), Scalable File Service (SFS), Object Storage Service (OBS), in-house NTP servers, and in-house Anti-DDoS servers
Security operations account
Centrally manage and control security policies, rules, and resources in all accounts of the company, set security configuration baselines for member accounts of the company, and be responsible for information security of the entire company.
Security management team
Deploy services that support cross-account security management and control, such as SecMaster, Host Security Service (HSS), Data Security Center (DSC), Data Encryption Workshop (DEW), Cloud Certificate Manager (CCM), and CodeArts Inspector.
O&M monitoring account
Centrally monitor and maintain resources and applications under each member account, manage alarms, handle events, manage changes, and provide O&M security assurance measures
O&M team
Application Operations Management (AOM), Cloud Operations Center (COC), Log Tank Service (LTS), Application Performance Management (APM), and Cloud Bastion Host (CBH)
Logging account
Centrally store and view audit logs and security-related logs (such as VPC flow logs and OBS access logs) of all accounts.
Compliance audit team
Cloud Trace Service (CTS), Log Tank Service (LTS), Config, and Object Storage Service (OBS)
Data platform
Centrally deploy big data platforms and collect service data from other accounts to store, process, and analyze them on the data platforms.
Data processing team
Data lake, big data analysis platform, Data Ingestion Service (DIS), and DataArts Studio
Sandbox account
Test functions and governance policies of cloud services.
Test team
Resources and services to be tested
You can create more member accounts such as application integration accounts as needed.
- The standard planning mode is suitable for medium-sized IT organizations. These IT organizations usually have only 10 to 30 IT management engineers. They do not divide IT responsibilities as detailed as large IT organizations. However, they usually divide IT functions into independent security operations, network operations, and O&M monitoring teams. You are advised to create independent IT management accounts for security operations, network operations, public services, and O&M management, respectively. The security operations account in the standard planning mode combines the functions of the security operations account and logging account in the full-scale planning mode. In the standard planning mode, the public service and management accounts combine the functions of the O&M monitoring account, public service account, data platform account, and DevOps account in the full-scale planning mode.
- The minimal planning mode is suitable for small IT organizations with only a few IT management engineers. In this case, only a public service and management account needs to be created. This account combines the functions of the security operations account, logging account, network operations account, O&M monitoring account, public service account, data platform account, and DevOps account in the full-scale planning mode.
Region-based Account Planning
The planning of accounts for different regions is simple. You can divide different levels of OUs on Huawei Cloud based on the geographical area structure. You can create member accounts under each OU for countries or regions, and deploy local customer relationship management systems, customer service systems, and operations management systems under the member accounts. In the preceding reference architecture, the organization in the China region is mapped to an OU on Huawei Cloud, and independent member accounts are created for branches such as Beijing and Shanghai to carry local application systems.
Master Account Planning
A master account (also called management account) is created under the root of the organization by default. It is recommended that no cloud resources be deployed in this master account. You can use this master account to do the following:
- Organization and account management: Create and manage the organization structure and OUs, create member accounts for OUs, or invite existing accounts as the member accounts of OUs.
- Financial management: Centrally manage all accounts of a company, including unified budget management, cost analysis, bill management, fund management, coupon application, cost settlement, and invoicing.
- Policy management: Configure policies (including SCPs and tag policies) for OUs and member accounts, forcibly restrict user permissions (also for account administrators) under member accounts to mitigate security risks caused by excessive permissions. If you apply a control policy to a specific OU, the policy will apply to all member accounts and lower-level OUs in that OU.
- Identity management: Create users and user groups based on IAM Identity Center, or configure identity federation with an external identity provider (IdP). Then, configure permissions for these users to access cloud resources in multiple accounts based on the PoLP.
You can also use enterprise projects or tags to logically group resources under each member account. For example, you can map a subsystem of an application system to an enterprise project or tag on Huawei Cloud. You can also allocate costs and grant fine-grained permissions based on enterprise projects or tags.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





