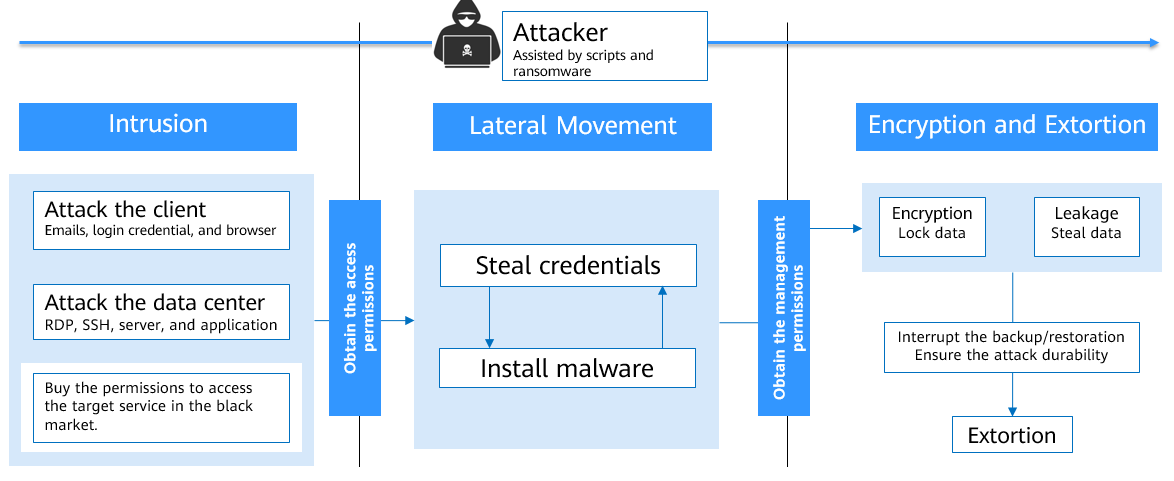
Process of Ransomware Attacks
When attacking cloud infrastructure, attackers usually attack multiple resources in an attempt to obtain access to customer data or company secrets. The process of a ransomware attack can be divided into three stages: investigation and detection, intrusion and lateral movement, and extortion.
- Intrusion: Attackers collect basic information, look for attack vectors, enter the environment, and establish an internal foothold.
- Lateral movement: Attackers deploy attack resources, detect network assets, elevate access permissions, steal credentials, implant ransomware, damage the detection and defense mechanism, and expand the attack scope.
- Encryption extortion: Attackers steal confidential data, encrypt key data, load ransomware information, and ask for ransom.
Figure 1 Extortion process
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






