Checking and Handling Suspicious Processes
Scenarios
If a new application process is started after application process control was enabled, HSS will display it in the suspicious process list. In this case, determine whether the process can be trusted. If it is a normal process, add it to the process whitelist.
Checking and Handling Suspicious Processes
- Log in to the HSS console.Log in to the management console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project.
- In the navigation tree, choose Server Protection > Application Process Control.
- Click the Suspicious Processes tab.
Figure 1 Viewing suspicious processes
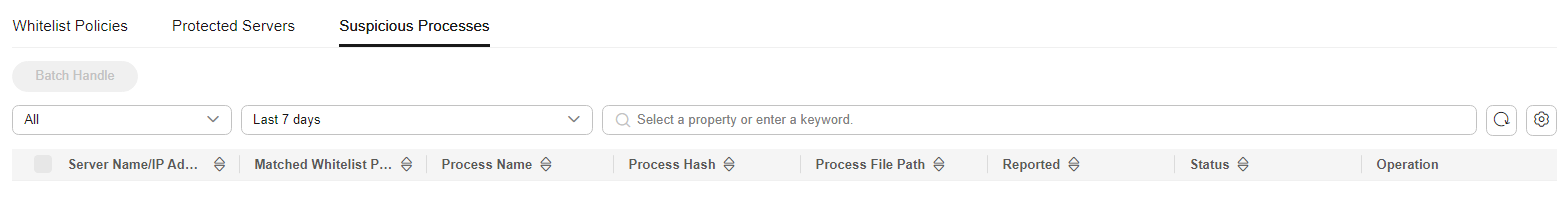
- Determine whether a suspicious process can be trusted based on its information, such as the hash value and file path.
- If the process can be trusted, go to 6.
- If the process cannot be trusted, manually clear it.
- In the row of a process, click Handle in the Operation column.
You can also select multiple suspicious processes and click Batch Handle above the list.
- In the dialog box that is displayed, select an action.
Select Add to process whitelist.
- Click OK.
Related Operations
HSS reports an alarm once it detects a running malicious process. Choose , check and handle the alarms on the Server Alarms tab page, and clear malicious processes in a timely manner. For details, see Handling Server Alarms.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






