Using VPN and Cloud Connect to Enable Communication Between On-Premises Data Centers and Multiple VPCs on Huawei Cloud
Scenario
To use VPN to connect to Huawei Cloud, create a VPC in each Huawei Cloud region. Configure Cloud Connect connections to enable communication between your on-premises data center and VPC subnets in multiple regions.
Multiple VPCs in the same region can also be connected through Cloud Connect connections.
Prerequisites
- Prepared resources
- You have purchased VPN connections to connect your on-premises data center to the VPCs on Huawei Cloud.
- You have created VPCs in multiple regions, and the subnets of each VPC do not conflict with each other. The ECS service in VPCs is running properly.
- Topology
Figure 1 Using VPN together with Cloud Connect
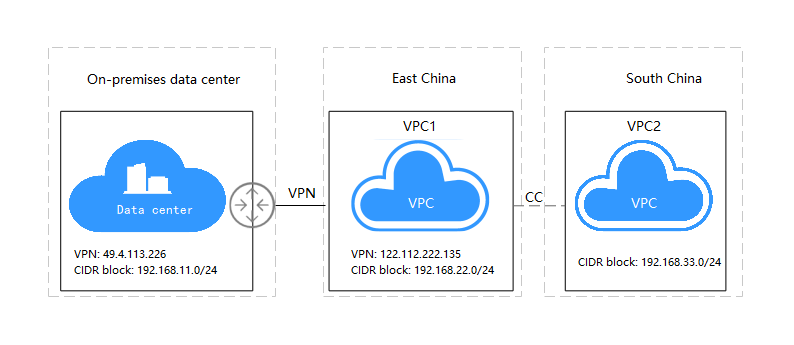
- Subnet of your on-premises data center: 192.168.11.0/24; VPN gateway IP address: 49.4.113.226
- VPC1 subnet: 192.168.22.0/24; VPN gateway address: 122.112.222.135
- VPC2 subnet: 192.168.33.0/24
- Configuration overview
Table 1 Configuration description On-premises Data Center
VPC1 (East China)
VPC2 (South China)
VPN connection subnet configuration
Local gateway: 49.4.113.226
Local subnet: 192.168.11.0/24
Remote subnet: 192.168.22.0/24
192.168.33.0/24
Remote gateway: 122.112.222.135
The local and remote gateway IP addresses in the on-premises data center and VPC1 are reversed.
The VPN configurations in the on-premises data center are consistent with those of VPC1.
VPN connection subnet configuration
Local gateway: 122.112.222.135
Local subnet: 192.168.22.0/24
192.168.33.0/24
Remote gateway: 49.4.113.226
Remote subnet: 192.168.11.0/24
Cloud Connect network instance configuration
Network instance: 192.168.22.0/24
192.168.11.0/24
Cloud Connect network instance configuration
Network instance: 192.168.33.0/24
Cloud Connect network instances can be configured at any region. You can check the route information to verify the network instance configuration.
- Configuration roadmap
- Use a cloud connection to connect VPC1 in East China to VPC2 in South China.
- Keep the local subnet of the VPN connection in your on-premises data center unchanged, and change the remote subnet to 192.168.22.0/24 and 192.168.33.0/24.
- Change the local subnet of the VPN connection in VPC1 to 192.168.22.0/24 and 192.168.33.0/24, and keep the remote subnet unchanged.
- The cloud connection of VPC1 updates the VPC CIDR blocks and adds 192.168.11.0/24 to the VPC subnet.
- The network information of VPC2 remains unchanged.
- Configure the inter-region bandwidth.
- Verify the route information of the cloud connection.
Procedure
- Create a cloud connection.
- Log in to the console. Click Service List in the upper left corner. Under Networking, select Cloud Connect. In the navigation pane on the left, choose Cloud Connections. On the displayed page, click Create Cloud Connection in the upper right corner.
- Configure required parameters and click OK.
Figure 2 Create Cloud Connection
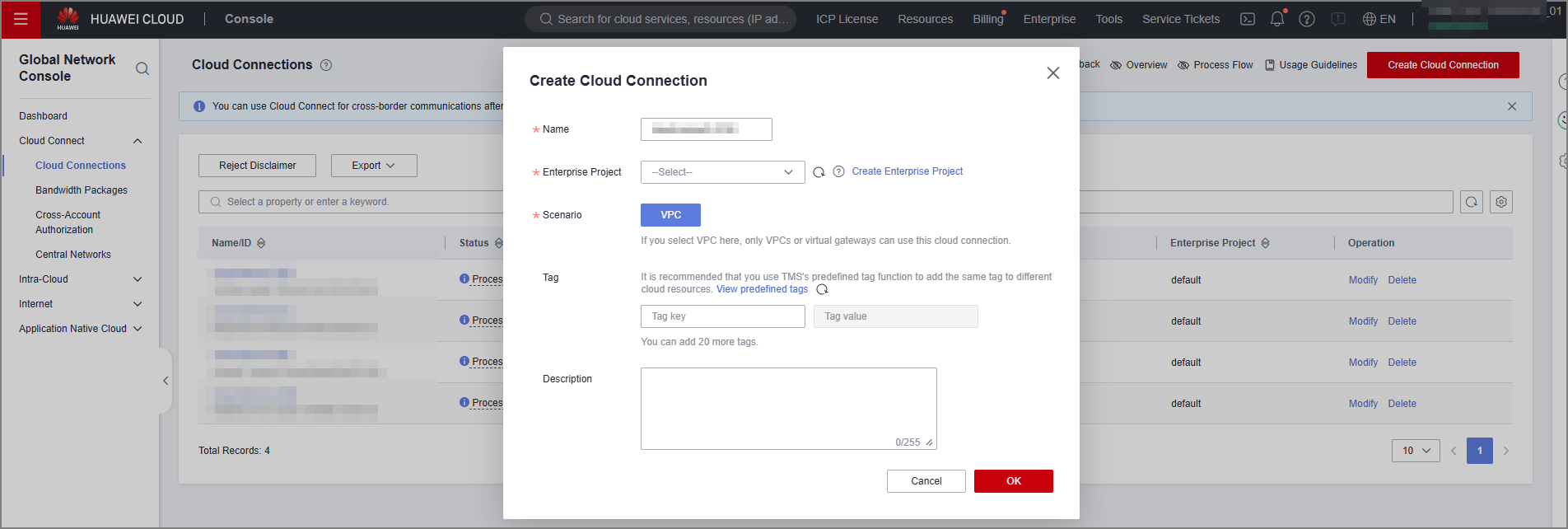
You can create a cloud connection in any region where the VPC is located. If you have two VPCs in the same region, you can use a VPC peering connection (with a lower latency) or a cloud connection to connect the two VPCs. If you have more than two VPCs, use cloud connections to connect them.
- Click the cloud connection name.
- Select the Network Instances tab and click Load Network Instance.
Configure required parameters and click OK.Figure 3 Loading network instance 1
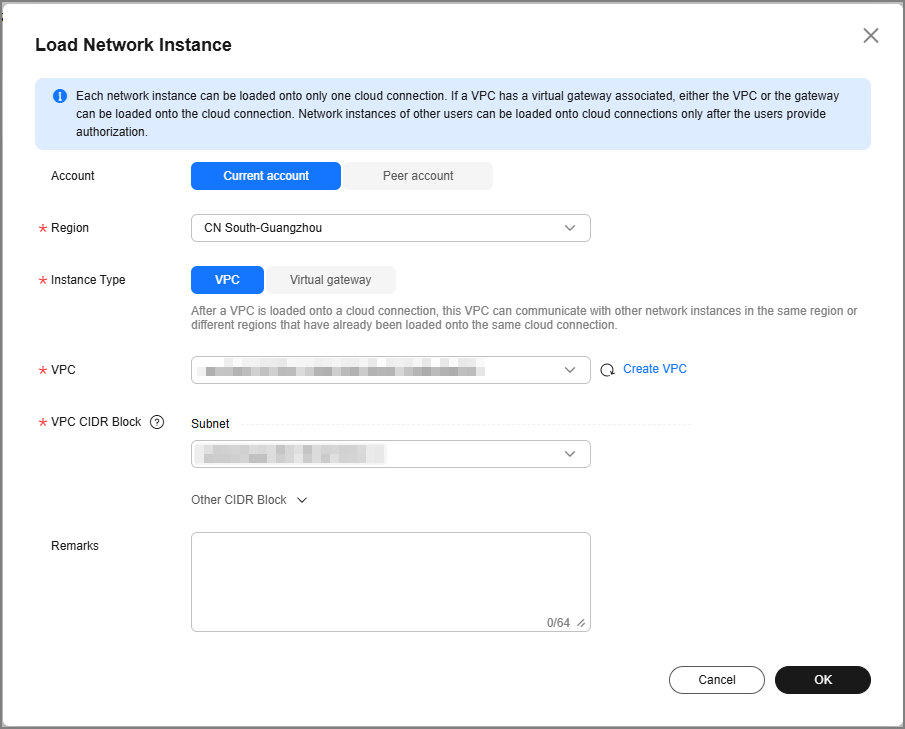
- Select CN South-Guangzhou for Region. Select VPC2. You can select some or all subnets for Subnet. You can also add VPC subnets by customizing CIDR blocks.
Add VPC1 in the CN East-Shanghai1 region and add its network configuration.
Figure 4 Loading network instance 2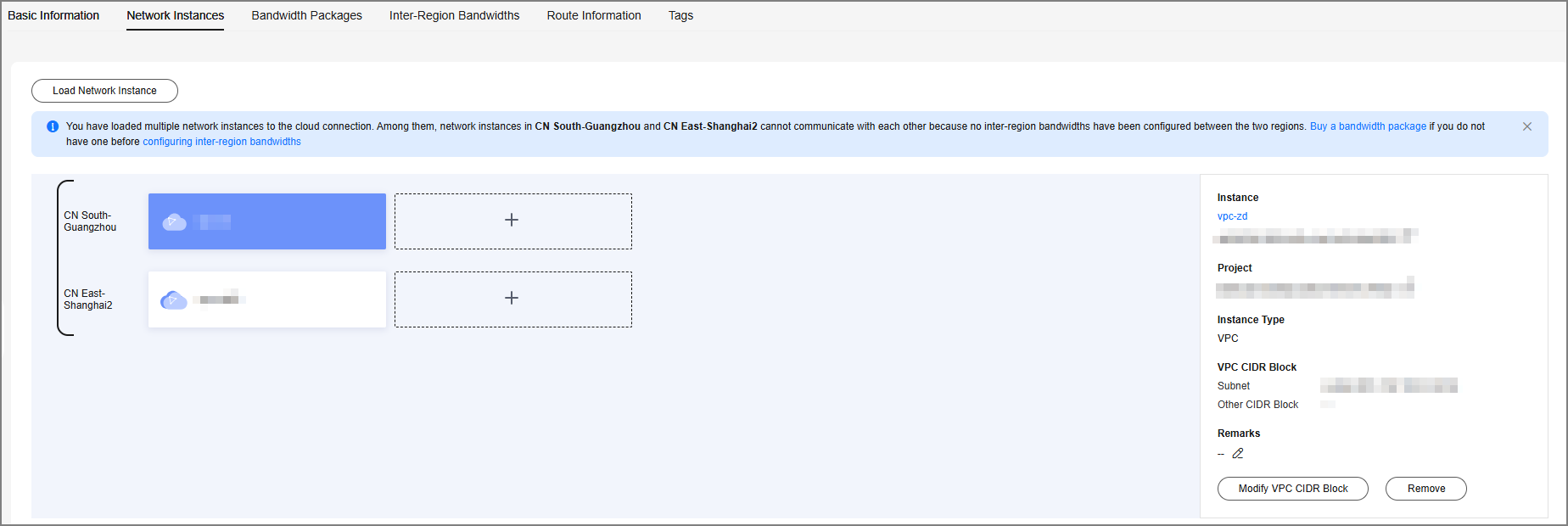
- A cloud connection can be created using the same account or different accounts. If you want to create a cross-account connection, obtain authorization first.
- The system does not verify custom subnets.
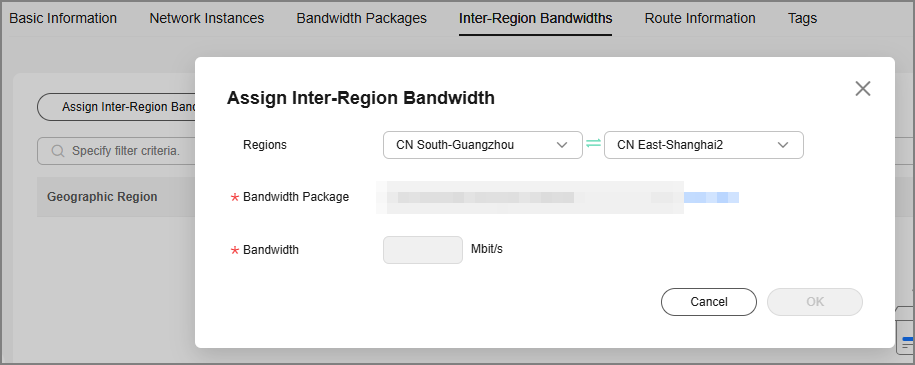
- Click the Inter-Region Bandwidths tab, and click Configure Inter-Region Bandwidth. If there are multiple regions, allocate the total bandwidth of the cloud connection among multiple regions based on the bandwidth usage in each region. In this example, the bandwidth is used for interconnection between two regions.
Figure 5 Configuring the inter-region bandwidth
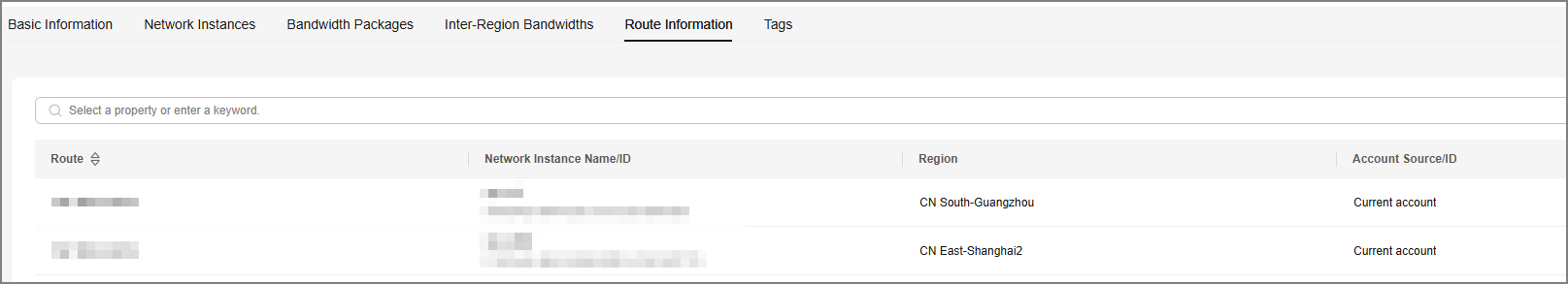
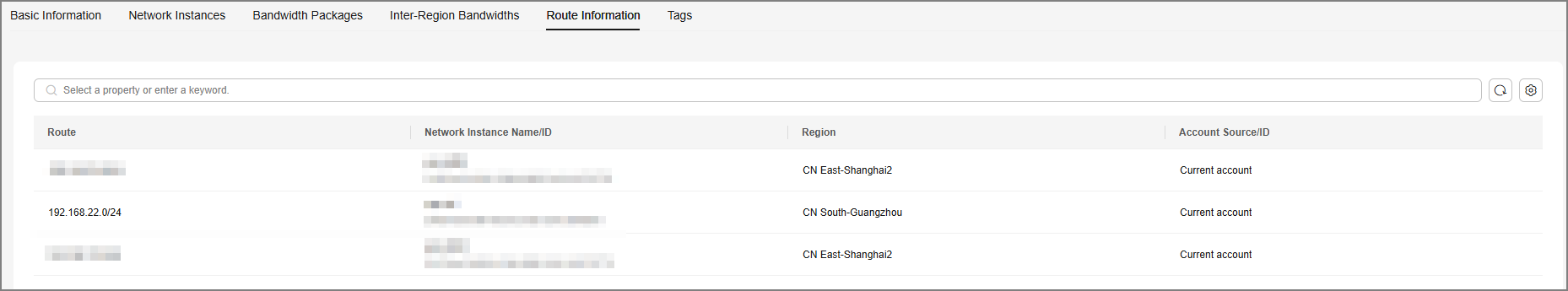
- To verify the route information, select the Route Information tab.
Route information for interconnection between regions is displayed. The subnets in the route are the subnets that are interconnected through the cloud connection. At this time, the subnets of VPC1 and VPC2 can access each other.Figure 6 Verifying the route information
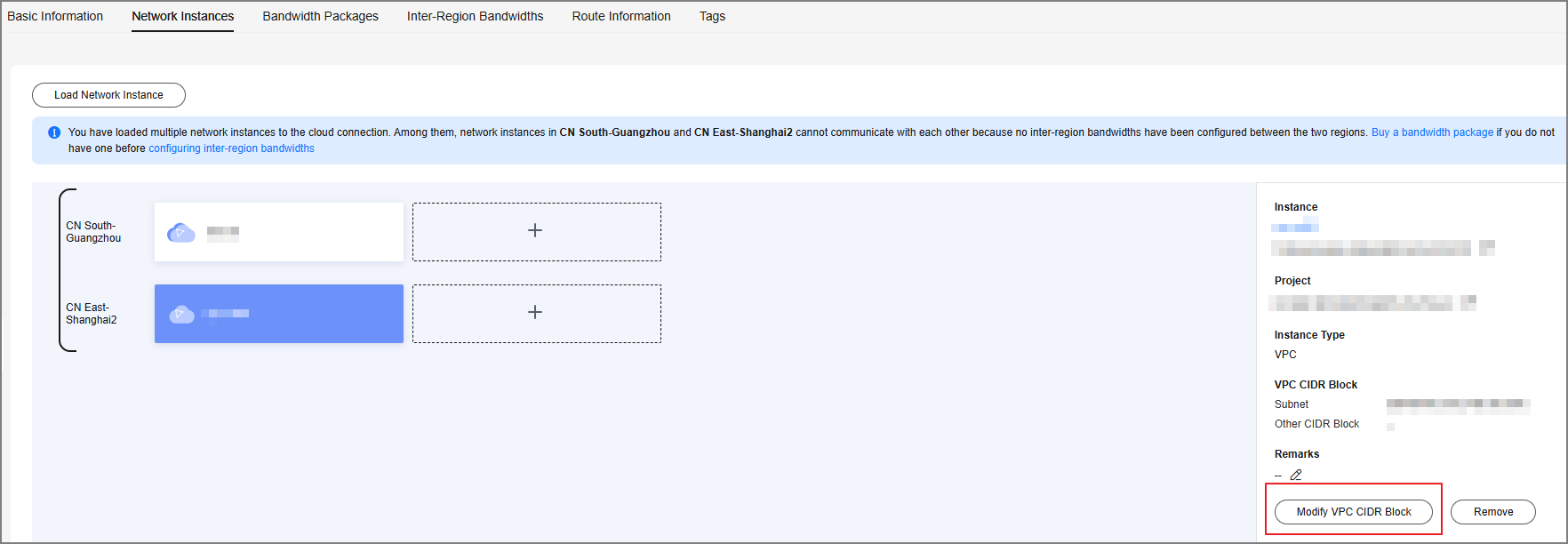
- Modify VPC CIDR blocks.
When you configure a network instance for the cloud connection between VPC1 and VPC2, the subnet connected to VPN is also considered to be connected to VPC1. Therefore, you need to modify the network instance of VPC1.
- Click the cloud connection name to go to the cloud connection details page.
- On the Network Instances tab page, select a network instance in the CN East-Shanghai2 region.
- Click Modify VPC CIDR Block on the right of the page.
Figure 7 Modifying the VPC CIDR block
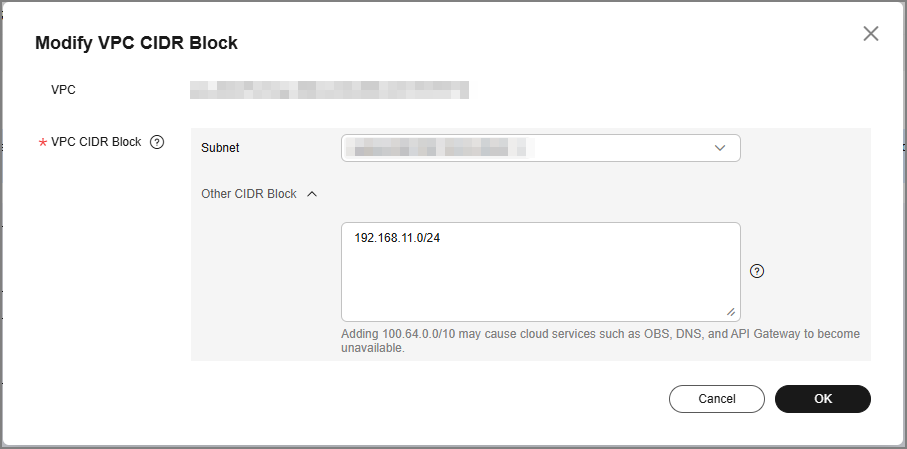
- For Other CIDR Block in the Advanced Settings area, enter the CIDR block to which VPC1 connects through the VPN connection and click OK.
Figure 8 Modifying the VPC CIDR block
- Verify the configuration update on the Route Information tab page.
Figure 9 Verifying the configuration update
- Update VPN configurations.
After VPC1 and VPC2 are connected through the cloud connection, the VPN subnet between user data center network and VPC1 changes. From the perspective of the VPN connection, the local subnet of VPC1 should contain the subnet of VPC1 and the subnet of VPC2 that is connected through the cloud connection, and the remote subnet of the client VPN also needs to be adjusted accordingly.
- On-premises data center: Keep the local subnet unchanged, and add the subnet of VPC2 as a remote subnet, which is 192.168.33.0/24 in this example.
- VPC1: Add a subnet of VPC2 to the local subnet. In this example, the subnet is 192.168.33.0/24, and the remote subnet remains unchanged.
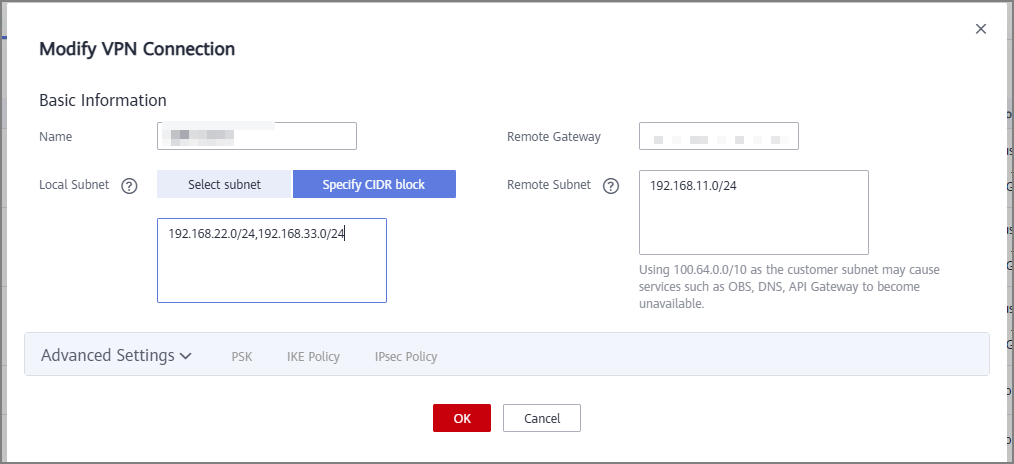
- Choose Virtual Private Network > Classic, locate the VPN connection created for VPC1, and choose More > Modify in the Operation column.
- On the Modify VPN Connection page, select Specify CIDR block for Local Subnet and enter the subnets of VPC1 and VPC2. Use a comma (,) to separate the two subnets. Keep the remote subnet and other information unchanged.
Figure 10 Modifying the VPN connection
- Modify the remote subnet in the VPN configuration.
Add the VPC1 and VPC2 subnets on Huawei Cloud to the remote subnet configuration of the VPN connection. Retain other configurations.
Verification
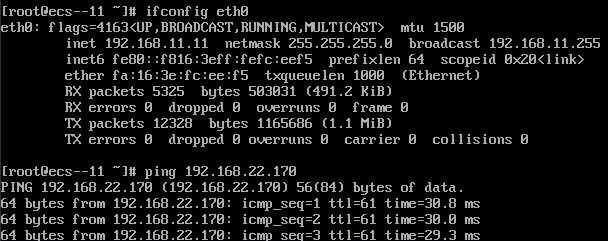
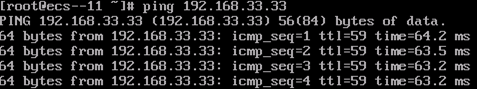
In this environment, the user data center, VPC1, and VPC2 each has three ECSs deployed. The IP addresses of the three ECSs are 192.168.11.11, 192.168.22.170, and 192.168.33.33, respectively. ECS1 (192.168.11.11) can communicate with ECS2 (192.168.22.170) through VPN. ECS3 (192.168.33.33) cannot communicate with other two ECSs. After a cloud connection is established, ECS3 can communicate with ECS2 but cannot communicate with ECS1.
After updating the VPC CIDRs and VPN configurations, ECS1, ECS2, and ECS3 can communicate with each other.
- On-premises data center
ECS1 can access ECS2 in the VPC1 subnet through the VPN connection.
ECS1 can access ECS3 in the VPC2 subnet.
- VPC1 on Huawei Cloud
ECS2 in the VPC1 subnet can access ECS1 in the subnet of your on-premises data center.
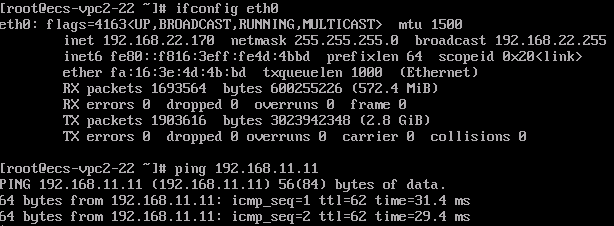
ECS2 in the VPC1 subnet can access ECS3 in the VPC2 subnet.
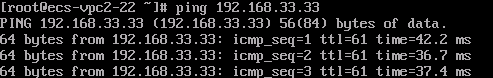
- VPC2 on Huawei Cloud
ECS3 in the VPC2 subnet can access ECS2 in the VPC1 subnet.
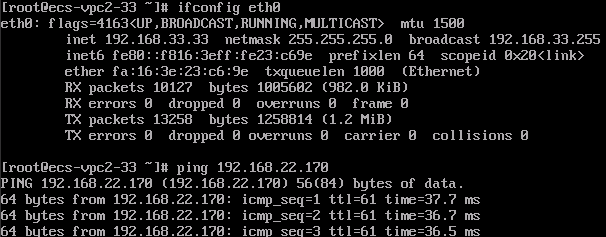
ECS3 in the VPC2 subnet can access ECS1 in the subnet of your on-premises data center.
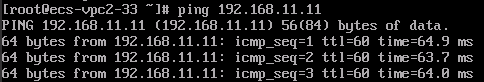
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





