Scenario
This section uses a basic database username and its password as an example to describe how CSMS works.
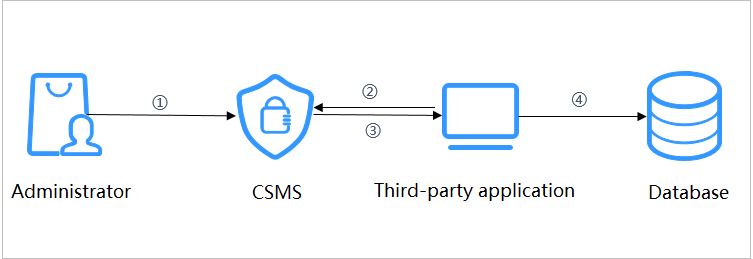
The administrator saves and updates secret values. The user obtains the required secret value through third-party application services. For details, see Figure 1.
The procedure is as follows:
- Create a secret on the console or via an API to store database information (such as the database address, port, and password).
- Use an application to access the database. CSMS will query the secret that the administrator created in Step 1.
- CSMS retrieves and decrypts the secret ciphertext, and securely returns the information stored in the secret to the application through the secret management API.
- The application obtains the decrypted plaintext secret and uses it to access the database.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.