Using Cascaded Agents to Collect Static Logs from Local Host to HDFS
This section describes how to use Flume to collect static logs from a local host and save them to the /flume/test directory on HDFS.
Prerequisites
- The cluster, HDFS and Flume services, and Flume client have been installed.
- User flume_hdfs has been created, and the HDFS directory and data used for log verification have been authorized to the user.
Procedure
- Generate the certificate trust lists of the server and client of the Flume role respectively.
- Log in to the node where the Flume server is located as user omm. Go to the ${BIGDATA_HOME}/FusionInsight_Porter_xxx/install/FusionInsight-Flume-1.9.0/flume/bin directory.
cd ${BIGDATA_HOME}/FusionInsight_Porter_xxx/install/FusionInsight-Flume-1.9.0/flume/bin
- Run the following command to generate and export the server and client certificates of the Flume role:
The generated certificate is saved in the ${BIGDATA_HOME}/FusionInsight_Porter_xxx/install/FusionInsight-Flume-1.9.0/flume/conf path .
- flume_sChat.jks is the certificate library of the Flume role server. flume_sChat.crt is the exported file of the flume_sChat.jks certificate. -f indicates whether users need to enter the password of the certificate and certificate library.
- flume_cChat.jks is the certificate library of the Flume role client. flume_cChat.crt is the exported file of the flume_cChat.jks certificate. -g indicates whether users need to enter the password of the certificate and certificate library.
- flume_sChatt.jks and flume_cChatt.jks are the SSL certificate trust lists of the Flume server and client, respectively.
Figure 1 Example
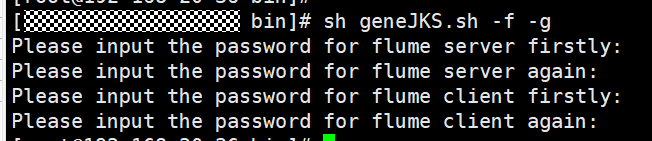
All user-defined passwords involved in this section must meet the following requirements:
- Contain at least four types of the following: uppercase letters, lowercase letters, digits, and special characters.
- Contain at least eight characters and a maximum of 64 characters.
- It is recommended that the user-defined passwords be changed periodically (for example, every three months), and certificates and trust lists be generated again to ensure security.
- Log in to the node where the Flume server is located as user omm. Go to the ${BIGDATA_HOME}/FusionInsight_Porter_xxx/install/FusionInsight-Flume-1.9.0/flume/bin directory.
- On FusionInsight Manager, choose and choose to download the Kerberos certificate file of user flume_hdfs and save it to the local host.
- Configure the server parameters of the Flume role and upload the configuration file to the cluster.
- Log in to any node where the Flume role is located as user omm. Run the following command to go to the ${BIGDATA_HOME}/FusionInsight_Porter_xxx/install/FusionInsight-Flume-1.9.0/flume/bin directory:
cd ${BIGDATA_HOME}/FusionInsight_Porter_xxx/install/FusionInsight-Flume-1.9.0/flume/bin
- Run the following command to generate and obtain Flume server keystore password, trust list password, and keystore-password encrypted private key information. Enter the password twice and confirm the password. It is the password of the flume_sChat.jks certificate library.
./genPwFile.sh
cat password.property
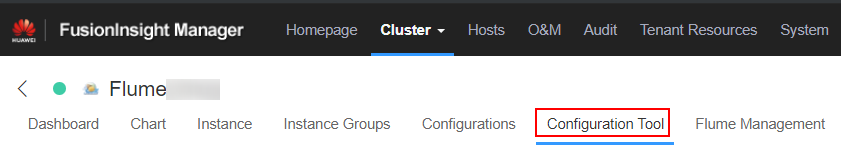
- Use the Flume configuration tool on the FusionInsight Manager portal to configure the server parameters and generate the configuration file.
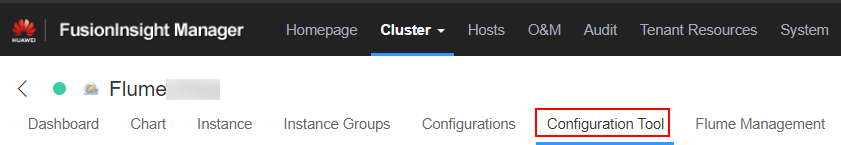
- Log in to FusionInsight Manager and choose Cluster > Name of the desired cluster > Services > Flume > Configuration Tool.
Figure 2 Choosing Configuration Tool
- Set Agent Name to server. Select the source, channel, and sink to be used, drag them to the GUI on the right, and connect them.
For example, use SpoolDir Source, File Channel, and HDFS Sink.
Figure 3 Example for the Flume configuration tool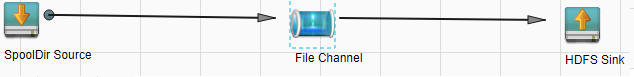
- Double-click the source, channel, and sink. Set corresponding configuration parameters by seeing Table 1 based on the actual environment.
- If the server parameters of the Flume role have been configured, you can choose Cluster > Name of the desired cluster > Services > Flume > Instance on FusionInsight Manager. Then select the corresponding Flume role instance and click the Download button behind the flume.config.file parameter on the Instance Configurations page to obtain the existing server parameter configuration file. Choose Cluster > Name of the desired cluster > Services > Flume > Configuration Tool > Import, import the file, and modify the configuration items related to encrypted transmission.
- It is recommended that the numbers of Sources, Channels, and Sinks do not exceed 40 during configuration file import. Otherwise, the response time may be very long.
- A unique checkpoint directory needs to be configured for each File Channel.
- Click Export to save the properties.properties configuration file to the local.
Table 1 Parameters to be modified of the Flume role server Parameter
Description
Example Value
Name
The value must be unique and cannot be left blank.
test
bind
Specifies the IP address to which Avro Source is bound. This parameter cannot be left blank. It must be configured as the IP address that the server configuration file will upload.
192.168.108.11
port
Specifies the IP address to which Avro Source is bound. This parameter cannot be left blank. It must be configured as an unused port.
21154
ssl
Indicates whether to enable the SSL authentication. (You are advised to enable this function to ensure security.)
Only Sources of the Avro type have this configuration item.
- true indicates that the function is enabled.
- false indicates that the client authentication function is not enabled.
true
keystore
Indicates the server certificate.
${BIGDATA_HOME}/FusionInsight_Porter_xxx/install/FusionInsight-Flume-1.9.0/flume/conf/flume_sChat.jks
keystore-password
Specifies the password of the key library, which is the password required to obtain the keystore information.
Enter the value of password obtained in 3.b.
-
truststore
Indicates the SSL certificate trust list of the server.
${BIGDATA_HOME}/FusionInsight_Porter_xxx/install/FusionInsight-Flume-1.9.0/flume/conf/flume_sChatt.jks
truststore-password
Specifies the trust list password, which is the password required to obtain the truststore information.
Enter the value of password obtained in 3.b.
-
dataDirs
Specifies the directory for storing buffer data. The run directory is used by default. Configuring multiple directories on disks can improve transmission efficiency. Use commas (,) to separate multiple directories. If the directory is inside the cluster, the /srv/BigData/hadoop/dataX/flume/data directory can be used. dataX ranges from data1 to dataN. If the directory is outside the cluster, it needs to be independently planned.
/srv/BigData/hadoop/data1/flumeserver/data
checkpointDir
Specifies the directory for storing the checkpoint information, which is under the run directory by default. If the directory is inside the cluster, the /srv/BigData/hadoop/dataX/flume/checkpoint directory can be used. dataX ranges from data1 to dataN. If the directory is outside the cluster, it needs to be independently planned.
/srv/BigData/hadoop/data1/flumeserver/checkpoint
transactionCapacity
Specifies the transaction size, that is, the number of events in a transaction that can be processed by the current Channel. The size cannot be smaller than the batchSize of Source. Setting the same size as batchSize is recommended.
61200
hdfs.path
Specifies the HDFS data write directory. This parameter cannot be left blank.
hdfs://hacluster/flume/test
hdfs.inUsePrefix
Specifies the prefix of the file that is being written to HDFS.
TMP_
hdfs.batchSize
Specifies the maximum number of events that can be written to HDFS once.
61200
hdfs.kerberosPrincipal
Specifies the Kerberos authentication user, which is mandatory in security versions. This configuration is required only in security clusters.
flume_hdfs
hdfs.kerberosKeytab
Specifies the keytab file path for Kerberos authentication, which is mandatory in security versions. This configuration is required only in security clusters.
/opt/test/conf/user.keytab
NOTE:Obtain the user.keytab file from the Kerberos certificate file of the user flume_hdfs. In addition, ensure that the user who installs and runs the Flume client has the read and write permissions on the user.keytab file.
hdfs.useLocalTimeStamp
Specifies whether to use the local time. Possible values are true and false.
true
- Log in to FusionInsight Manager and choose Cluster > Name of the desired cluster > Services > Flume > Configuration Tool.
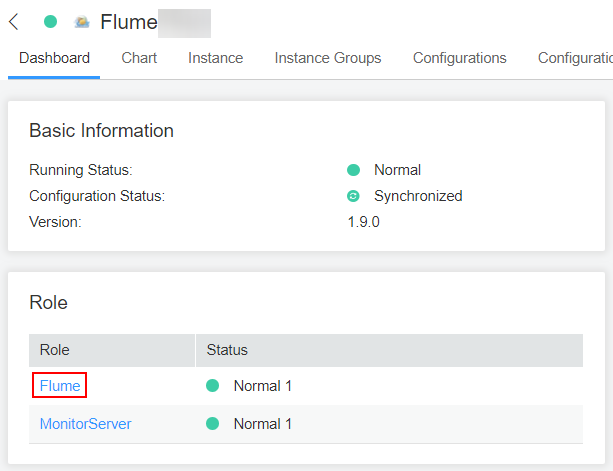
- Log in to FusionInsight Manager and choose Cluster > Name of the desired cluster > Services > Flume. In the Instances tab, click the Flume role whose configuration file is to be uploaded.
Figure 4 Clicking the Flume role
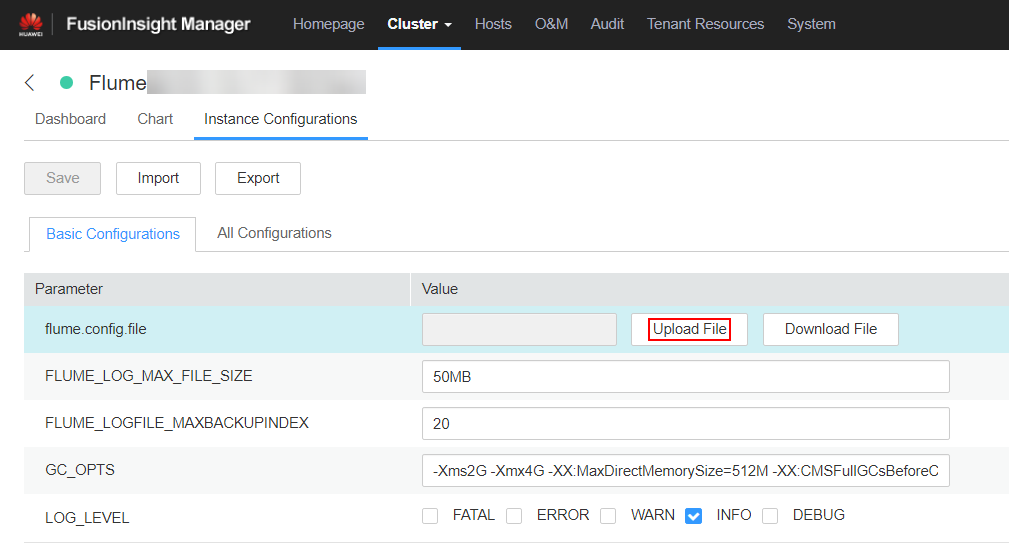
- On the Instance Configurations page, click Upload File next to flume.config.file and select the properties.properties file.
Figure 5 Uploading a file
- An independent server configuration file can be uploaded to each Flume instance.
- This step is required for updating the configuration file. Modifying the configuration file on the background is an improper operation because the modification will be overwritten after configuration synchronization.
- Click Save, and then click OK.
- Click Finish.
- Log in to any node where the Flume role is located as user omm. Run the following command to go to the ${BIGDATA_HOME}/FusionInsight_Porter_xxx/install/FusionInsight-Flume-1.9.0/flume/bin directory:
- Configure the client parameters of the Flume role.
- Run the following commands to copy the generated client certificate (flume_cChat.jks) and client trust list (flume_cChatt.jks) to the client directory, for example, /opt/flume-client/fusionInsight-flume-1.9.0/conf/. (The Flume client must have been installed.) 10.196.26.1 is the service plane IP address of the node where the client resides.
scp ${BIGDATA_HOME}/FusionInsight_Porter_xxx/install/FusionInsight-Flume-1.9.0/flume/conf/flume_cChat.jks user@10.196.26.1:/opt/flume-client/fusionInsight-flume-1.9.0/conf/
scp ${BIGDATA_HOME}/FusionInsight_Porter_xxx/install/FusionInsight-Flume-1.9.0/flume/conf/flume_cChatt.jks user@10.196.26.1:/opt/flume-client/fusionInsight-flume-1.9.0/conf/
When copying the client certificate, you need to enter the password of user user of the host (for example, 10.196.26.1) where the client resides.
- Log in to the node where the Flume client is decompressed as user user. Run the following command to go to the client directory /opt/flume-client/fusionInsight-flume-1.9.0/bin.
cd opt/flume-client/fusionInsight-flume-1.9.0/bin
- Run the following command to generate and obtain Flume client keystore password, trust list password, and keystore-password encrypted private key information. Enter the password twice and confirm the password. The password is the same as the password of the certificate whose alias is flumechatclient and the password of the flume_cChat.jks certificate library.
./genPwFile.sh
cat password.property
If the following error message is displayed, run the export JAVA_HOME=JDK path command.
JAVA_HOME is null in current user,please install the JDK and set the JAVA_HOME
- Run the echo $SCC_PROFILE_DIR command to check whether the SCC_PROFILE_DIR environment variable is empty.
- If yes, run the source .sccfile command.
- If no, go to 4.e.
- Use the Flume configuration tool on FusionInsight Manager to configure the Flume role client parameters and generate a configuration file.
- Log in to FusionInsight Manager and choose Cluster > Name of the desired cluster > Services > Flume > Configuration Tool.
Figure 6 Choosing Configuration Tool
- Set Agent Name to client. Select the source, channel, and sink to be used, drag them to the GUI on the right, and connect them.
Use SpoolDir Source, File Channel, and HDFS Sink.
Figure 7 Example for the Flume configuration tool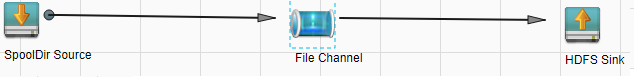
- Double-click the source, channel, and sink. Set corresponding configuration parameters by seeing Table 2 based on the actual environment.
- If the client parameters of the Flume role have been configured, you can obtain the existing client parameter configuration file from client installation directory/fusioninsight-flume-1.9.0/conf/properties.properties to ensure that the configuration is in concordance with the previous. Log in to FusionInsight Manager, choose Cluster > Name of the desired cluster > Services > Flume > Configuration Tool > Import, import the file, and modify the configuration items related to encrypted transmission.
- It is recommended that the numbers of Sources, Channels, and Sinks do not exceed 40 during configuration file import. Otherwise, the response time may be very long.
- Click Export to save the properties.properties configuration file to the local.
Table 2 Parameters to be modified of the Flume role client Parameter
Description
Example Value
Name
The value must be unique and cannot be left blank.
test
spoolDir
Specifies the directory where the file to be collected resides. This parameter cannot be left blank. The directory needs to exist and have the write, read, and execute permissions on the flume running user.
/srv/BigData/hadoop/data1/zb
trackerDir
Specifies the path for storing the metadata of files collected by Flume.
/srv/BigData/hadoop/data1/tracker
batch-size
Specifies the number of events that Flume sends in a batch.
61200
dataDirs
Specifies the directory for storing buffer data. The run directory is used by default. Configuring multiple directories on disks can improve transmission efficiency. Use commas (,) to separate multiple directories. If the directory is inside the cluster, the /srv/BigData/hadoop/dataX/flume/data directory can be used. dataX ranges from data1 to dataN. If the directory is outside the cluster, it needs to be independently planned.
/srv/BigData/hadoop/data1/flume/data
checkpointDir
Specifies the directory for storing the checkpoint information, which is under the run directory by default. If the directory is inside the cluster, the /srv/BigData/hadoop/dataX/flume/checkpoint directory can be used. dataX ranges from data1 to dataN. If the directory is outside the cluster, it needs to be independently planned.
/srv/BigData/hadoop/data1/flume/checkpoint
transactionCapacity
Specifies the transaction size, that is, the number of events in a transaction that can be processed by the current Channel. The size cannot be smaller than the batchSize of Source. Setting the same size as batchSize is recommended.
61200
hostname
Specifies the name or IP address of the host whose data is to be sent. This parameter cannot be left blank. Name or IP address must be configured to be the name or IP address that the Avro source associated with it.
192.168.108.11
port
Specifies the IP address to which Avro Sink is bound. This parameter cannot be left blank. It must be consistent with the port that is monitored by the connected Avro Source.
21154
ssl
Specifies whether to enable the SSL authentication. (You are advised to enable this function to ensure security.)
Only Sources of the Avro type have this configuration item.
- true indicates that the function is enabled.
- false indicates that the client authentication function is not enabled.
true
keystore
Specifies the flume_cChat.jks certificate generated on the server.
/opt/flume-client/fusionInsight-flume-1.9.0/conf/flume_cChat.jks
keystore-password
Specifies the password of the key library, which is the password required to obtain the keystore information.
Enter the value of password obtained in 4.c.
-
truststore
Indicates the SSL certificate trust list of the server.
/opt/flume-client/fusionInsight-flume-1.9.0/conf/flume_cChatt.jks
truststore-password
Specifies the trust list password, which is the password required to obtain the truststore information.
Enter the value of password obtained in 4.c.
-
- Log in to FusionInsight Manager and choose Cluster > Name of the desired cluster > Services > Flume > Configuration Tool.
- Upload the properties.properties file to flume/conf/ under the installation directory of the Flume client.
- Run the following commands to copy the generated client certificate (flume_cChat.jks) and client trust list (flume_cChatt.jks) to the client directory, for example, /opt/flume-client/fusionInsight-flume-1.9.0/conf/. (The Flume client must have been installed.) 10.196.26.1 is the service plane IP address of the node where the client resides.
- Verify log transmission.
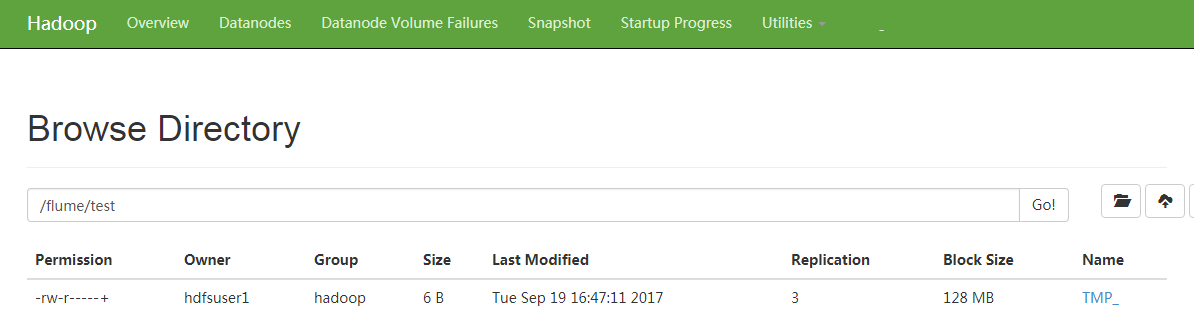
- Log in to FusionInsight Manager as a user who has the management permission on HDFS. For details, see Accessing FusionInsight Manager. Choose Cluster > Name of the desired cluster > Services > HDFS, click the HDFS WebUI link to go to the HDFS WebUI, and choose Utilities > Browse the file system.
- Check whether the data is generated in the /flume/test directory on the HDFS.
Figure 8 Checking HDFS directories and files
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






