Updated on 2025-12-23 GMT+08:00
How Do I Obtain an AK/SK Pair?
An access key ID and secret access key (AK/SK) constitute an access key.
- AK: access key ID, which is a unique identifier used in conjunction with a secret access key to sign requests cryptographically.
- SK: secret access key used in conjunction with an AK to sign requests cryptographically. It identifies a request sender and prevents the request from being modified.
Obtain and use the AK/SK pair of a public account.
- Each user can create up to two AK/SK pairs. Once they are generated, they are permanently valid.
- Ensure that the public account and AK/SK pair will not be deleted or disabled. If the AK/SK pair is deleted, ICAgent cannot report data to LTS.
Creating an Access Key
- Log in to Huawei Cloud and click Console in the upper right corner.
Figure 1 Accessing the console

- On the management console, hover over the username in the upper right corner and choose My Credentials from the drop-down list.
Figure 2 Choosing My Credentials

- Choose Access Keys from the navigation pane.
- Click Create Access Key.
If operation protection is enabled, you (the administrator) need to enter a verification code or password for identity authentication when creating an access key.Figure 3 Creating an access key
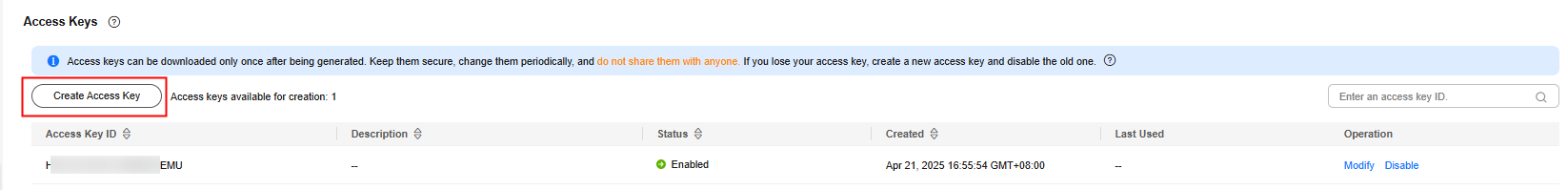
- You can create a maximum of two access keys. The quota cannot be increased. If you already have two access keys, you can only delete an access key and create a new one.
- To change an access key, delete it and create a new one.
- For newly created access keys, the last used time is the same as the creation time, but will change the next time you use them.
- Download the access key file.
After the access keys are created, view the access key ID (AK) in the access key list and view the secret access key (SK) in the downloaded CSV file.
- Download the access key file and keep it properly. If the download page is closed, you will not be able to download the access key. However, you can create a new one.
- Open the CSV file in the lower left corner, or choose Downloads in the browser and open the CSV file.
- Keep your access keys secure and change them periodically for security purposes. To change an access key, delete it and create a new one.
Parent topic: Host Management
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.
The system is busy. Please try again later.






