Generating a Certificate
A partner can purchase certificates issued by commercial CA or use OpenSSL to generate free certificates. There are many OpenSSL commands for generating certificates. This section describes the recommended OpenSSL commands.
- Generate the RSA public-private key pair of CA.
Command: openssl genrsa [-out filename] [-aes256] [numbits]
Example: openssl genrsa -out CAkey.pem -aes256 2048
When the command is executed, a message is displayed on the OpenSSL UI to prompt you to manually enter the password of the generated private key file. The password automatically derives an encryption key and encrypts the private key file.
Table 1 Parameter description Parameter
Description
[-out filename]
Indicates the name and path of the file that stores the public-private key pair.
[-aes256]
Indicates that the encryption algorithm is AES256-CBC.
You can also use other encryption algorithms, such as -des, -des3, -aes128, and -idea. The recommended symmetric encryption algorithms are AES (128 or higher bits). Therefore, AES256 is recommended. If no encryption algorithm is specified in the command for generating the public-private key pair, the generated key-pair file is not protected by the password.
[numbers]
Indicates the length of the generated public-private key pair. The recommended asymmetric encryption algorithm is RSA (2048 bits or higher). Therefore, the recommended length of the public-private key pair has 2048 bits.
- Use the CA private key to perform self signature and generate a root certificate.
Command: openssl req [-x509] [-new] [-key filename] [-out filename] [-md2|-md5|-sha1|-mdc2|-sha256] [-days n] [-config path of openssl.cnf]
Example: openssl req -x509 -new -key CAkey.pem -sha256 -out CA.pem -days 3650 -config openssl.cnf
In the example, Cakey.pem is the private key file generated in 1. When the command is executed, a message is displayed on the OpenSSL UI to prompt you to manually enter the password of the private key file generated in 1 and information of the certificate applicant.
Table 2 Parameter description Parameter
Description
[-x509]
Generates the root CA certificate. The extension item of the certificate is specified in the config file.
[-new]
Generates a new Certificate Secure Request (CSR) file. If this parameter is used together with -x509, a self-signed root certificate file is generated. In this case, you need to enter the necessary information for creating a CSR file. The required information is defined in the config file.
[-key filename]
Indicates the source of the certificate private key file. The format of the file is PKCS#8.
[-out filename]
Generates the certificate request file. If -x509 is specified, a self-signed root certificate file is generated. By default, a standard CSR file is generated.
[-md2|-md5|-sha1|-mdc2|-sha256]
Indicates the hash algorithm of the certificate. It is recommended to use SHA256 in the signature scenario. In addition, because the RSA public-private key pair is generated in 1, the signature algorithm specified here is SHA256RSA.
[-days n]
Indicates the validity period of the certificate with the signature. If this parameter is not specified, the validity period of the generated certificate is 30 days (default). Generally, it is recommended to set the validity period of the generated certificate to 10 years. That is, the value of n is 3650.
[-config path of openssl.cnf]
Indicates the name and path of the openssl.cnf configuration file.
- Generates the public-private key pair of the device certificate.
The command for generating the public-private key pair of the device certificate. The command is the same as that for generating the public-private key-pair of the CA certificate.
Example: openssl genrsa -out Devicekey.pem -aes256 2048
Devicekey.pem is the file that stores the public-private key of the device certificate. When the command is executed, a message is displayed on the OpenSSL UI to prompt you to manually enter the password of the generated private key file. The password automatically derives an encryption key and encrypts the private key file.
- Generates a CSR file of the device certificate.
Command: openssl req [-new] [-key filename] [-out filename] [-config path of openssl.cnf]
Example: openssl req -new -key Devicekey.pem -out DeviceCert.csr -config openssl.cnf
In the example, Devicekey.pem is the private key file generated in 3. When the command is executed, a message is displayed on the OpenSSL UI to prompt you to manually enter the password of the private key file generated in 3 and information of the certificate applicant.
Table 2 describes the parameters.
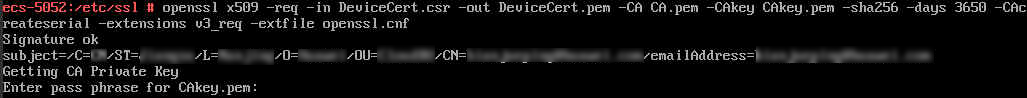
- Use the CA private key to issue the device certificate.
Command: openssl x509 [-req] [-in filename] [-out filename] [-CA filename] [-CAkey filename] [-md2|-md5|-sha1|-mdc2|-sha256] [-days arg] [-CAcreateserial] [-extfile filename] [-extensions v3_req]
Example: openssl x509 -req -in DeviceCert.csr -out DeviceCert.pem -CA CA.pem -CAkey CAkey.pem -sha256 -days 3650 -CAcreateserial -extensions v3_req -extfile openssl.cnf
When the command is executed, a message is displayed on the OpenSSL UI to prompt you to manually enter the password of the CA root private key file generated in 1.
Table 3 Parameter description Parameter
Description
[-req]
Indicates that the input file (the file following the -in parameter) is the CSR file (in x509 commands).
[-in filename]
Indicates the name of the input file. The file is the CSR file of the device certificate generated in 4.
[-out filename]
Indicates the name of the generated file. The file is the device certificate file.
[-CA filename]
Indicates the name of the CA certificate file for signature, that is, the CSR file generated in 2.
[-CAkey filename]
Indicates the CA private key file, that is, the RSA public-private key pair of CA generated in 1.
[-md2|-md5|-sha1|-mdc2|-sha256]
Indicates the hash algorithm of the certificate. It is recommended to use SHA256 in the signature scenario. In addition, because the RSA public-private key pair is generated in 1, the signature algorithm specified here is SHA256RSA.
[-days n]
Indicates the validity period of the certificate with the signature. If this parameter is not specified, the validity period of the generated certificate is 30 days (default). Generally, it is recommended to set the validity period of the generated certificate to 10 years. That is, the value of n is 3650.
[-CAcreateserial]
If there is no CA serial number file (default file name CA.srl), one CA serial number file will be generated. If there is a default CA serial number file, the default file is used. The serial number increases by one every time when a certificate is issued.
[-extfile filename]
Indicates the name of the file containing the certificate extension item. In the example, the file name is openssl.cnf. If this parameter is not specified, the generated certificate does not contain any extension item, that is, the generated certificate is of the x.509 v1 version.
[-extensions section]
Indicates the extended items in the issued certificate file. If this parameter is not specified, the default value is v3_ca, indicating that a CA root certificate is generated. In this example, the device certificate is to be issued. Therefore, the section value is set to v3_req, indicating that the basic constraint of the generated certificate is Subject Type=End Entity (the certificate is a terminal entity certificate).
- The body of the DeviceCert.pem file (excluding the header and tail of the file) generated in 5 is the values of <ds:X509Certificate> </ds:X509Certificate> in Example of the IDP Metadata File (Saved Using UTF-8).
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






