How Do I Minimize the Permissions of a LakeFormation Agency?
Question
When enabling LakeFormation, the lakeformation_admin_trust IAM role is automatically created with default permissions including ReadOnlyAccess, VPCEndpoint Administrator, and lakeformation_admin_additional_domain. How can I modify the permissions of this role to the minimum required to reduce security risks?
Answer
Perform the following operations to grant the lakeformation_admin_trust agency the minimum permissions and delete the high-level permissions to reduce security risks.
After the modification is complete, only the minimum permissions required for using LakeFormation functions are retained.
- Create a custom policy.
- Log in to the IAM console.
- In the navigation pane on the left, choose Permissions > Policies/Roles.
- Create the LakeFormationIamAccess policy (if the policy already exists, skip this step).
Click Create Custom Policy. Set the parameters as follows and click OK.
- Policy Name: LakeFormationIamAccess
- Policy View: Select JSON.
- Policy Content: Enter the following content:
{ "Version": "1.1", "Statement": [ { "Effect": "Allow", "Action": [ "iam:groups:listGroupsForUser", "iam:agencies:listAgencies", "iam:roles:listRoles", "iam:agencies:getAgency", "iam:users:listUsers", "iam:permissions:listRolesForAgency", "iam:groups:listGroups", "iam:permissions:listRolesForAgencyOnProject", "iam:roles:getRole" ] } ] } - Description: Permissions required for LakeFormation to access IAM
- Create the LakeFormationObsAccess policy (if the policy already exists, skip this step).
Click Create Custom Policy. Set the parameters as follows and click OK.
- Policy Name: LakeFormationObsAccess
- Policy View: Select JSON.
- Policy Content: Enter the following content:
{ "Version": "1.1", "Statement": [ { "Effect": "Allow", "Action": [ "obs:bucket:ListAllMyBuckets" ] }, { "Effect": "Allow", "Action": [ "obs:bucket:GetLifecycleConfiguration", "obs:bucket:GetBucketLocation", "obs:bucket:PutLifecycleConfiguration", "obs:bucket:PutBucketAcl", "obs:bucket:HeadBucket", "obs:bucket:GetBucketAcl", "obs:bucket:ListBucket" ], "Resource": [ "OBS:*:*:bucket:*" ] }, { "Effect": "Allow", "Action": [ "obs:object:GetAccessLabel", "obs:object:PutObjectVersionAcl", "obs:object:DeleteAccessLabel", "obs:object:PutObjectAcl", "obs:object:PutAccessLabel", "obs:object:GetObjectVersion", "obs:object:GetObject", "obs:object:GetObjectVersionAcl", "obs:object:DeleteObject", "obs:object:DeleteObjectVersion", "obs:object:GetObjectAcl", "obs:object:PutObject" ], "Resource": [ "OBS:*:*:object:*" ] } ] } - Description: Permissions required for LakeFormation to access OBS
- Create the LakeFormationVpcAccess policy (if the policy already exists, skip this step).
Click Create Custom Policy. Set the parameters as follows and click OK.
- Policy Name: LakeFormationVpcAccess
- Policy View: Select JSON.
- Policy Content: Enter the following content:
{ "Version": "1.1", "Statement": [ { "Effect": "Allow", "Action": [ "vpc:routes:get", "vpc:routes:list", "vpc:vpcs:get", "vpc:subnets:get", "vpc:vpcs:list", "vpc:routes:create" ] } ] }
- Description: Permissions required for LakeFormation to access VPC
- Create the LakeFormationVpcepAccess policy (if the policy already exists, skip this step).
Click Create Custom Policy. Set the parameters as follows and click OK.
- Policy Name: LakeFormationVpcepAccess
- Policy View: Select JSON.
- Policy Content: Enter the following content:
{ "Version": "1.1", "Statement": [ { "Effect": "Allow", "Action": [ "vpcep:epserviceDesc:get", "vpcep:connections:list", "vpcep:endpoints:get", "vpcep:endpoints:delete", "vpcep:connections:update", "vpcep:endpoints:create", "vpcep:endpoints:list" ] } ] }
- Description: Permissions required for LakeFormation to access VPCEP
- Create the LakeFormationDnsAccess policy (if the policy already exists, skip this step).
Click Create Custom Policy. Set the parameters as follows and click OK.
- Policy Name: LakeFormationDnsAccess
- Policy View: Select JSON.
- Policy Content: Enter the following content:
{ "Version": "1.1", "Statement": [ { "Effect": "Allow", "Action": [ "dns:zone:list", "dns:recordset:update", "dns:zone:delete", "dns:recordset:create", "dns:recordset:list", "dns:zone:get", "dns:recordset:delete", "dns:zone:create" ] } ] }
- Description: Permissions required for LakeFormation to access DNS
- Add the created policies to lakeformation_admin_trust.
- In the navigation pane of the IAM console, choose Agencies. On the displayed page, search for lakeformation_admin_trust and click Authorize in the Operation column.
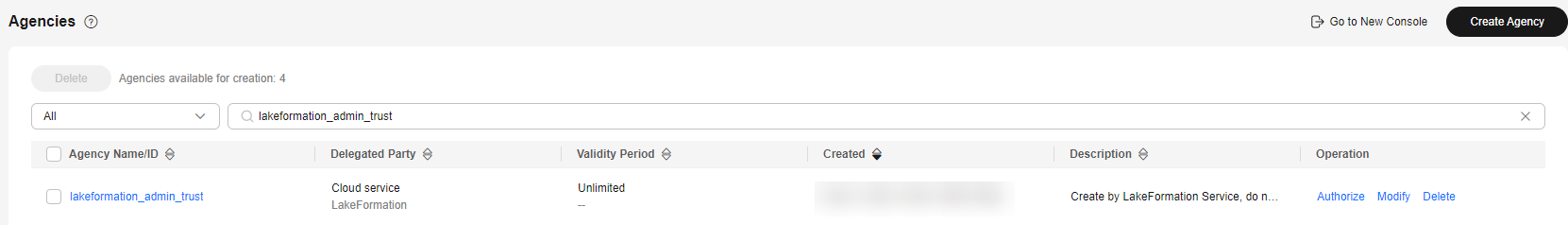
- On the displayed page, search for the minimum LakeFormation agency policies created in Step 1, select them, and click Next.
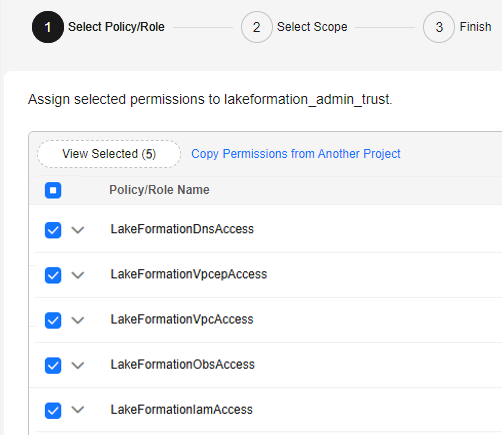
- On the Select Scope page, retain the default settings and click OK. Wait for 15 to 30 minutes for the new permissions to take effect.
- In the navigation pane of the IAM console, choose Agencies. On the displayed page, search for lakeformation_admin_trust and click Authorize in the Operation column.
- Delete high-level permissions.
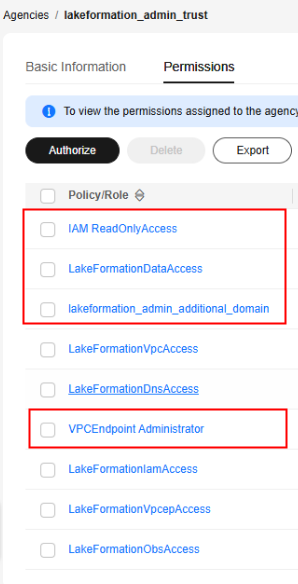
- After the new agency permissions take effect, in the navigation pane of the IAM console, choose Agencies. On the displayed page, search for lakeformation_admin_trust and click the agency name to go to the agency details page.
- Click the Permissions tab, select LakeFormationDataAccess, IAM ReadOnlyAccess, lakeformation_admin_additional_domain, and VPCEndpoint Administrator (if not available, ignore it) from the permission list, and click Delete above the list. In the displayed dialog box, click OK.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





