HSTS
HTTP Strict Transport Security (HSTS) is a web security protocol promoted by Internet Engineering Task Force (IETF). HSTS forces clients (such as browsers) to use HTTPS to access your server, improving access security.
Working Principles
If HSTS is configured on CDN, when a client (such as a browser) uses HTTPS to access a CDN PoP for the first time, the PoP responds to the browser with the Strict-Transport-Security header. The browser caches this header if it supports HSTS and uses HTTPS to access CDN PoPs until the cache expires. The structure of the HSTS response header is Strict-Transport-Security:max-age=expireTime [;includeSubDomains]. The following table describes the parameters.
|
Parameter |
Description |
|---|---|
|
max-age |
Validity period of the HSTS header, in seconds. During this period, clients must use HTTPS for access. |
|
includeSubDomains |
(Optional) Enables HSTS for all subdomain names of this domain name. |
Precautions
- HSTS is valid when an international HTTPS certificate is configured.
- Use force redirect to redirect the first HTTP client request to HTTPS.
- To disable the HTTPS certificate, disable HSTS as well.
- When HSTS is enabled and a browser caches the Strict-Transport-Security header, force redirect to HTTP will lead to an infinite loop. As a result, the domain name cannot be accessed.

- To enable HSTS for domain names with special configuration, submit a service ticket.
- HSTS takes effect on clients. After HSTS is disabled, you need to refresh the browser cache. In this way, the next HTTP request from a client will not be automatically redirected to HTTPS.
Procedure
- Log in to the CDN console.
- In the navigation pane, choose .
- In the domain list, click the target domain name or click Configure in the Operation column.
- Click the HTTPS Settings tab.
- In the HSTS area, click Edit.
- Turn on the Status switch and set parameters.
Figure 1 HSTS
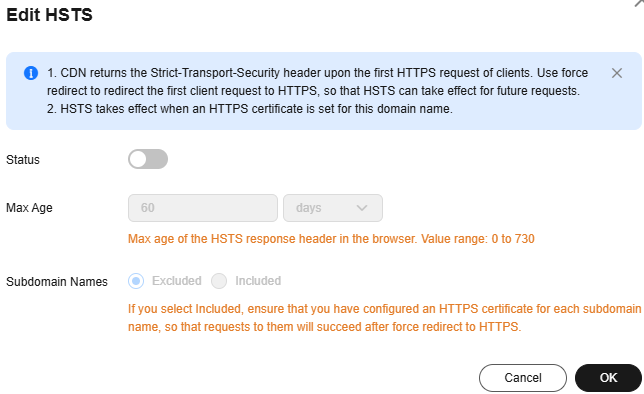
Table 1 Parameters Parameter
Description
Max Age
TTL of the response header Strict-Transport-Security on clients.
- The value ranges from 0 to 63,072,000, in seconds.
- If the TTL is too short, the client cache frequently expires, affecting HSTS. If the TTL is too long and the HTTPS certificate is canceled within the TTL, the domain name cannot be accessed, affecting businesses. The recommended TTL is 5,184,000 seconds, that is, 60 days.
Subdomain Names
Whether to enable HSTS for subdomain names.
- Excluded: HSTS is disabled for subdomain names.
- Included: HSTS is enabled for subdomain names. Check whether HTTPS certificates have been configured for all subdomain names. Subdomain names without a certificate cannot be accessed.
- Click OK.
Examples
Assume that you have configured the following HSTS settings for the domain name www.example.com.

Result:
- When a client uses HTTPS to access the domain name for the first time, the CDN PoP returns the requested content with the Strict-Transport-Security header.
- If the client does not support HSTS, the protocol of client requests to CDN PoPs is not changed.
- If the client supports HSTS, the client caches the Strict-Transport-Security header. When the client accesses the domain name again, the browser automatically converts the HTTP request to an HTTPS request and sends the request to CDN.
- After the browser TTL expires, step 1 is performed again.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






