Changing the Protection Action of an Intrusion Prevention Rule
For rules in the basic protection rule library and the virtual patch rule library, you can change their protection actions. The actions you set will prevail and not be affected by the IPS protection mode.
If the rules in the rule library cannot meet your requirements, you can customize IPS signature rules. For details, see Adding a Custom IPS Signature.
Constraints
- The action of a manually modified rule remains unchanged even if Protection Mode is changed.
- The constraints on manually modified actions are as follows:
- The actions of up to 3000 rules can be manually changed to Observe.
- The actions of up to 3,000 rules can be manually changed to Intercept.
- The actions of up to 128 rules can be manually changed to Disable.
Default Actions of Rule Groups in Different Protection Modes
|
- |
Observe Mode |
Intercept mode - strict |
Intercept mode - medium |
Intercept mode - loose |
|---|---|---|---|---|
|
Observe rule group |
Observe |
Disable |
Disable |
Disable |
|
Strict rule group |
Observe |
Intercept |
Disable |
Disable |
|
Medium rule group |
Observe |
Intercept |
Intercept |
Disable |
|
Loose rule group |
Observe |
Intercept |
Intercept |
Intercept |
- Observe: No rules are enabled. The firewall records the traffic that matches the current rule in Attack Event Logs and does not block the traffic.
- Intercept: Rules are enabled. The firewall records the traffic that matches the current rule in Attack Event Logs and blocks it.
- Disable: Rules are disabled. The firewall does not log or block the traffic that matches the current rule.
Modifying the Action of a Basic Protection Rule
- The actions of up to 3000 rules can be manually changed to Observe.
- The actions of up to 3,000 rules can be manually changed to Intercept.
- The actions of up to 128 rules can be manually changed to Disable.
- Log in to the CFW console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - (Optional) Switch to another firewall instance. Select a firewall from the drop-down list in the upper left corner of the page.
- In the navigation pane, choose .
- Ensure Basic Protection is enabled.
- Click View Effective Rules under Basic Protection.
- (Optional) To view the parameter details of a type of rules, set filter criteria in the input box above the list.
- In the basic protection rule list, click an action in the Operation column as needed.
- Observe: The firewall logs the traffic that matches the current rule and does not block the traffic.
- Intercept: The firewall logs and blocks the traffic that matches the current rule.
- Disable: The firewall does not log or block the traffic that matches the current rule.
Figure 1 Changing the current action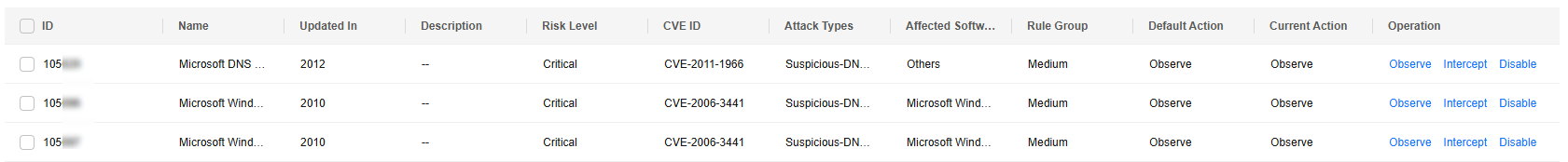
The action of a manually modified rule remains unchanged even if Protection Mode is changed. To restore the default action, select a rule and click Restore Default.
References
- Restoring the default actions of some rules: On the Basic Protection tab, select rules and click Restore Default above the list.
- Restoring the default actions of all rules: On the Basic Protection tab, select rules and click Restore All Defaults above the list.
- For details about how to set the overall IPS protection action, see Configuring Basic IPS Protection.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






