Configuring Interconnection between MRS Hive and External LDAP
Scenarios
This topic describes how Hive connects to an external LDAP server and accesses HiveServer.
In security mode, a client application needs to pass identity authentication before accessing any resource in the cluster and establish a secure session link to manage access control permissions on data and resources in the cluster.
MRS uses KrbServer to provide Kerberos authentication for all components.
LdapServer supports Lightweight Directory Access Protocol (LDAP) and provides the capability of storing user and user group data for Kerberos authentication.
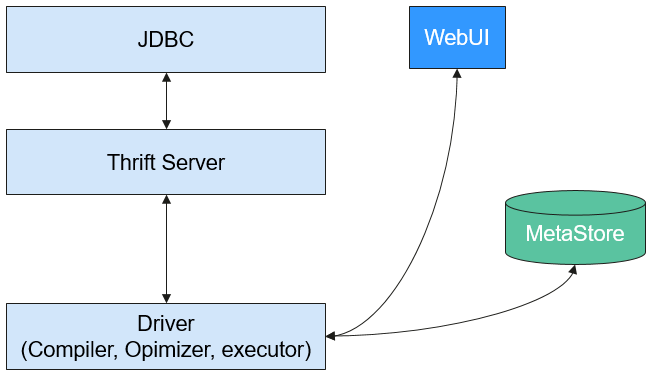
Solution Architecture
Hive is a data warehouse built on Hadoop. It provides batch computing capability for the big data platform and is able to batch analyze and summarize structured and semi-structured data for data calculation. Hive operates structured data using Hive Query Language (HQL), a SQL-like language. HQL is automatically converted into MapReduce tasks for the query and analysis of massive data in the Hadoop cluster.
Hive is able to:
- Analyze massive structured data and summarize analysis results.
- Allow complex MapReduce jobs to be compiled in SQL languages.
- Support flexible data storage formats, including JavaScript object notation (JSON), comma-separated values (CSV), TextFile, RCFile, SequenceFile, and ORC.
Hive functions as a data warehouse based on HDFS and MapReduce architecture and translates HQL statements into MapReduce jobs or HDFS operations.
Constraints
- You have created a user same as that in LDAP on the System > Permission > User page of FusionInsight Manager. The user is added to the hive and hadoop user groups. It is used for HiveServer health check.
- This section applies to MRS 3.1.0 and later versions.
Step 1: Configure LDAP Authentication
- Log in to FusionInsight Manager and choose Cluster > Services > Hive. Click Configurations then All Configurations, click HiveServer(Role) > Security, and search for and modify the following parameters.
Table 1 LDAP authentication parameters Parameter
Description
Example Value
hive.server2.authentication
Authentication mode of HiveServer. The value can be KERBEROS or LDAP. Set it to LDAP.
LDAP
hive.server2.authentication.ldap.baseDN
Base DN of the LDAP service user.
-
hive.server2.authentication.ldap.password
Password of the user created in Constraints with the same username as that in LDAP. This password is used for HiveServer health check.
-
hive.server2.authentication.ldap.url.ip
LDAP IP address.
-
hive.server2.authentication.ldap.url.port
LDAP port number. The default value is 389.
389
hive.server2.authentication.ldap.userDNPattern
Mode list used for searching for user DNs in this directory. If there are multiple modes, separate them with colons (:).
cn=%s,ou=People1,dc=huawei,dc=com: cn=%s,ou=People2,dc=huawei,dc=com
hive.server2.authentication.ldap.username
Password of the user created in Constraints with the same username as that in LDAP. This password is used for HiveServer health check.
-
- Click Save in the upper left corner. In the displayed dialog box, click OK.
- In the Instances tab, select the instances whose configuration status is Expired, click More, and select Restart Instance to restart the affected Hive instances.
Step 2: Access the HiveServer
If LDAP authentication is enabled, the LDAP username and password are required for accessing HiveServer. Run the following command on the Hive client node to connect to HiveServer:
beeline -u "jdbc:hive2://${hs_ip}:${hs_port}" -n ${user} -p ${password}
The relevant parameters are as follows:
- ${user}: LDAP username for accessing HiveServer
- ${password}: LDAP user password for accessing HiveServer
- ${hs_ip}: service IP address of the node where the HiveServer instance is deployed in the MRS cluster. To view the IP address, log in to FusionInsight Manager and choose Cluster > Services > Hive > Instances.
- ${hs_port}: port number of HiveServer in the MRS cluster. You can obtain the port number by running the following command on any node where the HiveServer instance is deployed:
grep -A 1 'hive.server2.thrift.port' ${BIGDATA_HOME}/FusionInsight_HD_*/*_HiveServer/etc/hive-site.xml | grep 'value' | awk -F'[<>]' '{print $3}'
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






