Load Balancing Algorithms
Overview
Load balancers receive requests from clients and forward them to backend servers in one or more AZs. Each load balancer has at least a listener and a backend server. The load balancing algorithm you select when you create the backend server group determines how requests are distributed.
ELB supports the following load balancing algorithms: weighted round robin, weighted least connections, source IP hash, and connection ID.
The default load balancing algorithm is weighted round robin. You can change it to a different algorithm if needed.
You can select the load balancing algorithm that best suits your needs.
|
Load Balancing Algorithm |
Description |
|---|---|
|
Weighted round robin |
Routes requests to backend servers in sequence based on their weights. |
|
Weighted least connections |
Routes requests to backend servers with the smallest connections-to-weight ratio. |
|
Consistent hashing
|
Calculates the request fields using the consistent hashing algorithm to obtain a hash value and routes requests with the same hash value to the same backend server, even if the number of backend servers in the backend server group changes.
|
How Load Balancing Algorithms Work
Dedicated load balancers support four load balancing algorithms: weighted round robin, weighted least connections, source IP hash, and connection ID.
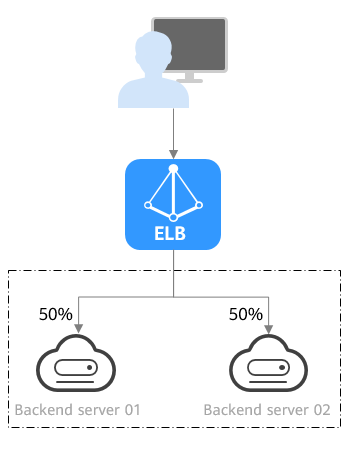
Figure 1 shows an example of how requests are distributed using the weighted round robin algorithm. Two backend servers are in the same AZ and have the same weight, and each server receives the same proportion of requests.
|
Description |
Requests are routed to backend servers in sequence based on their weights. Backend servers with higher weights receive proportionately more requests, whereas equal-weighted servers receive the same number of requests. |
|---|---|
|
When to Use |
This algorithm is typically used for short connections, such as HTTP connections.
|
|
Disadvantages |
|
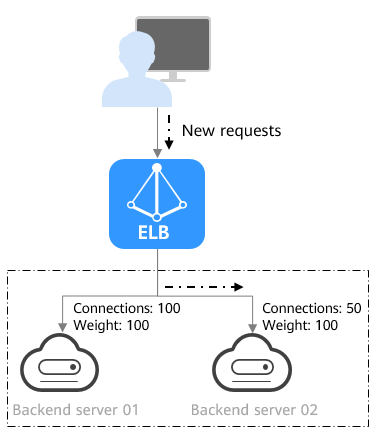
Figure 2 shows an example of how requests are distributed using the weighted least connections algorithm. Two backend servers are in the same AZ and have the same weight, 100 connections have been established with backend server 01, and 50 connections with backend server 02. New requests are preferentially routed to backend server 02.
|
Description |
In addition to the number of active connections established with each backend server, each server is assigned a weight based on their processing capability. Requests are routed to the server with the lowest connections-to-weight ratio. |
|---|---|
|
When to Use |
This algorithm is often used for persistent connections, such as connections to a database.
|
|
Disadvantages |
|
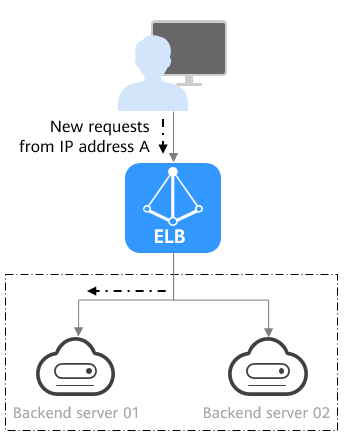
Figure 3 shows an example of how requests are distributed using the source IP hash algorithm. Two backend servers are in the same AZ and have the same weight. If backend server 01 has processed a request from IP address A, the load balancer will route new requests from this IP address to backend server 01.
|
Description |
The source IP hash algorithm calculates the source IP address of each request and routes requests from the same IP address to the same backend server. |
|---|---|
|
When to Use |
This algorithm is often used for applications that need to maintain user sessions or state.
|
|
Disadvantages |
|
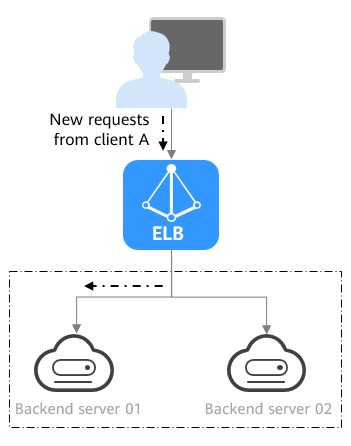
Figure 4 shows an example of how requests are distributed using the connection ID algorithm. Two backend servers are in the same AZ and have the same weight. If backend server 01 has processed a request from client A, the load balancer will route new requests from client A to backend server 01.
|
Description |
The connection ID algorithm calculates the QUIC connection ID and routes requests with the same hash value to the same backend server. A QUIC ID identifies a QUIC connection. This algorithm distributes requests by QUIC connection. You can use this algorithm to distribute requests only to QUIC backend server groups. |
|---|---|
|
When to Use |
This algorithm is typically used for QUIC requests.
|
|
Disadvantages |
|
Changing a Load Balancing Algorithm
The new load balancing algorithm is applied immediately and will be used to route requests over new connections. The previous load balancing algorithm is still be used to route requests over established connections.
- Go to the backend server group list page.
- In the backend server group list, locate the target backend server group and click Edit in the Operation column.
- In the Modify Backend Server Group dialog box, change the load balancing algorithm.
- Click OK.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.