Intrusion Prevention Overview
Intrusion Prevention System (IPS) detects intrusion behavior based on the attack signature database and takes measures to block the intrusion in real time. CFW intrusion prevention can detect and block malicious traffic, including hacker attacks, vulnerability exploits, brute-force attacks, worms, mining programs, and Trojans in real time based on the experience and rules accumulated over the years. It helps you build a comprehensive cloud service security system, protecting enterprise core data and key services from unauthorized access, data leakage, and service interruptions.
Why Do We Need Intrusion Prevention?
Intrusion prevention is a necessary defense method to cope with the complex network threats. It largely reduces the intrusion risks for enterprises through real-time, intelligent threat blocking. The reasons for using IPS are as follows:
- Defending against diverse complex network attacks
Network threats have evolved from simple viruses to complex advanced persistent threats (APTs) and zero-day vulnerability exploits. Traditional firewalls and antivirus software cannot effectively defend against these advanced threats. Common means of attacks are as follows:
- Malware attacks: Viruses, Trojans, ransomware, worms, or other malware attack cloud servers, often after they were unintentionally downloaded to the servers by users.
- Port scans and brute-force attacks: Attackers deploy scan systems to scan servers worldwide for open ports, and attempt to guess the username and password by brute-force attacks to obtain unauthorized access. Attackers may also deploy Trojans, download mining programs, or ransomware on victims' servers.
- Web vulnerability exploits: SQL injections, XSS attacks, CSRF attacks, and RCE vulnerabilities are included. Attackers exploit vulnerabilities in applications or websites to access target systems, tamper with data, or steal information.
- Layer-4 vulnerability exploits: The attacks exploiting layer-4 network protocol vulnerabilities are included.
- Database attacks: The attacks on databases such as Redis and MySQL are included.
- Command executions and reverse shells: Attackers run malicious commands and reverse shells to obtain unauthorized access permissions.
To cope with these threats, enterprises need to build a multi-layer security system. By deploying intelligent cloud firewalls, optimizing network access control policies, and establishing a quick vulnerability response mechanism, enterprises can comprehensively improve the security and stability of their business systems.
- Huawei Cloud CFW IPS capabilities
Huawei Cloud CFW IPS provides the following capabilities to enhance and facilitate protection on enterprise cloud services:
- CFW IPS has preconfigured rules that were developed based on the defense experience of the cloud platform accumulated over the years. They help to defend against common network attacks and are continuously updated to protect assets.
- CFW IPS monitors network traffic in real time. It proactively identifies and blocks network attacks, such as SQL injections and cross-site scripting (XSS), through packet inspection and behavior analysis.
- CFW IPS allows you to create custom network intrusion signatures. CFW checks data flows for threats based on the signatures.
- CFW IPS defends against sensitive directory scan attacks. After this function is enabled, the service can block scan attacks.
- CFW IPS defends against reverse shell attacks. After this function is enabled, the service can block reverse shells.
CFW IPS Process
If protection is enabled, all network traffic that accesses CFW will be filtered by the CFW ACL engine and IPS engine, and then forwarded or discarded. During a traffic check, CFW identifies protocols and parses content to accurately analyze application layer behaviors. For detected potential threats:
- They are matched with IPS attack signatures and threat intelligence through flow and packet filtering.
- They are handled based on the preset protection mode (observation, lenient interception, medium interception, or strict interception).
- Malicious traffic is blocked or allowed in real time, in strict compliance with the IPS rule library.
In this way, attacks can be reported and blocked in every stage of the process from protocol identification and threat detection to real-time blocking. The process is as follows:
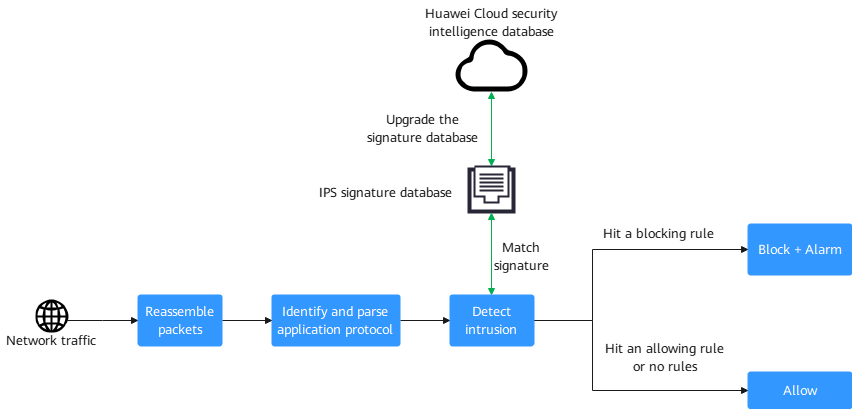
- Packet reassembly: After receiving traffic, CFW reassembles IP fragments and TCP flows to ensure the continuity of application layer data and effectively detect the attacks that bypass intrusion prevention.
- Application protocol identification and parsing: The service identifies the application layer protocol based on the packet content and parses the protocol in depth to extract packet features.
- Signature matching: The service checks parsed packet features against intrusion prevention signatures. If a packet is matched, it is handled based on preset actions. CFW can periodically download the latest intrusion prevention signature databases from the Huawei Cloud security intelligence center to defend against network intrusions.
- Response: After a packet matches a signature, the IPS profile determines whether to respond to the packet and how to process the packet (alarm, block, or allow).
Constraints
- Intrusion prevention does not support decryption detection and defense for TLS- and SSL-encrypted traffic.
- If custom IPS rules have been added, IPS basic protection cannot be disabled.
- If IPS basic protection is disabled, the virtual patch, sensitive directory scan prevention, and reverse shell detection prevention functions will be disabled with it.
Impacts on Services
If IPS blocking is enabled, a range of possible threats and suspicious traffic will be blocked. To change the protection mode, you are advised to enable the Observe mode and check false alarms for a period of time and then switch to the Intercept mode.
Attack Types That Can Be Blocked by CFW
The following table describes the attacks that can be blocked by CFW. For details about how to configure IPS, see Configuring Basic IPS Protection.
|
Attack Type |
Impact |
|---|---|
|
Access control |
In access control attacks, attackers exploit access control vulnerabilities in systems or applications to illegally obtain or elevate their access permissions in the systems or applications, perform unauthorized operations, or access sensitive resources. Access control attacks severely threaten system security. The major impacts are as follows:
|
|
Hacker tool |
A hack tool is a malware program used to launch network attacks. It is usually installed by hackers or malicious programs on victims computers to steal sensitive information, damage the system or network, and remotely control computers or networks. Hacker tools can also be legally used by security researchers to test the security of a system or network. Abuse of hacker tools may bring huge security risks and economic losses to individuals and the society, including but not limited to the following:
|
|
Suspicious DNS activity |
Suspicious DNS activities refer to abnormal DNS requests or responses over the network. Attackers exploit DNS defects or send excessive requests to attack DNS. As a result, the DNS sends abnormal requests or responses, causing domain name resolution errors, resolution timeout, or DNS breakdown. This affects user experience and may also bring serious consequences such as economic losses and even legal liabilities.
Common suspicious DNS activities and their impacts include but are not limited to the following:
|
|
Trojan |
Trojans are a type of malware program that invades a computer to implement illegal intents. Trojans usually disguise as legitimate software and induce users to download them. Attackers use Trojans to control users' computer systems and steal personal information, passwords, or other sensitive data, or damage the computer systems. Common Trojans and their harms include but are not limited to the following:
|
|
Vulnerability exploit |
A vulnerability exploits refer to the behavior that attackers exploit security vulnerabilities in a system, software, or hardware to access the target system without authorization or damage it through well-constructed attack methods to achieve malicious purposes. These vulnerabilities are usually caused by defects in the design, implementation, or configuration process. They provide an opportunity for attackers to bypass security mechanisms. The harms of vulnerability exploits include but are not limited to:
|
|
Worm |
A worm is a type of malware that can replicate itself and spread over the network. It scans for vulnerabilities on the network and exploits these vulnerabilities to infect other servers. Worms can exist and run without depending on other programs. Worms pose serious threats to network security, including but not limited to:
|
|
Reverse shell |
Reverse shells are a covert attack method. An attacker induces the victim server to initiate an outbound connection, bypassing traditional firewall restrictions to establish a remote control channel. Once successful, the attacker can completely control the target system, execute arbitrary commands, steal sensitive data, or implant backdoors. Reverse shells are often disguised as normal network traffic (such as HTTP and DNS) to evade traditional security devices. As a result, they may remain undetected for a long time. Such attacks may cause data leakage, system damage, and bring legal and compliance risks. |
|
Sensitive directory scan |
Sensitive directory scan is a common attack method. Attackers systematically access specific directories on websites or application servers to look for paths that may contain sensitive information or configuration files. In this way, attackers may obtain unauthorized access permissions and sensitive data, such as user information and configuration files. This may also cause server performance deterioration or even service interruption. Sensitive directory scan can also facilitate subsequent attacks, such as system penetration and website content tampering. These can severely harm enterprise security and reputation. |
IPS Protection Modes
IPS can work in observation or interception mode. The mode influences the actions of basic protection rules and virtual patching rules. For example, if Intercept mode-strict is selected, the actions of most basic protection rules and virtual patching rules is Intercept. IPS protection modes are as follows:
- Observe: Attacks are detected and recorded in logs.
- Intercept: Attacks and abnormal IP address access are automatically intercepted.
|
Category |
Scenario |
Description |
Example Value |
|
|---|---|---|---|---|
|
Observe |
No protection. |
Attacks are only recorded in Attack Event Logs and are not blocked. |
Apache Druid remote code execution vulnerability (CVE-2021-25646), VMware Cloud Director remote code execution vulnerability (CVE-2020-3956), and Nero MediaHome DoS vulnerability (CVE-2012-5876) |
|
|
Intercept |
Low |
High-threat and high-certainty attacks are blocked. Select it if you want to minimize false positives. |
Attack characteristics (keywords and parameters) are accurately identified to match specific attack behaviors. No false positives are reported. |
Command execution vulnerability in GNU Bash environment variable processing via DHCP (CVE-2014-6271), Microsoft SharePoint remote code execution vulnerability (CVE-2021-31181), and Delta Electronics DIAEnergie SQL injection vulnerability (CVE-2022-26013) |
|
Medium |
It meets protection requirements in most scenarios and is suitable for routine O&M. |
Multiple types of attacks are covered, and multiple vulnerability analysis methods are integrated. In most cases, no false positives are reported. |
Apache Commons Text remote code execution vulnerability (CVE-2022-42889), Apache Commons Text remote code execution vulnerability (CVE-2022-42889), and Apache Flink remote code execution vulnerability |
|
|
High |
All the identified attack requests are blocked. Select it if you want to avoid false negatives. |
Most high-risk vulnerabilities, such as stack overflow and buffer overflow, are layer-4 vulnerabilities. They need to be identified by analyzing protocols, matching keywords, and checking redirections and keyword offset. |
Schneider Electric C-Bus directory traversal vulnerability (CVE-2021-22717), Apache SkyWalking GraphQL SQL injection vulnerability (CVE-2020-9483), and suspicious Trojan communication |
|
Default actions of rule groups in different protection modes
|
Rule Group |
Observe |
Intercept mode - strict |
Intercept mode - medium |
Intercept mode - loose |
|---|---|---|---|---|
|
Observe rule group |
Observe |
Disable |
Disable |
Disable |
|
Strict rule group |
Observe |
Intercept |
Disable |
Disable |
|
Medium rule group |
Observe |
Intercept |
Intercept |
Disable |
|
Loose rule group |
Observe |
Intercept |
Intercept |
Intercept |
|
The protective actions are as follows:
|
||||
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






