Scenario
After a Dedicated HSM instance is purchased, you can use the UKey provided by DHSM to initialize and manage the instance. You can fully control the key generation, storage, and access authentication.
You can use Dedicated HSM to encrypt your service systems (including encryption of sensitive data, payment, and electronic tickets). Dedicated HSM helps you encrypt enterprise sensitive data (such as contracts, transactions, and SNs) and user sensitive data (such as user ID numbers and mobile numbers), to prevent hackers from cracking the network and dragging the database, which may cause data leakage, and prevent illegal access to or tampering with data by internal users.
You need to deploy the Dedicated HSM instance and service system in the same VPC and select proper security group rules. If you have any questions, contact technical support.
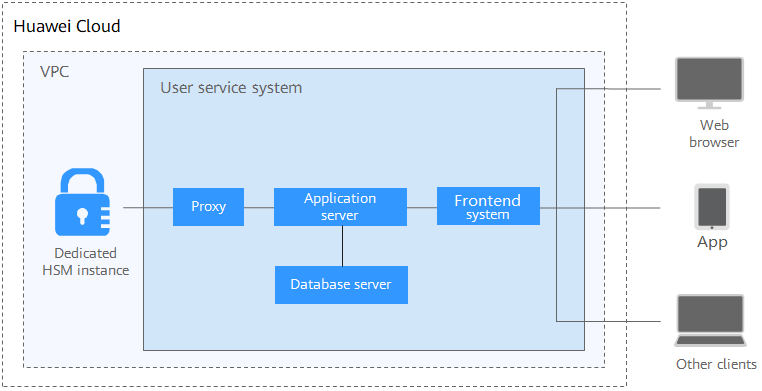
Sensitive Data Encryption
Government public services, Internet enterprises, and system applications that contain immense sensitive information
Data is the core asset of an enterprise. Each enterprise has its core sensitive data. Dedicated HSM provides integrity check and encrypted storage for sensitive data, which effectively prevents sensitive data from being stolen or tampered with, and prevents unauthorized access.
Finance
System applications for payment and prepayment with transportation card, on e-commerce platforms, and through other means
Dedicated HSM can ensure the integrity and confidentiality of payment data during transmission and storage, and ensure the payment identity authentication and the non-repudiation of payment process.
Verification
Transportation, manufacturing, and healthcare
DHSM can ensure the confidentiality and integrity of electronic contracts, invoices, insurance policies, and medical records during transmission and storage.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






