How Do I Use a Certificate and an Authentication Credential to Access a Node?
You can perform the following operations to use a certificate and an authentication credential to access a node.
Prerequisites
- You have created a full node.
- You have obtained a key on Staking Launchpad. For details, see NES User Guide (Staking Nodes).
- You have downloaded a validator client. Check the Prysm Documentation or Lighthouse Documentation to download a client as required.
Procedure
- Create and obtain an authentication credential.
- On the NES console, choose Dedicated > Authentication Credential and click Create Credential.
- Describe the credential and set the access policy.
Figure 1 Creating a credential
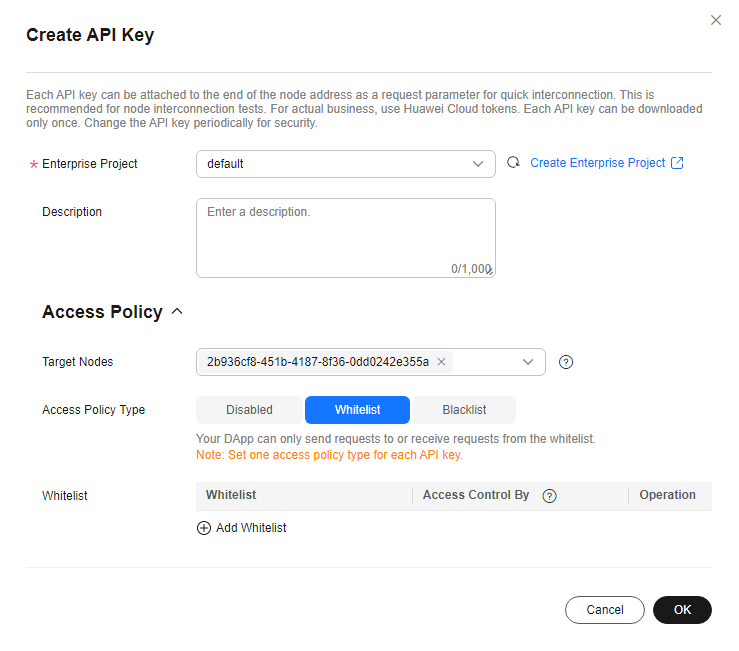
- Click OK. The credential is created and then automatically downloaded as a ZIP package.


Each credential can be downloaded only once. Change the credential periodically for security.
- Decompress the package and open the credential.csv file to obtain the credential.

- Start a staking node.
- Click a node ID.
Figure 2 Node ID
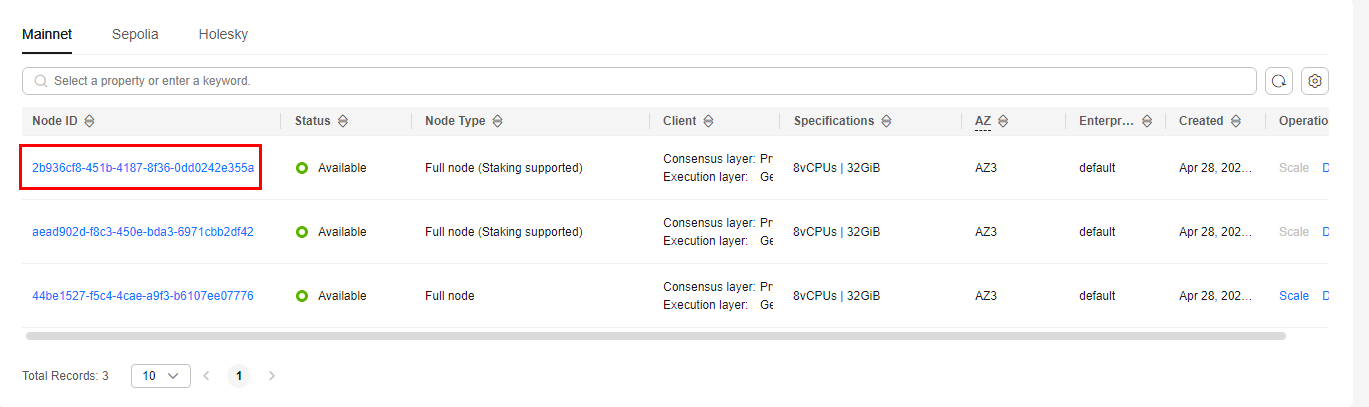
- Obtain the node information.
For a Prysm client, you can obtain its gRPC Endpoint and Node TLS Certificate.
For a Lighthouse client, you can obtain its HTTP Endpoint and Node TLS Certificate.Figure 3 Node details of a Prysm client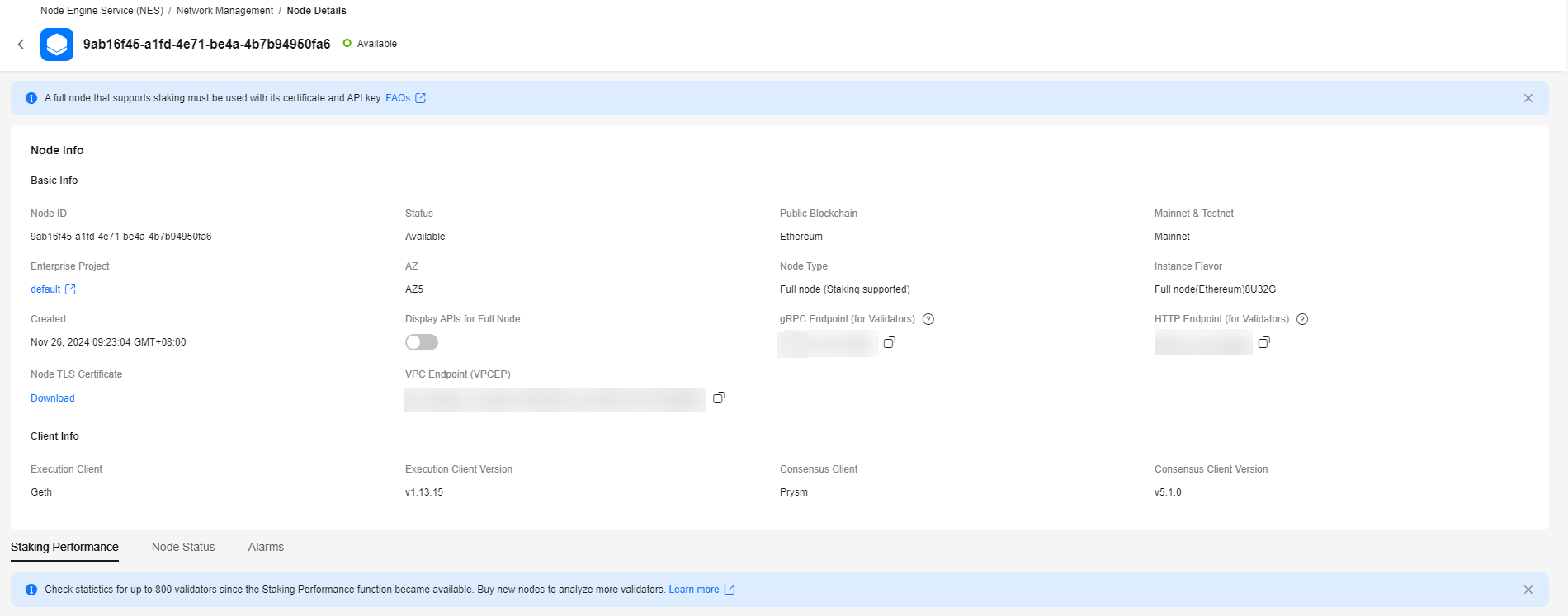
- Paste the key and TLS certificate to the hardware machine installed with the script.
For a Prysm client, run the following command to import the key to the keystore:
./prysm.sh validator accounts import --keys-dir=<YOUR_FOLDER_PATH> --< NETWORK >
NETWORK is the staking network and YOUR_FOLDER_PATH is the actual key file path.
For a Lighthouse client, run the following command to import the key to the keystore:
lighthouse --network < NETWORK > account validator import --directory < YOUR_FOLDER_PATH >
NETWORK is the staking network and YOUR_FOLDER_PATH is the actual key file path.
- After the key is imported, perform the following operations for a Prysm client and Lighthouse client, respectively.
For a Prysm client, run the prysm.sh file, configure the following parameters, and start the staking node.
- beacon-rpc-provider: the value of gRPC Endpoint
- grpc-headers: the authentication credential
- tls-cert: the relative path of Node TLS Certificate
Example:
./prysm.sh validator --beacon-rpc-provider=xx.xx.xx.xx:30002 --grpc-headers=credential=xxxxxxxxxxxxxxxxxxxxxx --tls-cert=ca.crt
For a Lighthouse client, run the lighthouse vc command, configure the following parameters, and start the staking node.
- network: the staking network
- suggested-fee-recipient: the suggested fee recipient
- beacon-nodes-tls-certs: the relative path of Node TLS Certificate
- beacon-nodes: the HTTP endpoint or credential information
lighthouse vc --network < **NETWORK** > --suggested-fee-recipient <**YourFeeRecipientAddress** > --beacon-nodes-tls-certs ca.pem --beacon-nodes https://xx.xx.xx.xx:30000/xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx

These parameters are mandatory for interconnecting Huawei Cloud nodes. Check the Prysm Documentation and Lighthouse Documentation to learn other parameters.
- Click a node ID.
- Monitor a staking node.
Click a node ID and click the Node Status tab page.Figure 4 Node status
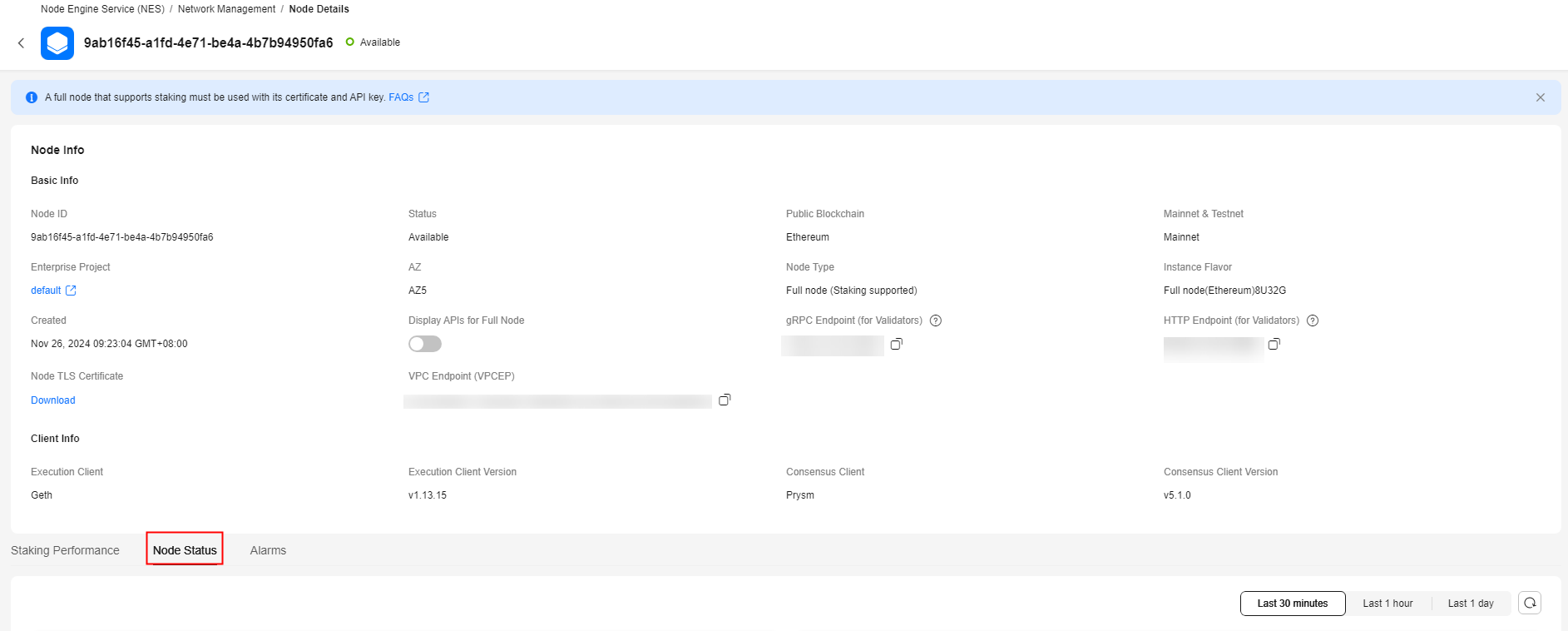

You need to monitor and perform O&M on the validator client where a staking node has been started. You can also enter the key on a page similar to the following to check the client execution.

Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





