Modifying WTP Configuration
Scenarios
You can modify configuration after WTP is enabled.
You can perform the following operations:
- Manage protected directories: Add, modify, or delete protected directories.
- Configure scheduled protection: Configure when to enable and disable static WTP. While WTP is disabled, you can update and release web pages. This feature is optional.
- Enable and disable dynamic WTP: Enable dynamic WTP to protect Tomcat web pages on Linux servers. It can detect and block the tampering with dynamic data, such as database data, in real time. Currently, dynamic WTP can protect Tomcat applications using JDK 8, JDK 11, and JDK 17.
- Configure privileged processes: After static WTP is enabled, the files and folders in protected directories are set to read-only and cannot be modified. You can configure privileged processes to modify them. This feature is compatible with Linux and Windows. For Linux, only the distributions using kernel versions 5.10 or later are supported.
Modifying WTP Settings
- Log in to the HSS console.Log in to the management console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane, choose Server Protection > Web Tamper Protection.
Figure 1 Web tamper protection
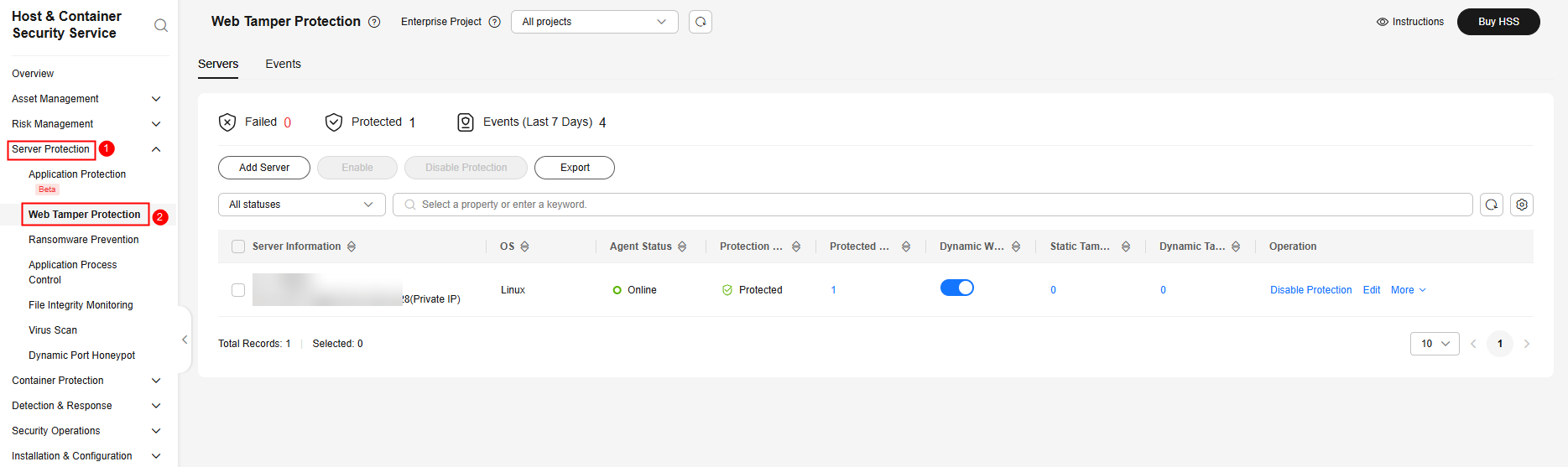
- In the Operation column of a server, click Edit.
- On the Edit page, modify the WTP configuration.
- Manage protected directories
You can add, modify, and delete protected directories.
- Modify a protected directory
On the Edit page, you can modify excluded file types and protection modes. To modify the directory, excluded subdirectories, excluded file paths, and local backup paths of a protected directory, click Edit in its Operation column. For details, see Table 1.
- Delete a protected directory
If a directory no longer needs protection, click Delete in its Operation column.
- Add a protected directory
Click Add Protected Directory. In the dialog box that is displayed, enter directory information and click OK. For details, see Table 1.
- Modify a protected directory
- Configure scheduled protection
Configure when to enable and disable static WTP. While WTP is disabled, you can update and release web pages. Exercise caution when you configure this parameter, because files will not be protected in those periods.
 : Scheduled protection is enabled.
: Scheduled protection is enabled. : Scheduled protection is enabled. You need to configure Unprotected Time Range and Unprotected Days of a Week. For details, see Table 2.
: Scheduled protection is enabled. You need to configure Unprotected Time Range and Unprotected Days of a Week. For details, see Table 2.
Table 2 Scheduled protection parameters Parameter
Description
Example Value
Unprotected Time Range
A time range when WTP is disabled within a day, for example, 10:05 to 15:35.
Requirements:
- A time range must be at least 5 minutes.
- Time ranges (except for those starting at 00:00 or ending at 23:59) cannot overlap and must have at least a 5-minute interval.
- All time ranges are subject to the system time of the server.
10:05-15:35
Unprotected Days of a Week
Static WTP is automatically disabled on specified days of a week, for example, Wednesday and Thursday.
Wednesday
- Enable and disable dynamic WTP
Enable dynamic WTP to protect Tomcat web pages on Linux servers. It can detect and block the tampering with dynamic data, such as database data, in real time.
 : Dynamic WTP is disabled.
: Dynamic WTP is disabled. : Dynamic WTP is enabled. You need to configure the Tomcat bin directory, for example, /usr/workspace/apache-tomcat-8.5.15/bin. The setenv.sh script will be put in the bin directory to configure the startup parameters of the anti-tamper program.
: Dynamic WTP is enabled. You need to configure the Tomcat bin directory, for example, /usr/workspace/apache-tomcat-8.5.15/bin. The setenv.sh script will be put in the bin directory to configure the startup parameters of the anti-tamper program.
- Configure privileged processes
A privileged process is a process authorized to modify a protected directory.
 : Privileged processes are disabled.
: Privileged processes are disabled. : Privileged processes are enabled. You need to configure Process File Path and Trust Subprocess. For details, see Table 3.
: Privileged processes are enabled. You need to configure Process File Path and Trust Subprocess. For details, see Table 3.
Table 3 Privileged process parameters Parameter
Description
Example Value
Process File Path
Set one or multiple complete file paths of privileged processes. Example:
- Linux: /Path/Software.type
- Windows: C:\Path\Software.type
Put each privileged process file path on a separate line. Up to 10 privileged processes are allowed.
/Path/Software.type
Trust Subprocess
If Trust Subprocess is enabled, HSS will trust all the subprocesses up to five levels deep in the subdirectories of specified directories, and allow the subprocesses to modify protected directories. Subprocesses can modify protected directories.
Enabled
- Manage protected directories
- Confirm the settings. On the Edit page, click OK.
After dynamic WTP is enabled for a server, restart Tomcat to apply this setting.
- Verify the change.
- Protected Directory
In the Protected Directories column of a server, click the number view details.
If the information about the protected directory is correct and the Protection Status is Protected, the directory is successfully added or modified.
If the deleted protected directory is not displayed in the list, its deletion is successful.
- Scheduled protection
Modify the web page in the specified unprotected period. If it can be modified, the scheduled protection is configured successfully.
- Dynamic WTP
- Privileged process
If the web page can be modified through a privileged process, the process is successfully configured.
- Protected Directory
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.







