Deploying the MgC Agent
Before using the big data functions, you need to deploy the MgC Agent on a server that can access your metadata source.
The MgC Agent does not support automatic restart. Do not restart the MgC Agent during task execution, or tasks will fail.
Preparations
- Prepare a Linux server for installing the MgC Agent in the source intranet environment. The Linux server must:
- Be able to access the Internet and the domain names of MgC, IoTDA, and other cloud services. For details about the domain names to be accessed, see Domain Names.
- Allow outbound traffic on port 8883 if the server is in a security group.
- Run CentOS 8.X.
- Have at least 4 CPUs and 8 GB of memory. If you want to use big data verification, the server must have at least 8 CPUs and 16 GB of memory.

Do not install the MgC Agent on a source server to be migrated.
- High resource consumption: The MgC Agent consumes CPU and memory resources during collection and migration. If a large number of migration tasks are performed by the MgC Agent, services on the source server may be affected.
- Port occupation: The MgC Agent occupies some ports on the server, which may affect services running on it.
- Have rng-tools installed. To check whether this tool is installed, run the following command on the Linux server:
rpm -qa | grep rng-tools
If no rng-tools-related information is displayed, rng-tools is not installed on the server. Run the following command to install rng-tools:yum -y install rng-tools
- Not have any antivirus or protection software enabled. This type of software may stop the MgC Agent from executing migration commands, resulting in migration failures.
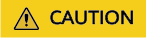
- Allow TCP traffic on port 27080. You can do that by adding an inbound rule to the security group of the Linux server. For the rule, set Source to the IP address of the Windows server you use to remotely access the MgC Agent console.
- Sign up for a HUAWEI ID and enable Huawei Cloud services, and obtain an AK/SK pair for the account.
- Create a migration project on the MgC console.
Installing the MgC Agent
- Sign in to the MgC console from the Linux server you prepared.
- In the navigation pane on the left, choose MgC Agents.
- In the Linux area, click Download Installation Package or Copy Download Command to download the MgC Agent installation program to the Linux server.
- Decompress the MgC Agent installation package.
tar zxvf Edge.tar.gz
- Go to the scripts directory in the decompressed MgC Agent directory.
cd Edge/scripts/
- Run the MgC Agent installation script.
./install.sh
- Enter a private IP address of the Linux server. The IP address will be used for accessing the MgC Agent console. If the entered IP address is not used by the Linux server, the system will prompt you whether to use any public IP address of the Linux server as the MgC Agent access address.
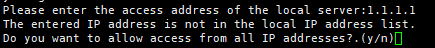
- Check if the message shown in the following figure is displayed. If it is, the MgC Agent for Linux has been installed. The port in the following figure is for reference only. Note the actual port returned. Generally, the port is 27080.
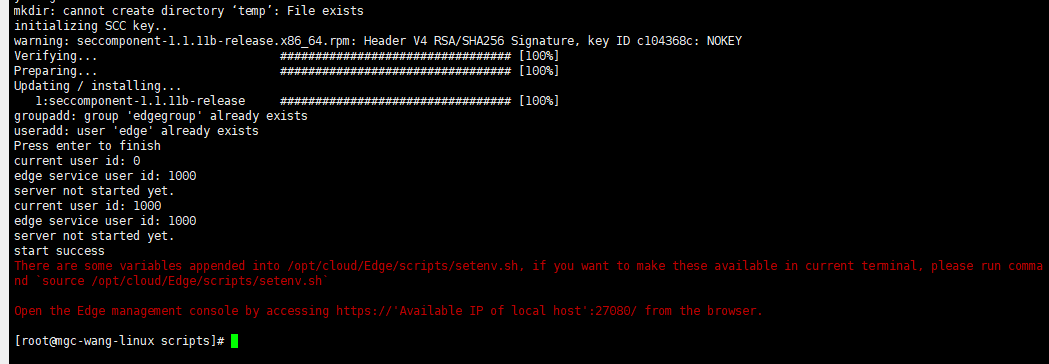
Update environment variables.
source /opt/cloud/Edge/scripts/setenv.sh
- On the Windows server for which an inbound rule is added to the security group of the server where the MgC Agent is installed, open a browser and enter https://<IP-address-entered-in-step-7>:<port-obtained-in-step-8> in the address box. For example, if the IP address entered in step 7 is 192.168.x.x and the port returned in step 8 is 27080, the MgC Agent access address is https://192.168.x.x:27080. Open the MgC Agent console, enter the AK/SK pair of your Huawei Cloud account, select a region, and click Log In.
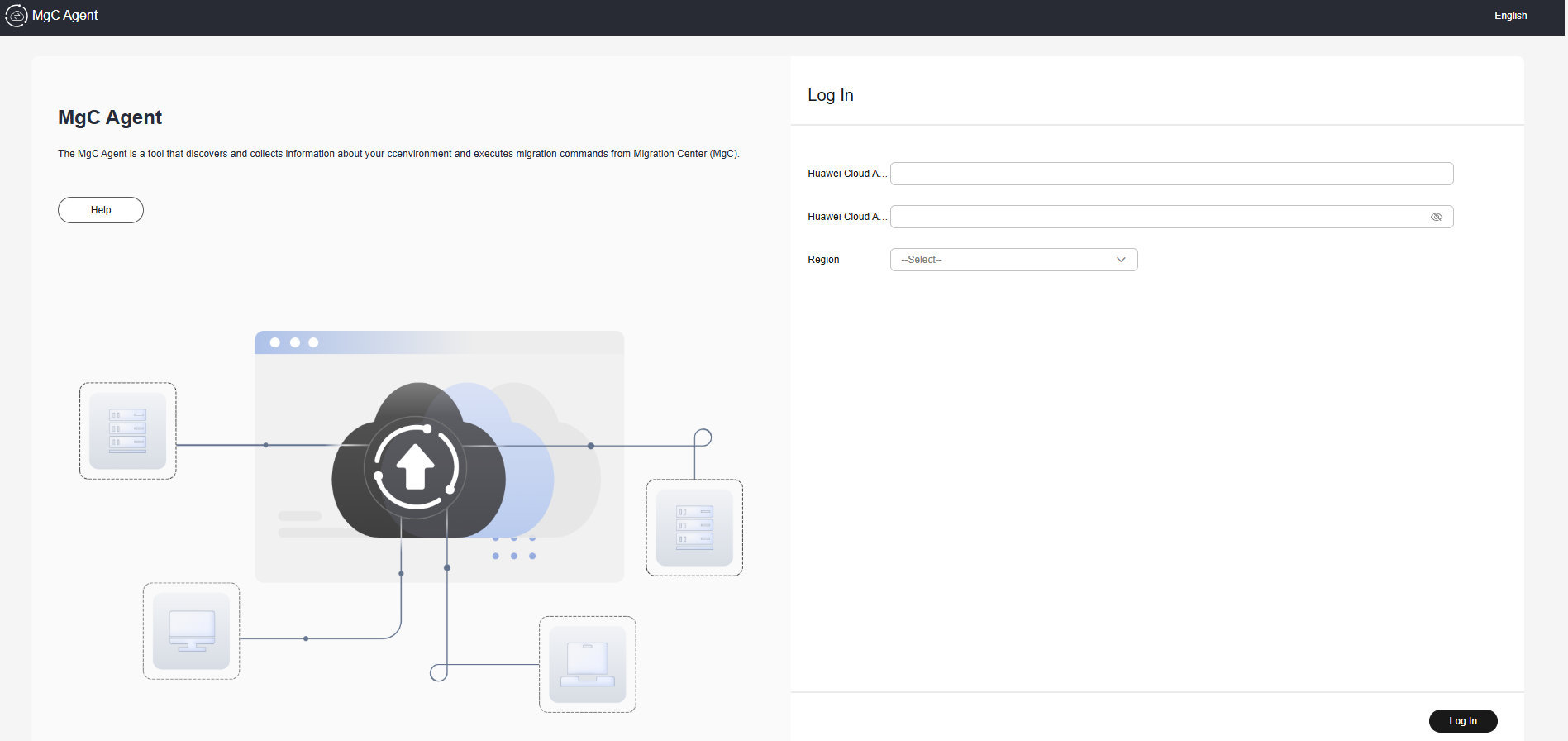

If there are access problems, check the IP address entered in the address box and the inbound rule settings of the security group of the Linux server with the MgC Agent installed.
Connecting the MgC Agent to MgC
- Use the AK/SK pair of your Huawei Cloud account to log in to the MgC Agent console.
- On the Overview page, click Connect in the upper right corner. The Connect to MgC page is displayed on the right.
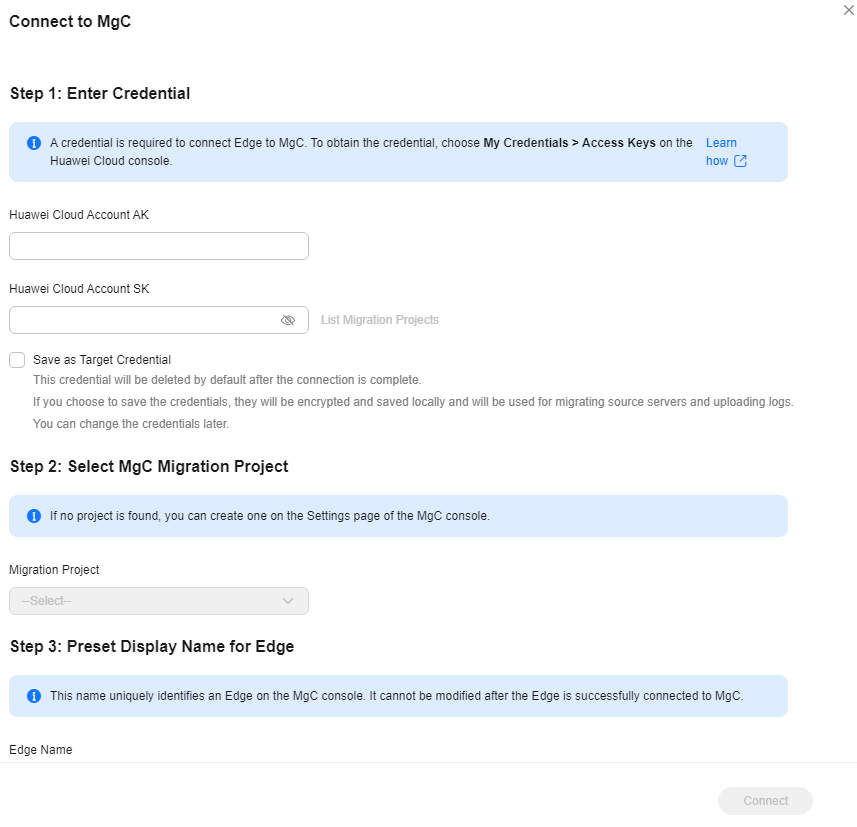
- In Step 1: Enter Credential, enter the AK/SK pair of the Huawei Cloud account used to access MgC and click List Migration Projects. After the MgC Agent is authenticated using the entered AK/SK pair, you can go to the next step. If the system displays a message indicating that the AK/SK pair is incorrect, try to rectify the fault by following the instructions in What Can I Do If the AK/SK Verification Fails?

If your source servers need to be migrated, the entered AK/SK pair must have permissions to use SMS. For details, see SMS Custom Policies.
Determine whether to save the entered AK/SK pair as the target credential which will be used for migrating your workloads to Huawei Cloud.
- If you select No, the entered AK/SK pair will be deleted after the MgC Agent is connected to MgC.
- If you select Yes, the entered AK/SK pair will be encrypted and saved locally after the connection to MgC is established. When you migrate workloads to Huawei Cloud, the AK/SK pair will be delivered to SMS-Agent on the source servers for executing the migration.
- In Step 2: Select MgC Migration Project, select a migration project from the project drop-down list. The MgC Agent will report the collected information about your source resources to this project.
- In Step 3: Preset MgC Agent Name, specify a name for the MgC Agent, which will be displayed on the MgC console, and click Connect. Confirm the connection to MgC, and click OK.

After the MgC Agent is connected to MgC, the name you specified here cannot be modified.
- If Connected shows up on the overview page, the connection to MgC is successful.
Adding Resource Credentials
You can add credentials of the following types of resources to the MgC Agent: private clouds, servers, big data clusters, and containers. For details about the authentication methods supported for each resource type, see Table 1.
|
Resource Type |
Authentication Method |
Description |
|---|---|---|
|
Public cloud |
|
|
|
Private cloud |
Username/Password |
Enter the username and password for logging in to the source private cloud. |
|
Databases |
Username/Password |
Enter the username and password of the database. |
|
Big data - Executor |
Username/Password |
Enter the username and password for logging in to the server deployed as an executor. Then specify Network Range, which can be a single IP address or an IP address range. The value can be:
|
|
Big data - Hive Metastore |
Username/Key |
Upload the core-site.xml, hivemetastore-site.xml, hive-site.xml, krb5.conf, and user.keytab files. For details about how to obtain the certificate file, see How Do I Obtain the Hive Metastore Credential Files? |
|
Big data - Data Lake Search (DLI) |
AK/SK |
Enter the AK/SK pair of the Huawei Cloud account. For details about how to obtain an AK/SK pair, see How Do I Obtain the AK/SK and Project ID? |
|
Big Data - MaxCompute |
AK/SK |
Enter the AK/SK pair of the source Alibaba Cloud account. For details about how to obtain the key pair, see Viewing the Information About AccessKey Pairs of a RAM User. |
|
Big data - Doris |
Username/Password |
Enter the username and password of the Doris database. |
|
Big data - HBase |
Username/Key |
The preceding configuration files are usually stored in the conf subdirectory of the Hadoop and HBase installation directories. |
|
Big data - ClickHouse |
Username/Password |
Enter the username and password of the ClickHouse database. |
|
Windows server |
Username/Password |
Enter the username and password for logging in to the server. Then specify Network Range, which can be a single IP address or an IP address range. The value can be:
|
|
Linux server |
|
Then specify Network Range, which can be a single IP address or an IP address range. The value can be:
|
|
Container |
Configuration file |
The configuration file must be a .json or .yml file. |
- Use the AK/SK pair of your Huawei Cloud account to log in to the MgC Agent console.
- In the navigation pane, choose Agent-based Discovery > Credentials.
- Click Create Certificate above the list.
- Select a resource type and authentication method as prompted. Specify a credential name, enter your credentials, and click Confirm.
- If the MgC Agent is not connected to MgC, the added resource credentials can be used for deep collection.
- If the MgC Agent is connected to MgC, the added resource credentials will be automatically synchronized to MgC.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






